Now Available! Critical Start Vulnerability Prioritization – Your Answer to Preemptive Cyber Defense.

Organizations understand that effective vulnerability management is critical to reducing their cyber risk exposure, but many struggle with the overwhelming complexity and effort involved in deciphering and prioritizing vulnerability scan results. That’s why CRITICALSTART® now offers Vulnerability Prioritization as part of our Vulnerability Management and Managed Detection and Response Services.
Vulnerability Prioritization Puts an End to Patching Guesswork
Critical Start Vulnerability Prioritization, which is included with Critical Start’s Vulnerability Management Service or as a standalone tool with Managed Detection and Response, identifies and highlights your high-risk vulnerabilities. By enriching the scan results you already produce from Tenable or Qualys with proprietary calculations that leverage real-time threat intelligence, Vulnerability Prioritization helps you cut through the volume of vulnerabilities so you can patch what matters most first. Then, we go one step further by giving you prescriptive patching guidance, so you’ll know exactly which patches to use.
Intelligence-based and Threat-aware Prioritization
Most security teams lean heavily on CVSS scores and CISA KEV rankings to prioritize vulnerabilities. However, those scores lack the necessary business context and threat intelligence needed to make them timely with current exploits and relevant to your business context. Critical Start’s Vulnerability Prioritization starts with Qualys’s or Tenable’s scan results, and then goes deep, with enrichment based on threat intelligence, exploit weaponization by attack type (ransomware, malware, botnet), asset criticality, and exposure settings due to technical security controls gaps. This allows your teams to focus remediation efforts on the vulnerabilities that pose the greatest risk so you can mitigate the most significant exposures to your organizations.
Made to Help you in your Fight Against Ransomware, Botnets, and More
Even when you have a prioritized list of vulnerabilities, do you know which assets are at risk of exploitation by Ransomware threat actors? Do you know for certain where Botnets might strike? When you first sign into your Vulnerability Prioritization dashboard, you will immediately see where your attack surface is most vulnerable to attacks from these and other high-risk threats. This lets you rapidly shut down possible attack vectors, even during—or before—the news of zero-day events hits the headlines.
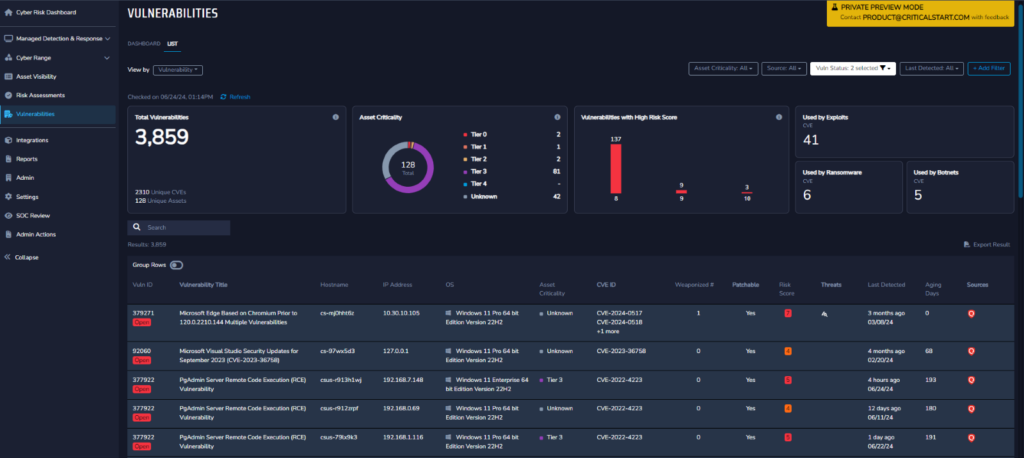
Complete Asset Visibility at Your Fingertips
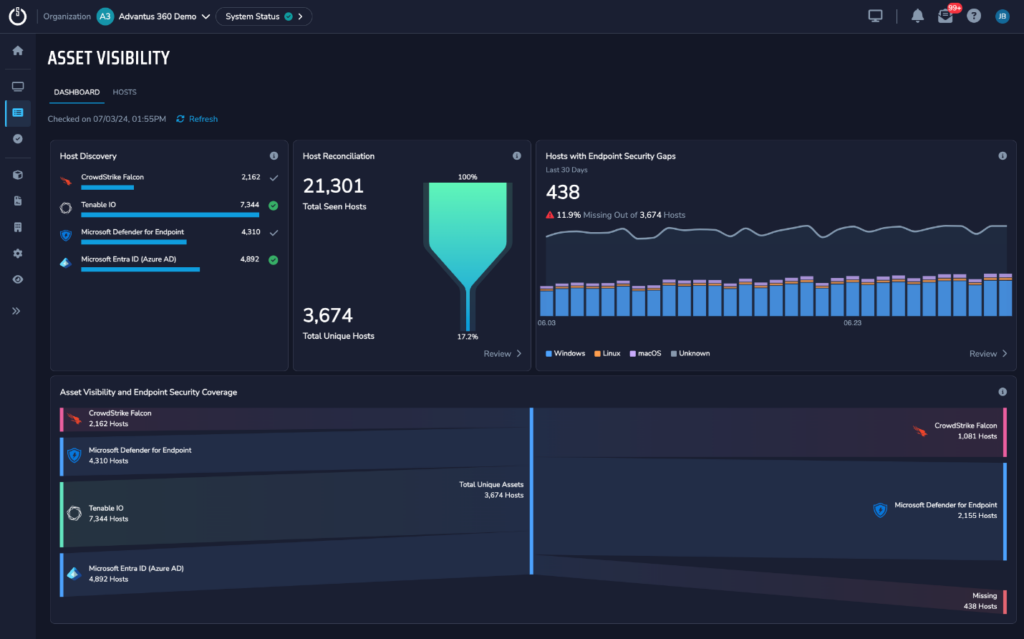
Your security strategy is only as good as the information you’re receiving from your tools. Critical Start’s tools and services, including Vulnerability Prioritization, are underpinned by comprehensive Asset Visibility. This window into your coverage alerts you to assets that lack the agents and scanning they need to keep your organization safe. That way, you can close the gaps and ensure that you’re not missing any assets in your vulnerability scans.
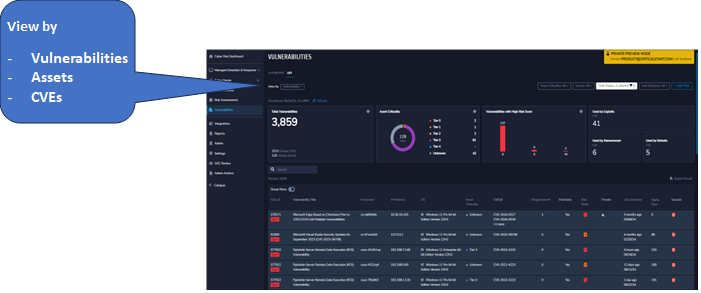
A View for Every Stakeholder
Are you in charge of vulnerability management, needing clear prioritization based on risk score, exploitability, and weaponization? Or are you tasked with remediation or IT asset management, in need of asset views and prescriptive patching guidance? Or is your role compliance or leadership, demanding aging criteria so you can articulate findings and remediation over time? For all these roles and more, Vulnerability Prioritization has views to get the job done.
Read the press announcement
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
