While Microsoft took a hit to its security reputation with Windows Defender 2016, the Big 5 Technology powerhouse came back strong with a rise in both capabilities and rankings among third parties like Gartner, Forrester and MITRE. With the expanded capabilities coming out of Microsoft Azure Sentinel, Microsoft’s portfolio ties together with additional data feeds to enable customers to detect threats earlier and respond more effectively. It’s why Ann Johnson, CVP of Security Compliance and Identity for Microsoft, was high on our list to interview for the second installment of our Rated XDR series. Listen to the podcast below.
In a review of the top XDR solutions for 2021, Gartner Peer Insights, Microsoft held a 4.5/5 star rating over 158 reviews. Microsoft’s 365 Defender made the Forrester Wave and Gartner Magic Quadrant Leaders in the most recent reviews. In the latest MITRE Carabanak+FIN7 Evaluations for EDR, Microsoft had an overall detection rate of 86.78% between telemetry and analytic detections.
We found Ann’s job title insightful into the new thinking driving the Microsoft approach to security. “When we think about security compliance, identity and management holistically, we don’t think they can be separated,” Ann shared. “With the increase in global regulations and the increase in attacks on our customers, we feel that these ideas need to be operationalized more seamlessly. “We’re certainly seeing a huge push in identity right now as attackers go after credentials to try and take over accounts to leverage for lateral movement. That’s why we’re seeing an effort to pull all these things together.”
Microsoft’s approach has been to build native security capabilities into the solutions they were already offering to their customers. “It’s amazing to see the roadmap that was laid out three years ago and how well it’s been executed,” Ann stated. “If you just think about a recent acquisition, like Risk IQ, we’re going to invest more than a billion dollars in security this year…It’s about understanding the customer’s problems really in depth. We think about outcomes more than we think about tooling.”
Azure Sentinel delivers stronger outcomes through XDR
Ann described how she was sitting in a room with her colleagues several years ago discussing how there needed to be a better way to handle security event management. They decided that there needed to be a cloud-native version of SIEM which was more scalable and automated. Since they didn’t believe this type of tool existed, they decided to build it and make it native to Microsoft Azure. “We didn’t want this to be your traditional SIEM, where a box was checked or something was logged, but no one ever used it to pull data out. We wanted this to be a great data aggregator to give actionable feedback to the SOC that was meaningful, but also to automate as many low-level tasks as we could. There are smart humans are working on hard problems and we’re telling them which hard problems they should tackle first. And it’s all part of the XDR strategy. If you think about Microsoft Defender for Endpoint and Microsoft Defender for Office and Microsoft Defender for Networks and IOT and Azure, they all aggregate to an XDR solution where you can do hunting and forensics within the platform.”
“You should have an EDR capability that ultimately comes into XDR. So that applies whether that’s servers, storage, network, an IOT environment or actual end points—all these different places are where we have Microsoft Defender capabilities today. You have the detection and response capability, but before you even get to Sentinel, you could actually do hunting and forensics. (And at the Sentinel level) we want it to be the master brain of your SOC and to the extent that we cannot, you or an organization like CRITICALSTART can build SOC capabilities on top of Sentinel and have it be extensible and make it easier for your SOC admins to react to something quickly, so a breach doesn’t turn into a major event. We have a big, bold vision, but we also don’t know everything the future holds, which is why it’s so extensible.”
Ann went on to discuss how Microsoft is utilizing machine learning to take advantage of the advancements in AI, but that one of their most important principles is automation. As an example, she stated that if there are a trillion signals, with a million that could represent a threat, then the goal is to automate 999,000 of them. Then out of the remaining thousand, prioritize until the top five are identified that SOC analysts need to focus on at that very moment. This correlation of alerts enables continually less, but ever more important alerts to go to analysts for human review and intervention.
Stop threats before they happen
Ann believes human input will be even more important in the years ahead. “People always ask me, “let’s see how technology can replace humans,” she shared. “My response to that is never. Human intel and understanding of the behavior of the attackers and where they’re going to go next and what they’re going to try to do all needs to be part of predictive analytics. That’s why I want to make it easier for customers by just automatically being predictive and blocking stuff that potentially comes into their environment. I think you’ll see a natural convergence of XDR and SIEM into one thing—we just have to make sure that we get it right. We want simplicity of tooling and automation of tooling. The goal is that we want customers running their businesses and not worried about their security tooling. The point when cybersecurity becomes a mature industry will be when there are no longer cybersecurity departments and when everybody’s problem is cybersecurity. Whether you’re a developer or an operator, you’ll still have a SOC. Cybersecurity needs to be everybody’s job from the first line of code.”
“And I’m optimistic on achieving this outcome,” Ann concluded. “I’m always optimistic because we have really smart people trying to solve hard problems. But at the end of the day, we need to work to become more integrated into the fabric of everything that happens within an organization.”

Transform Vulnerability Management: How Critical Start & Qualys Reduce Cyber Risk
In a recent webinar co-hosted by Qualys and Critical Start, experts from both organizations discusse...
H2 2024 Cyber Threat Intelligence Report: Key Takeaways for Security Leaders
In a recent Critical Start webinar, cyber threat intelligence experts shared key findings from the H...
Bridging the Cybersecurity Skills Gap with Critical Start’s MDR Expertise
During a recent webinar hosted by CyberEdge, Steven Rosenthal, Director of Product Management at Cri...
2024: The Cybersecurity Year in Review
A CISO’s Perspective on the Evolving Threat Landscape and Strategic Response Introduction 2024 has...
Modern MDR That Adapts to Your Needs: Tailored, Flexible Security for Today’s Threats
Every organization faces unique challenges in today’s dynamic threat landscape. Whether you’re m...
Achieving Cyber Resilience with Integrated Threat Exposure Management
Welcome to the third and final installment of our three-part series Driving Cyber Resilience with Hu...Why Remote Containment and Active Response Are Non-Negotiables in MDR
You Don’t Have to Settle for MDR That Sucks Welcome to the second installment of our three-part bl...
Choosing the Right MDR Solution: The Key to Peace of Mind and Operational Continuity
Imagine this: an attacker breaches your network, and while traditional defenses scramble to catch up...
Redefining Cybersecurity Operations: How New Cyber Operations Risk & Response™ (CORR) platform Features Deliver Unmatched Efficiency and Risk Mitigation
The latest Cyber Operations Risk & Response™ (CORR) platform release introduces groundbreaking...
The Rising Importance of Human Expertise in Cybersecurity
Welcome to Part 1 of our three-part series, Driving Cyber Resilience with Human-Driven MDR: Insights...
Achieving True Protection with Complete Signal Coverage
Cybersecurity professionals know all too well that visibility into potential threats is no longer a ...
Beyond Traditional MDR: Why Modern Organizations Need Advanced Threat Detection
You Don’t Have to Settle for MDR That Sucks Frustrated with the conventional security measures pro...The Power of Human-Driven Cybersecurity: Why Automation Alone Isn’t Enough
Cyber threats are increasingly sophisticated, and bad actors are attacking organizations with greate...Importance of SOC Signal Assurance in MDR Solutions
In the dynamic and increasingly complex field of cybersecurity, ensuring the efficiency and effectiv...The Hidden Risks: Unmonitored Assets and Their Impact on MDR Effectiveness
In the realm of cybersecurity, the effectiveness of Managed Detection and Response (MDR) services hi...
The Need for Symbiotic Cybersecurity Strategies | Part 2: Integrating Proactive Security Intelligence into MDR
In Part 1 of this series, The Need for Symbiotic Cybersecurity Strategies, we explored the critical ...Finding the Right Candidate for Digital Forensics and Incident Response: What to Ask and Why During an Interview
So, you’re looking to add a digital forensics and incident response (DFIR) expert to your team. Gr...
The Need for Symbiotic Cybersecurity Strategies | Part I
Since the 1980s, Detect and Respond cybersecurity solutions have evolved in response to emerging cyb...
Critical Start H1 2024 Cyber Threat Intelligence Report
Critical Start is thrilled to announce the release of the Critical Start H1 2024 Cyber Threat Intell...
Now Available! Critical Start Vulnerability Prioritization – Your Answer to Preemptive Cyber Defense.
Organizations understand that effective vulnerability management is critical to reducing their cyber...
Recruiter phishing leads to more_eggs infection
With additional investigative and analytical contributions by Kevin Olson, Principal Security Analys...
2024 Critical Start Cyber Risk Landscape Peer Report Now Available
We are excited to announce the release of the 2024 Critical Start Cyber Risk Landscape Peer Report, ...Critical Start Managed XDR Webinar — Increase Threat Protection, Reduce Risk, and Optimize Operational Costs
Did you miss our recent webinar, Stop Drowning in Logs: How Tailored Log Management and Premier Thre...Pulling the Unified Audit Log
During a Business Email Compromise (BEC) investigation, one of the most valuable logs is the Unified...
Set Your Organization Up for Risk Reduction with the Critical Start Vulnerability Management Service
With cyber threats and vulnerabilities constantly evolving, it’s essential that organizations take...
Announcing the Latest Cyber Threat Intelligence Report: Unveiling the New FakeBat Variant
Critical Start announces the release of its latest Cyber Threat Intelligence Report, focusing on a f...Cyber Risk Registers, Risk Dashboards, and Risk Lifecycle Management for Improved Risk Reduction
Just one of the daunting tasks Chief Information Security Officers (CISOs) face is identifying, trac...
Beyond SIEM: Elevate Your Threat Protection with a Seamless User Experience
Unraveling Cybersecurity Challenges In our recent webinar, Beyond SIEM: Elevating Threat Prote...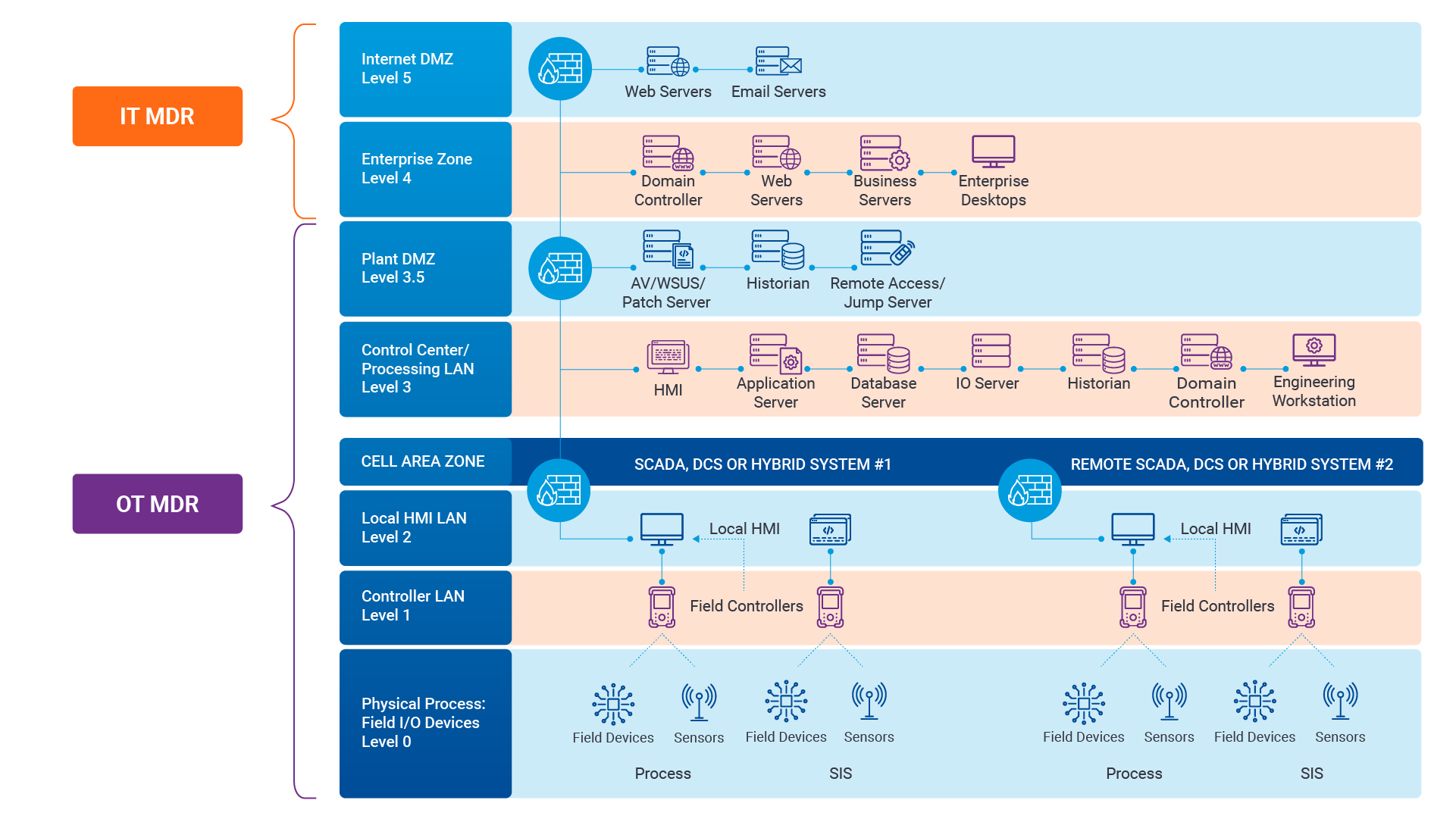
Navigating the Convergence of IT and OT Security to Monitor and Prevent Cyberattacks in Industrial Environments
The blog Mitigating Industry 4.0 Cyber Risks discussed how the continual digitization of the manufac...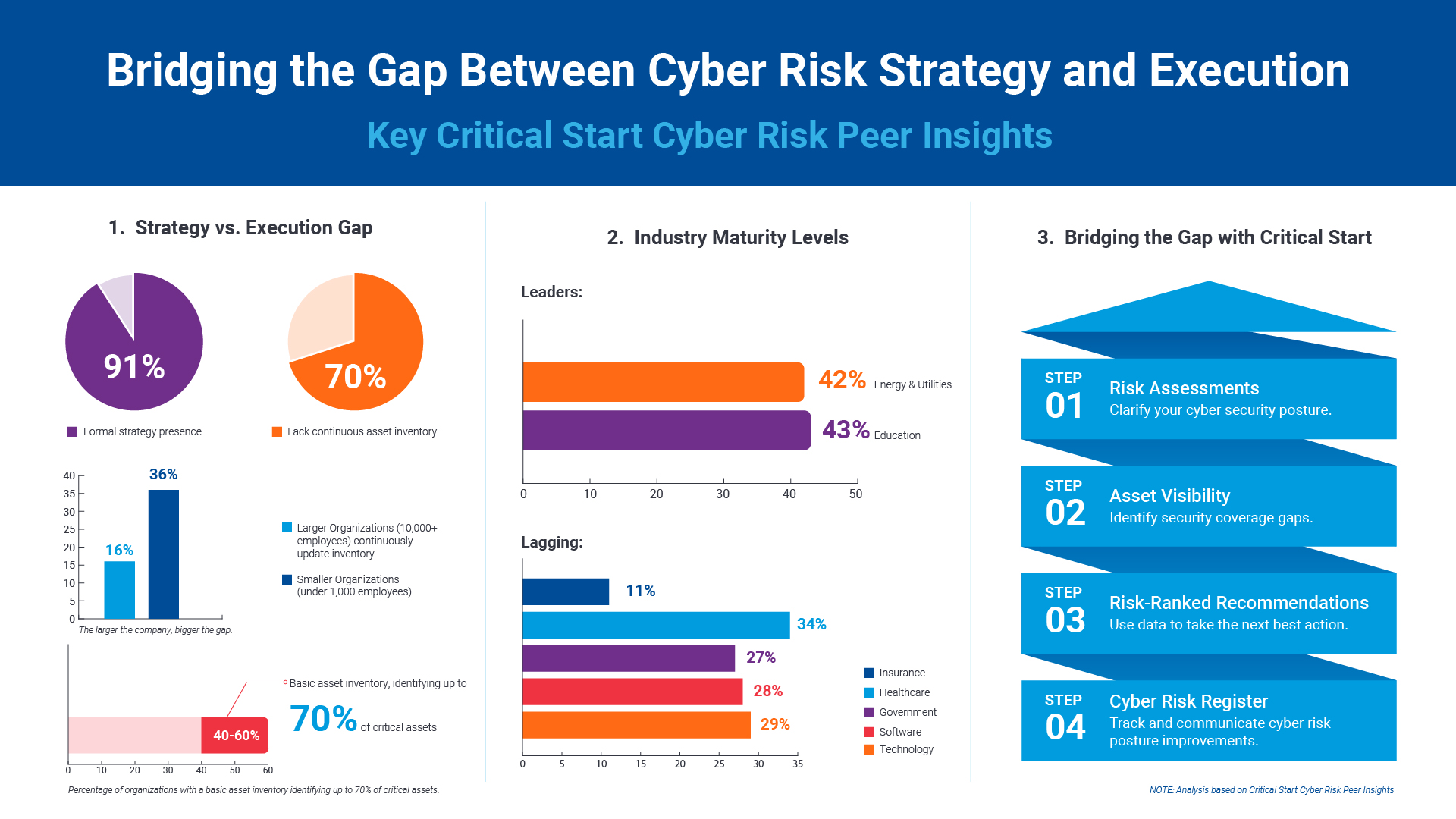
Critical Start Cyber Risk Peer Insights – Strategy vs. Execution
Effective cyber risk management is more crucial than ever for organizations across all industries. C... Press Release
Press ReleaseCritical Start Named a Major Player in IDC MarketScape for Emerging Managed Detection and Response Services 2024
Critical Start is proud to be recognized as a Major Player in the IDC MarketScape: Worldwide Emergin...Introducing Free Quick Start Cyber Risk Assessments with Peer Benchmark Data
We asked industry leaders to name some of their biggest struggles around cyber risk, and they answer...Efficient Incident Response: Extracting and Analyzing Veeam .vbk Files for Forensic Analysis
Introduction Incident response requires a forensic analysis of available evidence from hosts and oth...
Mitigating Industry 4.0 Cyber Risks
As the manufacturing industry progresses through the stages of the Fourth Industrial Revolution, fro...
CISO Perspective with George Jones: Building a Resilient Vulnerability Management Program
In the evolving landscape of cybersecurity, the significance of vulnerability management cannot be o...
Navigating the Cyber World: Understanding Risks, Vulnerabilities, and Threats
Cyber risks, cyber threats, and cyber vulnerabilities are closely related concepts, but each plays a...The Next Evolution in Cybersecurity — Combining Proactive and Reactive Controls for Superior Risk Management
Evolve Your Cybersecurity Program to a balanced approach that prioritizes both Reactive and Proactiv...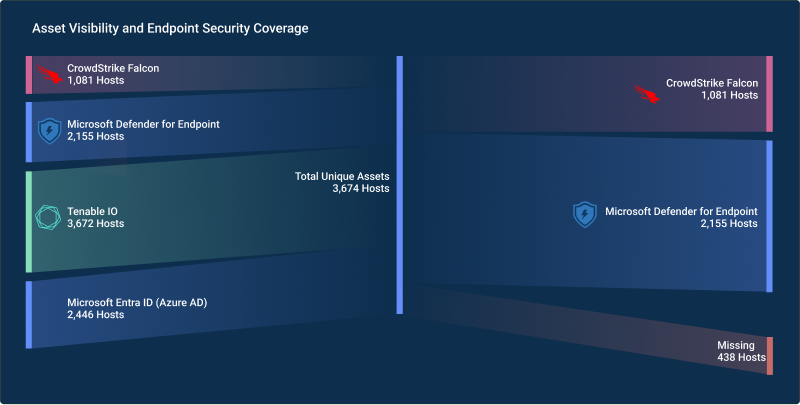
CISO Perspective with George Jones: The Top 10 Metrics for Evaluating Asset Visibility Programs
Organizations face a multitude of threats ranging from sophisticated cyberattacks to regulatory comp...
5 Signs Your MDR Isn’t Working — and What to Do About It
Are you confident your MDR is actually reducing risk? If so, how confident? According to recent indu... Datasheet
DatasheetSecurity Services for SIEM
Critical Start’s Security Services for SIEM combines Managed SIEM and MDR for SIEM to deliver ...
Building a Future-Proof Security Stack with Flexible MDR
Technology evolves. Organizations grow. But is your cybersecurity strategy keeping up? Come on; be h...
Newsletter Signup
Stay up-to-date on the latest resources and news from CRITICALSTART.
Thanks for signing up!