Unknown Risk Acceptance Is Unacceptable: The Danger Lurking Behind the Threat Signals Missed by Your MDR
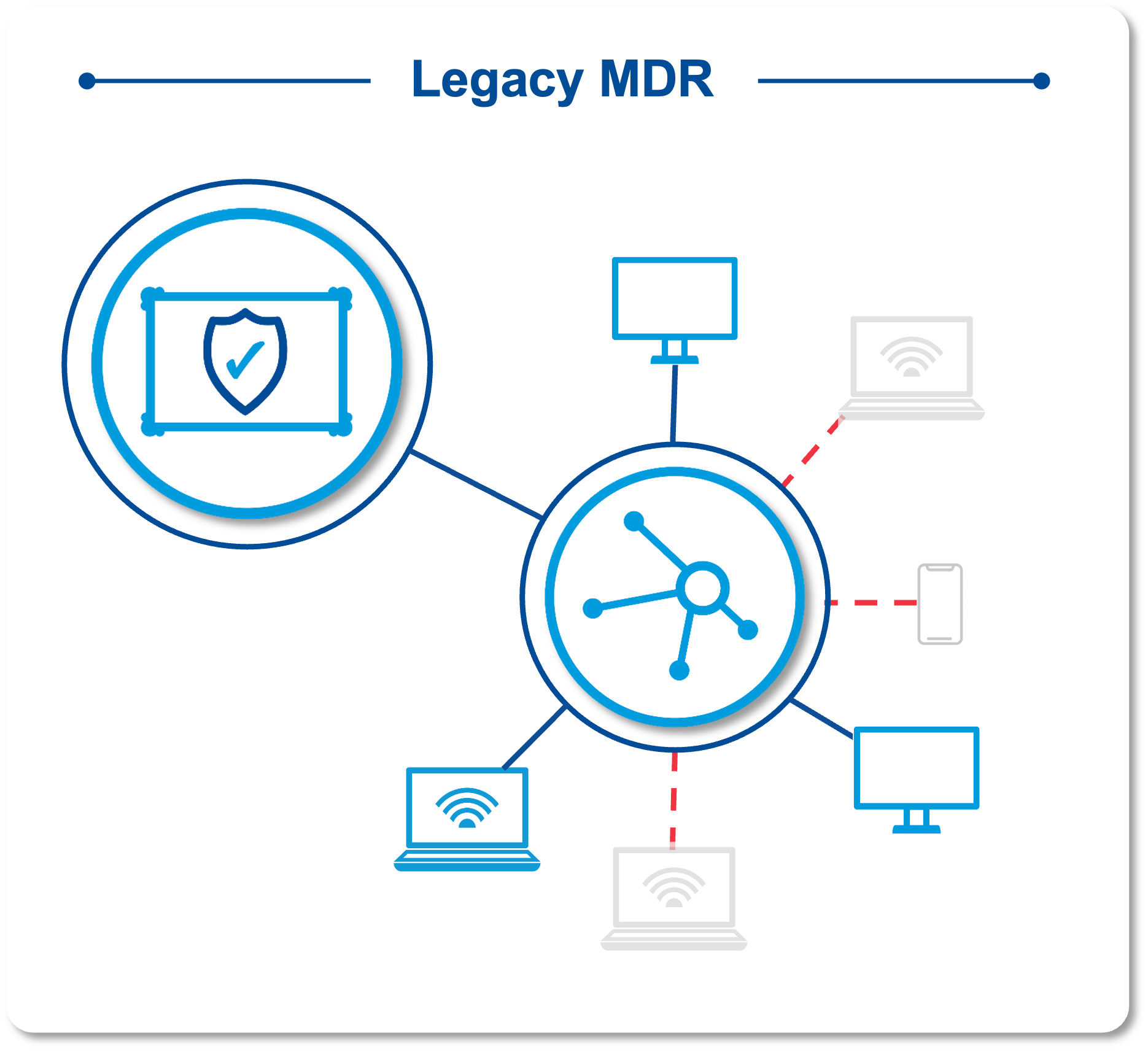
Legacy MDR Fails to Validate Controls Are Working
Recent data from the Ponemon Institute shows that 68% of organizations have experienced one or more successful endpoint attacks—frequently from threat actors exploiting insufficient visibility to gain network access—with 82% of security leaders admitting to being surprised by breaches or threats that had managed to evade security controls they assumed were correctly in place.
Adopting Managed Detection and Response (MDR) and Endpoint Detection and Response/Endpoint Protection Platform (EDR/EPP) together is generally considered one of the more effective cybersecurity approaches to create a robust, in-depth defense strategy that ensures comprehensive threat detection and response capabilities to quickly stop a breach. Yet, without the ability to validate that controls are working, many organizations reliant on MDR services unknowingly operate under a misplaced sense of security.
They assume their MDR is receiving all expected threat signals when, in reality, legacy MDR takes a “see no evil” approach, relying heavily on confirmation of endpoint security coverage based on periodic, manual data collection performed by over-taxed teams with no checks and balances to ensure asset inventory aligns with the threat signals being received.
Endpoint Security Coverage Gaps Force Unnecessary Risk Acceptance
Since an MDR is only as effective as the security signals it receives, this lack of visibility allows coverage blind spots to persist, enabling threats to slip through and exposing organizations to unknown and unacceptable levels of risk acceptance. In fact, only 30% of IT security leaders are highly confident in their endpoint visibility, leaving endpoints like laptops, servers, and mobile assets (which serve as the main entry point for threat actors) open to exploitation and organizations in unnecessary peril.
While there are many reasons endpoint security coverage gaps happen, including:
- Human misconfiguration
- Laptops and desktops
- Misconfigured servers and network equipment, and
- Legacy systems that are no longer supported or cannot run modern endpoint security agents,
the root cause almost always ties back to the lack of an accurate, real-time, and comprehensive view of an organization’s dynamically changing IT ecosystem that only automation can provide. This can be exacerbated by other significant detection obstacles like the:
- Inability to keep pace with the increasing complexity of the threat landscape
- Expanded attack surfaces and unfamiliar assets due to Mergers and Acquisitions (M&A) and new partnerships and
- Gradual configuration drift or changes in the log source schema
An inconsistent EDR/EPP deployment also increases the likelihood of coverage gaps, leading to poor visibility and signal disruption through integration issues, improper configuration, and no validation feedback loops that would verify endpoints are transmitting as expected.
Any gaps in inventory and coverage create critical detection issues, allowing endpoint security coverage gaps to remain invisible and preventing threat signals from being accurately reported and received by the MDR. As a result, when inevitable breaches occur via unprotected endpoints, organizations are left perplexed about how these compromise vectors were overlooked in the first place—leading to paralyzing detriment. Just one endpoint lacking oversight can pose an extreme risk, with research showing the average organization seeing five endpoint attacks in 2022, costing $1.8 million.
The Need for An Evolved MDR With Expanded Visibility
The phrase “evolving threat landscape” is so commonplace it borders on cliché, yet it isn’t without merit. What is concerning is that cybersecurity solutions used to combat those threats don’t have a similar, widely-used phrase to highlight a parallel evolution showing an attempt to stay one step ahead. This is because threat actors will always have the upper hand, with the advantage of hyper agility, leveraging new, covert exploits to evade traditional security measures. As a result, 67% of organizations have experienced a breach despite having threat-based security in place. Clearly, it’s time for an evolved MDR with expanded visibility to help get ahead of attackers who exploit unmanaged endpoints.
Organizations that prioritize risk must now incorporate an MDR service that includes endpoint security coverage monitoring into their security program to mitigate weaknesses in attack surfaces and ensure their Security Operations Center (SOC) receives the expected signals needed for threat identification and containment.
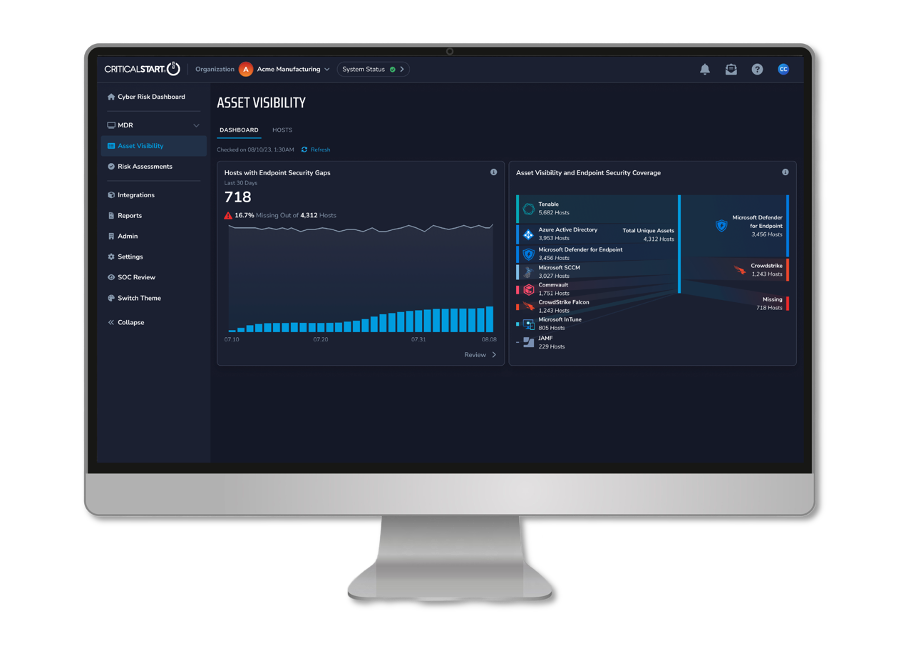
MDR with expanded visibility adds another layer of protection by:
- Identifying previously unknown or unmanaged assets
- Highlighting the level of risk exposure the organization faces due to endpoint security coverage gaps
- Allowing for gap mitigation to reduce the possibility that a threat will be missed, and
- Offering a consolidated view of assets through a normalized asset inventory built from security and asset data sources
Uncovering risks early and closing endpoint security coverage gaps optimizes MDR and enables measurable risk reduction across the organization. When their MDR is receiving all the expected security signals, organizations benefit from:
- Remediation of unprotected assets to prevent breaches
- Faster threat detection and response across endpoints
- Increased confidence in full security coverage, and
- Less distraction for IT and security teams, enabling greater focus on critical tasks
With comprehensive and validated coverage of endpoint security signals, organizations can confidently rely on their MDR for threat protection. Gone are the days of unknown and unnecessary risk acceptance.
Feeding a More Holistic Risk Picture
Closing endpoint visibility gaps provides immense value alone, but the impact compounds when leveraged as part of broader capabilities. Endpoint security gap identification integrates directly with Risk-Ranked Reduction Recommendations, providing more precise and contextual recommendations for the biggest impact to risk.
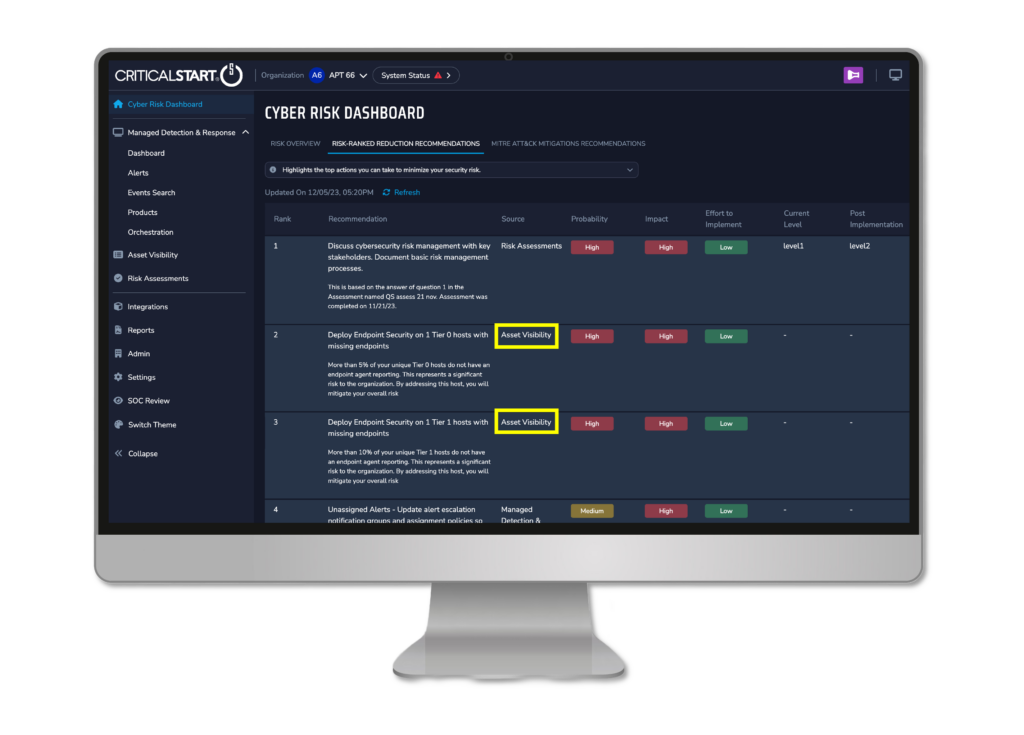
With endpoint coverage gaps data included within Critical Start’s Cyber Risk Dashboard highlighted in the Risk alongside broader risk and security gap information, teams gain a continuously updated, 360-degree view of exposures.
This consolidated cyber risk snapshot, benchmarked against best practices and peer data, empowers smarter decisions through correlated insights. When endpoint risks interplay with network, cloud, or identity risks, the intersecting effects are revealed.
Data-Driven Risk Optimization
With expanded visibility bridging endpoint monitoring gaps and helping to ensure the right controls are in place, organizations can finally include additional proactive, data-driven risk reduction measures in their defense against breaches, including:
- Exposure-focused investments to maximize risk reduction
- Objective validation of control efficacy
- Optimized cyber risk management, tying data to decisions
The result is confidence—and confidence is control. Leaders can pivot decisively to address the most pressing risks with context. They gain an intimate understanding of true exposures now…and what could happen later by continuously assessing changing risk trajectories.
Stop Danger in Its Tracks by Ensuring Controls Are in Place Across Your Endpoints
Traditional methods of accounting for assets like manual audits, periodic scans, and relying on customers to self-report don’t provide the real-time, continuous visibility needed to secure today’s dynamic environments. And an MDR that is limited to protecting only the assets it can see results in its inability to scale and adapt to the dynamic nature of emerging threats.
Without specific capabilities to proactively detect endpoint security coverage gaps, there is a greater likelihood of misplaced confidence, leaving security leaders to mistakenly believe all the threats their MDR should have detected were identified.
The rates of change across IT environments combined with constantly evolving new exploits means security teams can no longer wait for threats to emerge before responding. To get ahead of attackers, organizations need continuous visibility across all endpoints and assurance of full security coverage.
Evolved MDR, with a focus on risk reduction, adds value beyond threat detection and response by bringing visibility to security coverage gaps that would otherwise remain invisible, empowering security leaders with asset visibility and proactive controls to uncover and secure unknown risks in ways that legacy MDR solutions can’t offer and protect organizations now and for the future.
Click here for more information on Critical Start Endpoint Coverage Gaps, or contact an expert to discuss your unique endpoint coverage challenges and needs.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
