Threat Detection and the Pyramid of Pain
By Matthew Herring, Director Cyber Threat & Detection Engineering
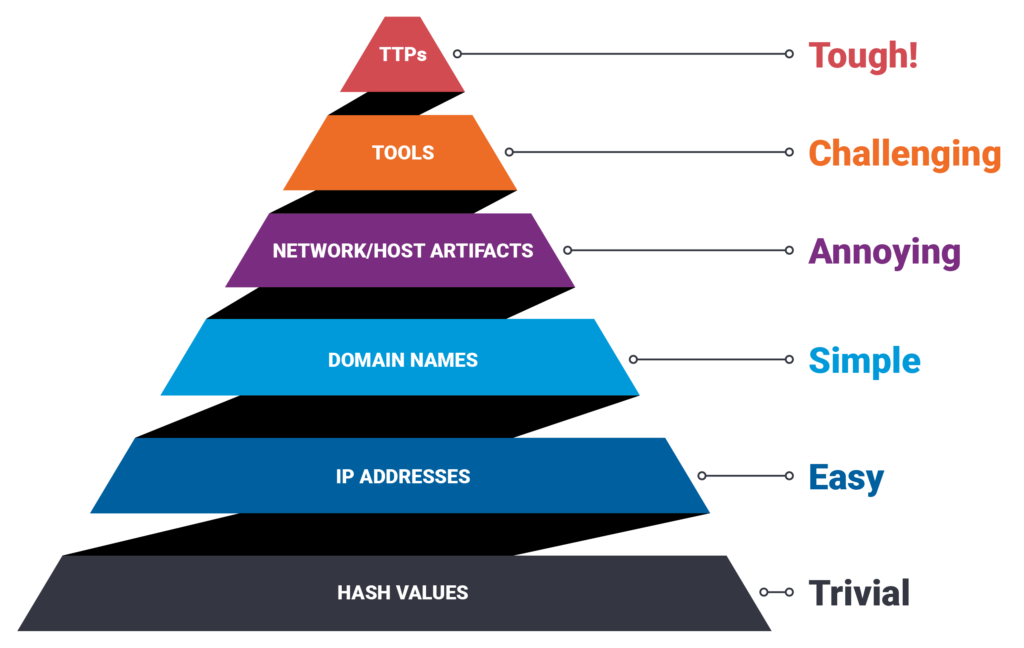
Defense is hard. Like really hard. There’s an old adage that while the adversary has to be right only once, you have to be right 100% of the time to prevent a breach. Good defensive posture requires a significant investment in resources. The cost for software, the talent to manage and operate the software, and then the time and energy spent to ensure that you’re maximizing your investment can add up quickly. Even with well-developed and maintained security tools, it’s difficult to stay on top of the ever-evolving threat landscape. To be effective, you have to maximize your investments to stop attacks before they become a problem. An effective tool for enterprise defenders is the pyramid of pain. Adversaries, just like defenders, are human and operate using a set of playbooks and tactics that have proven effective for them in the past. While the infrastructure the adversaries use to execute their operations are relatively simple to release, disrupting their playbooks can have a significant impact on their ability to succeed in their mission. The premise is simple — the further up the pyramid you go, the more pain you inflict on the adversary.
How does all of this work? Let’s use one of my favorite activities as an example – Barbecue. I’m from Texas, it’s only natural.
- Hash – The wood. Each piece of wood (I prefer post oak and pecan), and while I may look for a specific size, the level of effort to adjust has almost no impact on my ability to make a great meal.
- IP Address – The brand of wood. Can’t find a specific brand of wood to use for cooking? It’s trivial to find another brand of the same type of wood. If someone takes a specific brand of wood away from me, you bet I’m going to do a quick search on Amazon, and I will find several other varieties.
- Domain Names – The type of wood. I have my preferences in wood, and if my preferred isn’t available, it can change the result, but the overall outcome is the same (family and friends fighting off a nap attack after copious amounts of food).
- Host/Network Artifacts – The time and temperature to cook. This starts to get tricky. Everyone has their preferred time and temperature to get optimal results, and if you start to deviate from that, you must make some decisions on how to adjust if you want a good result. There are still methods for adjusting that with a little bit of effort, can still yield the results you’re looking for.
- Tools – Smoker, Torch, Thermometer. I have a set of tools that I use that help me ensure consistent and high quality results. Take away my smoker, thermometer, and torch to light the fire, and now I have some serious problems that I need to account for.
- TTP – I follow a specific playbook when I cook. I need to procure the ingredients. I’ll start the night before. Light the fire, trim the meat, put on the rub, get the smoker to temp, put some water in a pan, put the meat in the smoker, monitor, wrap the meat, pull, rest. What happens if I can’t execute that playbook? Pizza. I’m ordering pizza.
Wrapping it up – what does this mean? As a defender, you should focus building your detections as high up the pyramid of pain as possible to increase your probability of successfully disrupting adversary activity against you. The Critical Start Cyber Response Unit does just that. We leverage our threat intelligence research to power our detection capabilities by focusing not just on the atomic indicators (hashes, IP addresses, Domain Names), but on tools, tactics, techniques and procedures. Using our Threat Navigator, we can determine visibility gaps and quickly identify emerging trends in the threat landscape to fill those gaps to protect our customers. In combination with our Trusted Behavior Registry™ in ZTAP™, we’ve created an industry leading service that resolves every alert, and stops breaches.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
