Shrinking Timelines and Rising Costs: The Dynamics of Ransomware Attacks

Background
The landscape of cybersecurity is undergoing rapid and dynamic changes, driven by the ever-evolving tactics and strategies employed by ransomware threat actors. These malicious actors are not only adapting but also introducing groundbreaking extortion methods that pose new challenges for organizations’ security postures. Furthermore, the latest data and research findings underscore substantial shifts in dwell times – the duration between an initial network breach and its discovery – within compromised networks. This alarming trend emphasizes the critical importance of gaining a deep understanding of these evolving dynamics to effectively combat the growing menace of cyber threats.
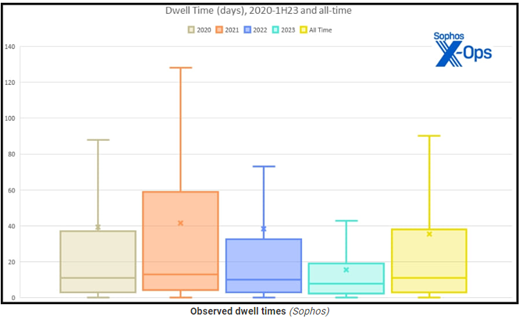
In the first half of 2023, there has been a remarkable reduction in the median dwell time for ransomware attacks, from nine days in 2022 to just five days. This metric signifies how long threat actors remain hidden within compromised networks and underscores the agility of ransomware operators in their pursuit of illicit gains. The group operating “Ransomed” ransomware has gained notoriety for branding their ransom demands as a “Digital Peace Tax,” coercing victims to pay to protect their stolen files or face fines reminiscent of data protection regulations like the European Union’s General Data Protection Regulation (EU’s GDPR). This type of terminology aligns with the unconventional branding tactics seen in the larger ransomware landscape, where groups like LockBit label their operations as a “post-paid penetration testing service.” However, questions linger about the extent of Ransomed’s criminal activities, including whether they actively deploy ransomware or merely make claims about stolen data.
Evolving Threat Landscape
In this dynamic landscape, ransomware attacks have assumed a dominant role, accounting for a staggering 68.75% of all recorded cyberattacks in the current year. As ransomware actors expedite their operations, a different narrative emerges in non-ransomware cyber incidents. The median dwell time for these incidents has extended from 11 to 13 days in 2023, signaling a propensity among other cybercriminals to bide their time and seize opportunities.
Data Exfiltration Trends
An intriguing trend is the increased occurrence of data exfiltration, observed in 43.42% of cases, marking a 1.3% rise from the previous year. This suggests a rising tide of data theft, despite a decrease in the overall number of such attacks—from 42.76% in 2022 to 31.58% in H1 2023. Furthermore, cases confirming no data exfiltration have risen from 1.32% to 9.21%. These shifts underscore the evolving tactics employed by cybercriminals in the digital landscape.
Temporal Patterns and Ransomware Preferences
Exploring the temporal aspects of these attacks unveils intriguing insights. Threat actors, including ransomware operators, target organizations late in the day on Tuesdays, Wednesdays, and Thursdays. These mid-week assaults are strategically timed to capitalize on understaffed IT teams, which are less likely to detect intrusions and threat actor movement. Notably, ransomware incidents peak on Fridays and Saturdays, exploiting the challenge of reaching tech teams and slower response times.
RDP Exploitation and Mitigation Strategies
Remote Desktop Protocol (RDP) remains a favored tool among cybercriminals, implicated in 95% of intrusions. However, it is primarily utilized for internal activity in 93% of cases, with external use occurring in only 18% of instances. Given its prevalence, securing RDP should be a top priority for organizations. Denying unauthorized access via RDP can significantly deter attackers, compelling them to invest more time and effort, thus increasing the likelihood of intrusion detection.
Unprecedented Extortion Tactics
A new ransomware group, operating through the “Ransomed” blog, presents victims with a stark ultimatum: pay to protect their stolen files or face fines resembling data protection regulations, such as the EU’s GDPR. The group follows a common ransomware blog strategy, publicly naming victims and issuing menacing threats to expose sensitive data unless ransoms ranging from $54,000 to $218,000 are paid. These sums are notably lower than authentic GDPR fines, potentially designed to boost victim compliance.
Ransomed’s blog includes several named companies, including the Metropolitan Club, TransUnion, and State Farm, none of them reported recent data breaches. Concerns escalate due to the group’s claim of possessing the source code of Raid Forums, an illicit hacking forum seized last year, suggesting possible transformation into a full-fledged hacker forum, adding to cybersecurity community anxieties.
Proactive Measures and Vigilance
To bolster cybersecurity defenses, organizations are encouraged to retain data for a reasonable period and conduct regular checks. This proactive approach facilitates the identification of threat actors already within the network before they advance to the final stages of an attack. Such data monitoring not only aids in early threat detection but also equips defenders and incident responders with invaluable insights to promptly address emerging issues.
Conclusion
While the legitimacy and real impact of the emerging threat presented by “Ransomed” are still uncertain, their unique extortion techniques introduce a new dimension to cybercriminal tactics. As the cybersecurity landscape continuously evolves, it underscores the need for unwavering vigilance, proactive security measures, and the ongoing adaptation of defense protocols. The decreasing dwell time, increasing data exfiltration, and strategic timing patterns all highlight the rapidly changing nature of cyber threats. In this ever-evolving cybersecurity landscape, it’s crucial for security professionals to maintain vigilance, adjust their strategies, and proactively tackle emerging challenges posed by such resourceful threat actors.
__________________________________________________________________________
CRITICALSTART® offers a pioneering solution to modern organizational challenges in aligning cyber protection with risk appetite through its Cyber Operations Risk & Response™ platform, award-winning Managed Detection and Response (MDR) services, and a dedicated human-led risk and security team. By providing continuous monitoring, mitigation, maturity assessments, and comprehensive threat intelligence research, they enable businesses to proactively protect critical assets with measurable ROI. Critical Start’s comprehensive approach allows organizations to achieve the highest level of cyber risk reduction for every dollar invested, aligning with their desired levels of risk tolerance.
References
- https://news.sophos.com/en-us/2023/08/23/active-adversary-for-tech-leaders/
- https://www.inforisktoday.com/speed-demons-ransomware-attackers-dwell-time-shrinks-a-22906
- https://www.bleepingcomputer.com/news/security/ransomware-hackers-dwell-time-drops-to-5-days-rdp-still-widely-used/
- https://www.cybersecuritydive.com/news/ransomware-attack-dwell-times-sophos/691576/
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
