Check out the CRTICALSTART Blog for the latest industry news, security landscape updates and expert-curated content.
 Press Release
Press ReleaseCritical Start Honored with Placement in the 2025 CRN® Partner Program Guide
Plano, TX, March 24, 2025 — Critical Start, a leader in Managed Detection and Response (MDR) servi...
 Catalog
CatalogCyber Incident Response Team (CIRT ) Professional Services Catalog
Our Cyber Incident Response Team (CIRT) offers proactive (incident response plans, assessments, pent...
 Webinar
WebinarMastering Vulnerability Management: Reduce Cyber Risk by 85%
Vulnerabilities are evolving—are your defenses keeping up? In this expert-led webinar, Critical St...
 Customer Stories
Customer StoriesAchieving Effective Vulnerability Management at Scale – and a Whole lot more
Managing cybersecurity at a fast-growing company comes with unique challenges. In this case study, s...
 Press Release
Press ReleaseCRITICALSTART® Unveils H2 Cyber Threat Intelligence Report Highlighting Key Threats Disrupting Businesses
Report discovers drastic shift in targeting patterns and finds professional services has displaced m...
 eBook
eBookH2 2024 Cyber Threat Intelligence Threat Report
Cyber threats continue to evolve at an alarming rate, with attackers shifting their tactics, targets...
 Webinar
WebinarH2 2024 Cyber Threat Intelligence Report: Key Trends, Threat Actors & Defensive Strategies
Stay Ahead of Cyber Threats in 2024 & Beyond Cyberattacks surged in H2 2024—are you prepared? ...
 Press Release
Press ReleaseCritical Start Named to CRN’s MSP 500 List for 2025
PLANO, Texas, Feb. 10, 2025— Critical Start, a leader in Managed Detection and Response (MDR) cybe...
 Press Release
Press ReleaseDwayne Myers of Critical Start Recognized as a 2025 CRN® Channel Chief
Channel program leader honored for the fourth time PLANO, Texas, Feb. 3, 2025 — Critical Start, a ...
 News
NewsA Blueprint for Fighting Ransomware in 2025
Jan 23, 2025 | Ransomware groups are evolving, with AI-powered threats and aggressive extortion tact...
 News
NewsAre Companies Putting Profits Over Privacy?
Jan 14, 2025 | Many organizations prioritize cost-cutting over client privacy, leaving sensitive dat...
 News
NewsStop wasting money on ineffective threat intelligence: 5 mistakes to avoid
Jan. 15, 2025 | Cyber threat intelligence (CTI) can be a powerful tool, but many organizations waste...
 News
NewsNorth Korea’s IT Worker Scam Tied to 2016 Crowdfunding Operation – Critical Start
Jan. 16, 2025 | A newly uncovered link between North Korea’s Nickel Tapestry IT worker scam and a ...
 News
NewsInside the Four-Month Espionage Campaign by Suspected Chinese Threat Actors – Critical Start
Jan. 17, 2025 | A U.S. organization with major operations in China faced a four-month cyberespionage...
 Webinar
WebinarNavigating Through a Blizzard of Logs: Advanced Threat Hunting & IR Techniques
Watch the On-Demand Recording of Navigating Through a Blizzard of Logs: Advanced Threat Hunting &...
 News
NewsCISA Adds Mitel, Oracle, flaws to the KEV list
January 10, 2025 | CISA has updated its Known Exploited Vulnerabilities (KEV) catalog with critical ...
 Press Release
Press ReleaseBuilt In Honors Critical Start in Its Esteemed 2025 Best Places To Work Awards
Critical Start Earns Spot 100 Best Midsize Places to Work in Dallas for 2025 on Built In’s B...
 News
NewsCISA Adds Mitel and Oracle Bugs to Exploited List – Critical Start
Jan. 9, 2025 | CISA has added three vulnerabilities to its KEV catalog, including a critical Mitel M...
 News
NewsSharing of Telegram User Data Surges After CEO Arrest – Critical Start
Jan. 7, 2025 | Telegram, once known for strict user privacy, shared data from 14 to 900 U.S. request...
 Webinar
WebinarAnalyst-Led, AI-Assisted: The Future of Cybersecurity Defense
Discover how human expertise and AI innovation are transforming the way organizations combat cyber t...
Webinar
Critical Start Platform Updates
We are excited to announce the latest enhancements to Critical Start’s Cyber Operations Risk &...
 Datasheet
DatasheetCritical Start Asset Visibility
Critical Start Asset Visibility gives you a single source of truth for your asset inventory, uncover...
 eBook
eBookEnhancing MDR Outcomes Through Asset Visibility: A Strategic Guide
What You’ll Learn If you’re a cybersecurity professional tasked with improving detection, stream...
 Quick Card
Quick CardCoverage Gap Detection
How quickly can you discover unprotected endpoints? Faster than your adversaries? See how Critical S...
 Quick Card
Quick CardBenign True Positive and False Positive Alert Verdicts
When a cyber alert hits your queue, are you certain it’s not a false alarm or part of an ongoi...
 Quick Card
Quick CardCritical Start Response Authorizations
Does your MDR provider expect your environment to fit neatly into their idea of what “detectio...
 White Paper
White PaperAhead of the Curve: The Role of CTEM in Cyber Risk Management
Continuous Threat Exposure Management (CTEM) is as a cyclical “set of processes and capabilities t...
 Webinar
WebinarHook, Line, & Secure: Leveraging MDR to Streamline Phishing Detection & Response
Join Tim Bandos, Field CISO at Critical Start, as he explores the evolving landscape of phishing att...
News
Zero-Day Exploits Surge in 2023: Cisco and Fortinet Under Fire
Nov 15, 2024 | In 2023, attackers increasingly targeted zero-day vulnerabilities, leveraging flaws i...
News
Iranian “Dream Job” Campaign Targets Aerospace Sector
Nov 15, 2024 | Iranian threat group TA455 is using fake job offers to infiltrate the aerospace indus...
News
Celebrating the 2024 Women in IT Security Honorees – SC Media
Nov 14, 2024 | Meet the extraordinary women driving innovation in cybersecurity. From industry veter...
 News
NewsCritical Start’s Callie Guenther: Shaping the Future of Digital Defense – SC Media
Nov 13, 2024 | From her Navy beginnings to leading Critical Start’s Cyber Research Unit, Callie Gu...
 News
NewsIranian Group Targets Aerospace Workers with Fake Job Lures – SC Media
Nov 13, 2024 | The Iranian Dream Job Campaign, active since September 2023, sees TA455 (UNC1549) tar...
 Webinar
Webinar[On-Demand Webinar] Leveraging MDR to Streamline Phishing Detection and Response
The evolving threat of phishing requires organizations to adopt smarter, faster, and more effective ...
 News
NewsTricked By a CAPTCHA: Cybercriminals Exploit Fake Verifications to Steal Sensitive Data – SC Media
Nov 12, 2024 | Lumma Stealer malware leverages fake CAPTCHA pages to execute advanced attacks, decei...
 News
NewsAlways-on Defense: The Critical Role of Monitoring in Manufacturing Cyber Protection
Nov 11, 2024 | Cyberattacks on manufacturing are rising, targeting legacy systems and interconnected...
 News
NewsMalicious PyPI Package Steals AWS Credentials: A Long-Term Supply Chain Threat
Nov 11, 2024 | Cybersecurity researchers have uncovered a malicious PyPI package, “fabrice,...
 News
NewsLatrodectus Malware: The Stealth Phishing Threat to Critical Sectors – SC Media
Nov 11, 2024 | Emerging in 2023, Latrodectus malware targets critical sectors like finance, healthca...
 News
NewsMalicious Python Package “Fabrice” Steals AWS Credentials via 37,000+ Downloads
Nov 7, 2024 | A malicious Python package called “Fabrice” was typosquatting the popular Fabric S...
 Customer Stories
Customer StoriesLeading Food Service Distributor Realized Maximum Value from Security Program with Tailored MDR from Critical Start
Learn how one of the largest food service distributors transformed their security operations with Cr...
 News
NewsStrengthening OT Cybersecurity in the Industry 4.0 Era
Nov 6, 2024 | As OT and IT systems converge, organizations face new cybersecurity risks. The Colonia...
 News
NewsSentinelOne Expands Autonomous SOC Vision with New AI and Automation
Nov 4, 2024 | SentinelOne is advancing its goal of an autonomous SOC with AI-driven updates to the S...
News
MSSPs: Key Partners in the Evolving World of Third-Party Risk Management (TPRM)
Nov 4, 2024 | As TPRM grows, MSSPs offer essential support by closing visibility and expertise gaps....
 News
NewsReturn from the Data Fog: Cybersecurity’s Scariest 2024 Trends
October 31, 2024 | This Halloween, beware the latest cyber threats: deepfake scams, AI-driven phishi...
 News
NewsNIST’s NICE: 3 Ways to Adapt the Hiring Framework for Modern Threats
Oct 31, 2024 | The NICE cybersecurity hiring framework is a solid foundation for building a security...
 News
NewsA Halloween Haunting: Cybersecurity’s Scary Stats
Oct 31, 2024 | This Halloween, cybersecurity reports reveal chilling insights: 17.8M phishing emails...
 News
NewsScary Cybersecurity Stats: 2024 Highlights
Oct 31, 2024 | The 2024 cybersecurity landscape revealed alarming trends. AI-driven threats surged, ...
 News
NewsAI Cyberattacks Rise but Businesses Still Lack Insurance
Oct 30, 2024 | A Nationwide survey finds that despite rising AI-driven cyber threats, many businesse...
 News
NewsFakeCall Android Trojan Evolves with New Evasion Tactics – SecurityWeek
Oct 30, 2024 | The FakeCall Android trojan has adopted advanced evasion and surveillance techniques,...
 News
NewsIntel and AMD Chips Still Vulnerable to Spectre Flaw
Oct 29, 2024 | Over six years since the Spectre flaw was first revealed, Intel and AMD processors re...
 News
NewsSentinelOne Expands Autonomous SOC Vision with New AI and Automation
Oct 24, 2024 | SentinelOne is advancing its goal of an autonomous SOC with AI-driven updates to the ...
 News
NewsCISOs respond: 49% of CISOs plan to leave role without industry action
Oct 23, 2024 | Trellix’s survey reveals that 91% of CISOs foresee increased turnover due to expand...
 News
NewsBumblebee Malware Is Buzzing Back to Life
Oct 23, 2024 | Just months after Europol’s takedown of botnets in Operation Endgame, the Bumblebee...
 News
NewsGoogle Mandiant: Time-to-Exploit Falls, Zero-Day Exploits Rise
Oct 23, 2024 | In 2023, 70% of exploited vulnerabilities were zero-days, with the average Time-to-Ex...
 News
NewsBumblebee malware infection chain seen for the first time since May
Oct 22, 2024 | The Bumblebee malware, used to deploy Cobalt Strike and ransomware, has reappeared in...

Tricky CAPTCHA Drops Lumma Stealer Malware
Oct 22, 2024 | Lumma Stealer’s latest campaign deceives users with fake CAPTCHA pages, tricking th...
 Customer Stories
Customer StoriesCRITICALSTART® MDR Frees Up Team Resources, Improves Security Outcomes for Oil States International
Discover how Oil States International improved their security posture, reduced operational costs, an...
 Webinar
WebinarConfronting the Invisible: Tactics to Mitigate Security Gaps in Modern Threat Response
It’s an unfortunate reality — cybersecurity professionals face threats they often can’t see. F...
 News
NewsOpen-Source Entry Points Targeted for Supply Chain Compromise
Oct 15, 2024 | Threat actors are exploiting open-source environments like PyPI, npm, and Ruby Gems t...
 News
NewsBasic Cyber Hygiene Still Offers the Best Defense Against Ransomware
Oct 17, 2024 | The FBI’s takedown of the Dispossessor ransomware gang highlights a critical truth:...
 News
NewsThreat Actors Exploit Zero Days Within 5 Days, Says Google’s Mandiant
Oct 17, 2024 | Google Mandiant’s analysis of 138 actively exploited vulnerabilities in 2023 reveal...
 News
NewsThe Evolving Threat Landscape in Manufacturing
Oct 17, 2024 | As Industry 4.0 connects manufacturing to the digital world, the sector faces a risin...
Webinar
[On-Demand Webinar] Ensuring Comprehensive Threat Detection with SOC and MDR
The ability to swiftly and accurately detect hidden threats is critical. Yet, many organizations fac...
News
Black Lotus, Emotet, Beep, and Dark Pink: Top Malware Threats of 2024
Oct 15, 2024 | As 2024 closes, malware like Black Lotus, Emotet, Beep, and Dark Pink continue to evo...
 News
NewsFidelity Investments Data Breach Impacts More Than 77,000 Customers
Oct 14, 2024 | Fidelity Investments disclosed a data breach affecting over 77,000 customers. Securit...
 News
NewsCommand-Jacking Used to Launch Malicious Code on Open-Source Platforms
Oct 14, 2024 | Attackers are exploiting entry points in open-source environments like PyPI and npm t...
 eBook
eBookBuyer’s Guide to Managed Detection & Response
Traditional security measures are no longer sufficient in today’s rapidly evolving threat landscap...
 News
NewsOver 77K Affected in Fidelity Investments Data Breach
October 11, 2024 | Fidelity Investments reported a data breach that exposed the personal information...
 News
NewsFidelity Breach Exposes Data of 77,000 Customers: What to Do If Affected
October 11, 2024 | Fidelity Investments reported a data breach impacting 77,000 customers. The breac...
 News
NewsCISOs Concerned Over Growing Demands of Their Role – DICE Insights
Nov 18, 2024 | With cybersecurity threats growing in complexity, 84% of CISOs advocate splitting the...
News
Fidelity Confirms Data Breach Impacting 77K Customers
October. 10, 2024 | Fidelity Investments confirmed a data breach affecting 77,099 customers in Augus...
 News
NewsFidelity Investments Data Breach Impacts Nearly 80,000 Customers
October 10, 2024 | Fidelity Investments disclosed a data breach that affected 77,099 customers. The ...
 News
NewsFidelity Notifies 77K Customers of Data Breach
October 10, 2024 | Fidelity Investments has notified over 77,000 customers that their personal infor...
 News
News30 Notable IT Executive Moves: September 2024
October 9, 2024 | Major tech companies like TD Synnex, ConnectWise, Critical Start, ThoughtSpot, Mic...
 News
NewsmacOS Sequoia Update Fixes Security Tool Issues
October 9, 2024 | Apple has released macOS Sequoia 15.0.1, addressing compatibility problems with Mi...
 News
NewsApple Fixes Security Tool Issues with macOS Update
October 8, 2024 | Apple’s macOS 15.0.1 patch addresses compatibility problems affecting CrowdStrik...
 News
NewsCRITICALSTART® Appoints Stuti Bhargava as Chief Customer Officer
October 4, 2024 | Critical Start has appointed Stuti Bhargava as its new Chief Customer Officer (CCO...
 News
NewsCritical Start Welcomes Stuti Bhargava as Chief Customer Officer
October 7, 2024 | Critical Start has appointed Stuti Bhargava as Chief Customer Officer. With over 2...
 News
NewsTeleCloud Acquired by Davenforth, Expanding Managed IT Services
October 4, 2024 | Davenforth, a family office based in Austin, has acquired Frisco-based TeleCloud a...
 News
NewsHow GM CEO Mary Barra is Tackling Her Second Major Transformation
September 4, 2024 | Mary Barra, CEO of General Motors, is steering the company through a second majo...
 Press Release
Press ReleaseCRITICALSTART® Expands Executive Bench by Appointing New Chief Customer Officer
Stuti Bhargava joins leadership team to continue expanding services and value for Critical Start cus...
 News
NewsGartner Magic Quadrant Names Microsoft, SentinelOne Among EPP Leaders
October 3, 2024 | Microsoft, SentinelOne, and CrowdStrike lead Gartner’s 2024 Magic Quadrant for e...
 News
NewsWhat Is the Market Impact of the SEC’s Cyber Disclosure Rules? Not Much.
October 3, 2024 | Data shows little impact on stock prices following cyber incident disclosures requ...
 News
NewsManufacturing Day 2024
October 3, 2024 | Manufacturing Day kicks off today, launching a month-long series of events across ...
 News
NewsCritical Start Appoints Chief Customer Officer
October 3, 2024 | Critical Start, a provider of MDR cybersecurity solutions, has appointed Stuti Bha...
 News
NewsNational Manufacturing Day 2024
October 2, 2024 | Happy Manufacturing Day 2024! This annual celebration aims to inspire interest in ...
News
Average CISO Compensation Tops $500K
October 2, 2024 | U.S.-based chief information security officers (CISOs) now earn an average of $565...
 News
NewsNorth Korean’s Stonefly Shifts from Espionage to Ransomware, Extortion
October 2, 2024 | North Korean hacking group Stonefly has shifted from espionage to financially moti...
 eBook
eBookBuyer’s Guide for Security Services for SIEM
Explore how to optimize the value of your Security Information and Event Management (SIEM) investmen...
 News
NewsSalt Typhoon Targets U.S. ISPs: A New Cyber Threat
September 27, 2024 | The China-linked group Salt Typhoon has targeted several U.S. internet service ...
 News
NewsArkansas City Water Treatment Facility Cybersecurity Incident
September 25, 2024 | Arkansas City, Kansas, experienced a cybersecurity incident affecting its water...
North Korean Hacker Group Using False Coding Tests to Spread Malware
September 16, 2024 | The notorious Lazarus Group is posing as recruiters to spread malware via fake ...
 News
NewsFeds Investigate Cyberattack on Kansas Water Treatment Facility
September 24, 2024 | The FBI and Department of Homeland Security are investigating a cyberattack on ...
 News
NewsTarget Practice: Honing Skills on Cyber Ranges
September 23, 2024 | Cyber ranges are vital for cybersecurity professionals to stay updated on threa...
News
N-able: Cyberattacks on Microsoft 365 Security Surge 56%
September 20, 2024 | N-able’s new report reveals a 56% rise in cyberattacks on Microsoft 365 i...
 News
NewsCritical Start Appoints New CEO as Part of Executive Transition
September 20, 2024 | Critical Start has appointed Scott White as its new CEO, succeeding founder Rob...
 News
NewsTeamTNT Hackers Attacking VPS Servers Running CentOS
September 20, 2024 | The hacking group TeamTNT has launched a new attack campaign targeting VPS serv...
 eBook
eBookIn-Depth Analysis: The Evolving DarkGate Malware Campaign
Explore the latest findings on the DarkGate malware campaign in this comprehensive technical report ...
 Webinar
Webinar[On-Demand Webinar] Kickstarting Your OT Security Journey: Practical Steps for Industrial Operations
Are your current Operational Technology (OT) security measures truly safeguarding your industrial op...

TeamTNT Hackers Attacking VPS Servers Running CentOS
A new cryptojacking campaign by TeamTNT is targeting cloud infrastructures, specifically Docker cont...
 News
NewsZero-Click Vulnerabilities in macOS Calendar Risk iCloud Data Exposure
A series of macOS vulnerabilities in the Calendar app exposed iCloud data by bypassing security feat...
 News
NewsZero-Click RCE Bug in macOS Calendar Exposes iCloud Data
September 18, 2024 | A zero-click vulnerability chain in macOS allowed attackers to bypass security ...
 News
NewsClosing the Gap Between Cyber Risk Strategy and Execution
September 18, 2024 | A recent Cyber Risk Peer Benchmarking Report from Critical Start reveals a disc...
 News
NewsFour Ways to Stay Ahead of the Ransomware Threat
September 18, 2024 | Ransomware groups like LockBit, Play, and BlackBasta are behind 40.54% of attac...
 White Paper
White PaperKickstarting Your OT Security Journey: Practical Steps for Industrial Operations
Practical steps for securing Operational Technology (OT) systems are fundamental for building resili...
 News
NewsCritical Start Appoints Scott White as Chief Executive Officer
September 17, 2024 | Critical Start, a leader in Managed Detection and Response (MDR) cybersecurity ...
 News
NewsExpert Insights on National Insider Threat Awareness Month: Why It Matters for Cybersecurity
September 17, 2024 | National Insider Threat Awareness Month highlights the need to address insider ...
 News
NewsGitLab Fixes Critical Pipeline Vulnerability
September 17, 2024 | GitLab has released security updates for 17 vulnerabilities, including a critic...
 Press Release
Press ReleaseCritical Start Appoints Scott White as Chief Executive Officer
Plano, TX — September 16, 2024 —- Critical Start, a leader in Managed Detection and Response (MD...

MSSP Market News: Immersive Labs Launches Cyber Threat Online Community
September 16, 2024 | Each business day, MSSP Alert provides key updates from the MSSP, MSP, and cybe...
 News
NewsTapping Into Asset Visibility for Enhanced MDR Outcomes
September 16, 2024 | Asset visibility is key to improving Managed Detection and Response (MDR) outco...
 News
NewsGitLab Patches Bug That Could Expose CI/CD Pipeline to Supply Chain Attack
September 13, 2024 | GitLab has patched a critical vulnerability (CVE-2024-6678) with a CVSS score o...
 News
NewsCISA Alerts Federal Agencies to Urgent Microsoft Vulnerabilities
Sept 12, 2024 | The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical wa...
 News
NewsIndustries Under Siege: The Rising Threat of Cyberattacks in 2024
September 12, 2024 | Cyberattacks are increasingly threatening industries vital to global economies....
 News
NewsHackers Have Sights Set on Four Microsoft Vulnerabilities, CISA Warns
Sept 11, 2024 | U.S. federal civilian agencies have until the end of September to patch four critica...
 News
NewsLazarus Targets Developers with Sophisticated Coding Test Scam
Sept 11, 2024 | The North Korean hacking group Lazarus has launched a new campaign targeting develop...
 News
NewsDespite cyberattacks, water security standards remain a pipe dream
September 9, 2024 | U.S. water systems are facing rising cyber threats from China, Russia, and Iran....
 News
NewsNew Vulnerability Exposes YubiKey 5 Devices to Cloning Attacks
Sept 05, 2024 | A vulnerability known as “Eucleak” puts YubiKey 5 devices with firmware ...
 News
NewsPlanned Parenthood Confirms Cyberattack by RansomHub
Sept 05, 2024 | Planned Parenthood has confirmed a cyberattack on its Montana organization, forcing ...
 News
NewsNew Vulnerability Puts YubiKey 5 Devices at Risk
Sept 05, 2024 | A recently discovered flaw, “Eucleak,” exposes YubiKey 5 devices with fi...
 News
NewsVMware ESXi Flaw Leveraged by BlackByte Ransomware
Sept 05, 2024 | The BlackByte ransomware group has been exploiting a new VMware ESXi vulnerability (...
 News
NewsEPSS and Vulnerability Management: New Scoring System Shows Promise
Sept 04, 2024 | The Exploit Prediction Scoring System (EPSS) helps organizations prioritize vulnerab...
 News
NewsCyber Threats That Shaped H1 2024
Sept 02, 2024 | In the first half of 2024, cybercrime surged across industries, with ransomware and ...
 News
NewsCyber Threats in H1 2024
August 30, 2024 | Critical Start’s Cyber Research Unit analyzed over 3,400 high-risk alerts an...
 News
NewsBlackByte Ransomware Targets More Orgs Than Reported
August 29, 2024 | Cisco researchers discovered that the BlackByte ransomware group is hiding most of...
 News
NewsBlackByte Targets Vulnerable VMware ESXi Instances
August 29, 2024 | The BlackByte ransomware group, believed to have branched off from Conti, is explo...
 News
NewsBlackByte Exploits VMware ESXi Authentication Flaw
August 29, 2024 | The BlackByte ransomware group, believed to have splintered from Conti, is exploit...
 News
NewsKey Cyber Threats in H1 2024: Ransomware, Data Leaks, and Evolving Attack Methods
August 29, 2024 | BlackByte, likely a Conti spin-off, is now exploiting a newly disclosed VMware ESX...
 News
NewsOver 3,400 High-Risk Cyber Alerts in Early 2024
August 28, 2024 | The first half of 2024 recorded over 3,438 high-risk cyber alerts, with a 46.15% r...
 News
NewsBlackByte Ransomware Group Targets VMware ESXi Bug
August 28, 2024 | The BlackByte ransomware group is exploiting a new authentication bypass vulnerabi...
 News
NewsCisco: BlackByte Ransomware Only Posts 20% to 30% of Successful Attacks
August 28, 2024 | The BlackByte ransomware gang is revealing only a small portion of its successful ...
 News
NewsCriticalStart® Unveils Mid-Year Cyber Threat Intelligence Report
August 26, 2024 | Critical Start has released its Cyber Threat Intelligence Report for the first hal...
 News
NewsManufacturing: The Most Targeted Industry for Cybercrime in 2024
August 26, 2024 | Critical Start’s latest Cyber Threat Intelligence Report reveals that manufa...
 News
NewsRising Cyber Threats in 2024: Critical Start’s Report Insights
August 26, 2024 | Critical Start’s latest report highlights a 15% annual increase in global cyberc...
 News
NewsAI-Driven Part Detection for Machine Tending Cobots
August 26, 2024 | Universal Robots (UR) is embracing AI with its new machine tending solution, enhan...
 News
NewsWhich Industries Face the Most Cyber-attacks?
August 23, 2024 | A new report from Critical Start reveals alarming trends in ransomware and databas...
 News
NewsManufacturing and Industrial Products Most Targeted by Cybercriminals
August 23, 2024 | The Critical Start Cyber Threat Intelligence Report reveals that Manufacturing and...
 News
NewsRise in Cyberattacks Across Multiple Industries
August 23, 2024 | The Critical Start Cyber Intelligence Report reveals that the manufacturing and he...
 News
NewsCritical Start Unveils Mid-Year Cyber Threat Intelligence Report
August 23, 2024 | Manufacturing and industrial sectors lead cyberattack targets in H1 2024, with dee...
 News
NewsOver 3,400 High and Critical Cyber Alerts Recorded in H1 2024
August 22, 2024 | Critical Start’s Cyber Research Unit reported over 3,438 high and critical c...
 News
NewsManufacturing Is the Most Targeted Sector by Cybercriminals
August 22, 2024 | Critical Start’s latest Cyber Threat Intelligence Report reveals manufacturi...
 Webinar
Webinar[On-Demand Webinar] Crucial Insights from the 2024 Cyber Risk Landscape Report
In today’s rapidly evolving cyber threat landscape, staying ahead of potential risks is more c...
 News
NewsCyberthreat Report from Critical Start Shows Significant Uptick in Ransomware and Data Leaks
August 22, 2024 | A new report from Critical Start reveals a worrying rise in cyberattacks, particul...
 Webinar
Webinar[On-Demand Webinar] Mastering Vulnerability Management and Prioritization with Critical Start
Is your security team overwhelmed by the growing number of vulnerabilities and shrinking time to exp...
 Press Release
Press ReleaseCRITICALSTART® Unveils Mid-Year Cyber Threat Intelligence Report Highlighting Key Threats Disrupting Businesses
Report finds manufacturing and industrial industries as the most targeted sectors by bad actors; Use...
 News
NewsCRITICALSTART Unveils Mid-Year Cyber Threat Intelligence Report Highlighting Key Threats Disrupting Businesses
August 22, 2024 | Critical Start’s latest Cyber Threat Intelligence Report reveals significant...
 News
NewsCRITICALSTART Releases Mid-Year Report on Major Cyber Threats Disrupting Businesses
August 22, 2024 | Critical Start’s latest Cyber Threat Intelligence Report reveals manufacturi...
 News
NewsManufacturing the Number One Target for Cyber Criminals
August 22, 2024 | New cyber threat intelligence reports reveal that manufacturing is the most target...
 News
NewsCritical Start Pinpoints Most Targeted Industries for Cyberattacks
August 22, 2024 | Critical Start’s latest report highlights manufacturing as the most targeted...
 News
NewsCritical Start Equips MSSPs and MSPs with Advanced Cyber Threat Intelligence
August 22, 2024 | Cybercrime is projected to grow 15% annually, reaching $10.5 trillion by 2025. Cri...
 News
NewsManufacturing and Industrial Sectors Most Targeted by Cyberattacks in 2024
August 22, 2024 | A report from Critical Start reveals that manufacturing and industrial products we...
 News
NewsManufacturing Leads in Cyberattacks for 2024
August 22, 2024 | A new report by Critical Start reveals manufacturing is the top target for cyberat...
 News
NewsAuthentication Bypass Discovered in Microsoft Entra ID
August 21, 2024 | A vulnerability in Microsoft Entra ID (formerly Azure AD) allows attackers to bypa...
 News
NewsTLS Bootstrap Attack Exposes Azure Kubernetes Services Cluster
August 20, 2024 | A newly discovered bug in Microsoft Azure Kubernetes Services (AKS) could allow at...
 News
NewsAzure Kubernetes Bug Exposes Cluster Secrets
August 20, 2024 | A critical vulnerability in Microsoft’s Azure Kubernetes Service (AKS) allows at...
 News
NewsRansomware Attack on Indian Payment System Traced to Jenkins Bug
August 16, 2024 | A ransomware attack on India’s payment system has been traced to CVE-2024-23897,...
 News
NewsCritical Start Launches Vulnerability Management Service
August 16, 2024 | Critical Start has introduced its Vulnerability Management Service (VMS) and Vulne...
eBook
H1 2024 Cyber Threat Intelligence Threat Report
Discover the most comprehensive analysis of the cyber threats that shaped the first half of 2024. Cr...
 News
NewsMicrosoft and CrowdStrike Outage: Lessons for Tech Professionals
August 15, 2024 | A recent outage affecting 8.5 million Microsoft Windows machines stemmed from a fl...
 News
NewsCritical Start Delivers Vulnerability Management Service and Vulnerability Prioritization Powered by Qualys VMDR
August 15, 2024 | Critical Start has launched its Vulnerability Management Service (VMS) and Vulnera...
 News
NewsMSSP Market News: Critical Start Launches Vulnerability Management Service
August 15, 2024 | MSSP Alert brings you the latest updates from the MSSP, MSP, and cybersecurity sec...
 Press Release
Press ReleaseCritical Start Delivers Comprehensive Vulnerability Management Service and Vulnerability Prioritization Powered by Qualys VMDR
PLANO, TX, August 15, 2024 – Today, Critical Start, a leading provider of Managed Detection an...
 News
NewsRansomware Group Behind Major Indonesian Attack: Many Masks, Little Sophistication
August 14, 2024 | The ransomware group Brain Cipher gained attention after a major attack on Indones...
 News
NewsCritical Start Cyber Range Revolutionizes Cybersecurity Training
August 13, 2024 | Critical Start has launched the Cyber Range, a free feature of its Critical Start ...
 News
NewsCyberTech Experts Address Cybersecurity Gaps in New MDR Report
August 13, 2024 | Cybersecurity leaders are grappling with a surge in attacks in 2024, highlighting ...
 News
NewsIdentity Management and InfoSec News – Week of August 9
August 9, 2024 | Stay updated with the latest in identity management and information security. This ...
 News
NewsChannel News You Can’t Afford to Miss: This Week’s Biggest Headlines for MSPs
August 9, 2024 | Stay competitive with ChannelPro’s roundup of essential updates. This week’s hi...
 News
NewsSEC Takes No Action on Progress Software for MOVEit Transfer Case
August 9, 2024 | The SEC has decided not to recommend enforcement action against Progress Software f...
 News
NewsChannel Brief: EQT Buys Majority Stake in Acronis, Fortinet Acquires Next DLP
August 8, 2024 | Big news in the tech and MSP world: EQT has acquired a majority stake in Acronis, w...
 Press Release
Press ReleaseCritical Start Unveils Cyber Range: A New Approach for Cybersecurity Training and Evaluation Curated from Thousands of Real-World Cyber Attacks
PLANO, TX, August 7, 2024 – Critical Start, a leader in Managed Detection and Response (MDR) c...
 News
NewsCritical Start Launches Cyber Range for Real-World Cybersecurity Training
August 7, 2024 | Critical Start has unveiled its Cyber Range, a virtual environment simulating real-...
 News
NewsCybersecurity Pros Say Unknown Threats Are Biggest Concern
August 7, 2024 | Unknown threat actors and exploits are the top worry for 86% of cybersecurity profe...
 News
NewsMSSP Market News: Fortinet Buys Next DLP
August 9, 2024 | Fortinet acquires Next DLP to enhance data protection. OPSWAT acquires InQuest, EQT...
 News
NewsFive Ways to Defend Against VMware ESXi Server Attacks
August 7, 2024 | A recent surge in attacks targeting VMware ESXi servers, exploiting the critical CV...
 Press Release
Press ReleaseCRITICALSTART® Enhances MDR with Integrated Asset Inventory & SOC Signal Assurance
PLANO, TX – August 6, 2024 – Critical Start, a leader in Managed Detection and Response (MDR) cy...
 News
NewsCyber Risk Landscape Peer Report: 4 Action Items for Your Organization
August 6, 2024 | Traditional security tools are falling short in today’s complex threat landsc...
 News
NewsCritical Start: 86% of Cyber Pros Worried About Unknown Risks
August 6, 2024 | Critical Start’s latest Cyber Risk Landscape Peer Report reveals that 86% of cybe...
 News
NewsMost Companies Fear Unseen Cybersecurity Threats – Critical Start Report
August 6, 2024 | A Critical Start survey found that 86% of companies are more concerned about unknow...
 News
News86% of Cyber Professionals Cite Unknown Risks as Top Concern – Critical Start Report
August 6, 2024 | A recent report from Critical Start reveals that 86% of cyber professionals now see...
 News
News2024 Cyber Risk Report: 4 Key Takeaways
August 6, 2024 | The latest Cyber Risk Report shows a 16% rise in data breaches. Key actions: align ...
 News
NewsMalware-as-a-Service: A Lucrative Opportunity for Hackers
August 06, 2024 | A new report by Darktrace reveals the rising threat of Malware-as-a-Service (MaaS)...
 News
NewsLinux Exploit SLUBStick Grants Full Memory Access
August 06, 2024 | Researchers have unveiled a new Linux kernel exploit technique called SLUBStick. T...
 Press Release
Press ReleaseCritical Start Finds 86% of Cyber Professionals’ Top Concern is Unknown Cyber Risks vs. Known Threats
Report examines market trends in cyber risk, where organizations of various sizes see their risks, a...
 News
NewsCritical Start: 86% of Cyber Professionals Fear Unknown Risks
August 5, 2024 | A new report from Critical Start reveals that 86% of cybersecurity professionals vi...
 News
NewsThe Gately Report: New Sophos CEO Focuses on Midmarket and SMBs
August 5, 2024 | Joe Levy, the new CEO of Sophos, aims to support midmarket and smaller businesses i...
 News
News86% of Cyber Pros Name Unknown Risks as Top Concern
August 6, 2024 | A new Critical Start report reveals that 86% of cybersecurity professionals now vie...
 Research Report
Research ReportCritical Start 2024 Cyber Risk Landscape Peer Report
Stay ahead of the evolving cyber threat landscape with our comprehensive 2024 Cyber Risk Landscape P...
 News
NewsPeer Report from Critical Start Explores Cyber Risk Landscape
August 5, 2024 | Critical Start’s second annual Cyber Risk Landscape Peer Report reveals that ...
 News
News86% of Firms Identify Unknown Cyber-Risks as Top Concern
August 5, 2024 | A recent report reveals that 86% of firms are most concerned about unknown cyber-ri...
 News
NewsMentorship advances security careers
August 2, 2024 | Security leaders agree: finding a mentor is crucial for career growth. Key traits i...
 News
NewsNorth Korean Hacker Attempts to Infiltrate KnowBe4
August 1, 2024 | KnowBe4 revealed a North Korean hacker tried to infiltrate its systems using a stol...
 News
NewsRoguePuppet software supply chain exposure: Lessons learned
July 30, 2024 | Security researcher Adnan Khan discovered a flaw in Puppet Forge, dubbed RoguePuppet...
 News
NewsHackers Leak Internal Documents Stolen from Leidos Holdings
July 23, 2024 | Hackers have leaked internal documents from Leidos Holdings Inc., an IT services pro...
 News
NewsCybersecurity Skills and Breaches: What Tech Pros Need to Know
29 July 2024 | A new Fortinet report reveals that 90% of organizations experienced breaches due to a...
 News
NewsThe Gately Report: Zimperium Partners Get Formal Channel Program
Plus, cybercriminals are ready to pounce on the Paris Olympics. July 29, 2024 | Zimperium will launc...
 News
News1 Million HotJar Users Vulnerable to XSS Attacks
July 29, 2024 | Salt Labs discovered a critical XSS vulnerability in HotJar, impacting over 1 millio...
 Datasheet
DatasheetSecurity Operations Center (SOC)
See how the human-driven, technology powered Critical Start Security Operations Center helps you inc...
 News
NewsCritical Vulnerability Bypassing Windows SmartScreen Shows Need for Layered Defenses
July 25, 2024 | A vulnerability in Microsoft’s Windows SmartScreen, CVE-2024-21412, bypassed w...
 News
News3,000 GitHub Accounts Found Distributing Malware
July 25, 2024 | Over 3,000 malicious GitHub accounts were found distributing malware like Atlantida ...
 Datasheet
DatasheetManaged Detection and Response Services
Human-Driven MDR Enhanced With Proactive Cybersecurity Intelligence Increase your security operation...
 Webinar
Webinar[On-Demand Webinar] Stop Drowning in Logs: How Tailored Log Management and Premier Threat Detection Keep You Afloat
Are you overwhelmed by security logs and complex threat detection? Watch our on-demand webinar to le...
 News
NewsCybersecurity Firm KnowBe4 Tricked into Hiring North Korean Hacker as IT Pro
July 24, 2024 | KnowBe4, a cybersecurity firm, was deceived by a North Korean hacker posing as an IT...
 News
NewsInsider Threat: KnowBe4 Thwarts North Korean Infiltration Attempt
July 24, 2024 | KnowBe4 recently stopped a North Korean operative posing as a software engineer. The...
 Datasheet
DatasheetCritical Start MDR Services for Operational Technology
Gain 24x7x365 visibility and threat detection across Information Technology (IT) and Operational Tec...
 White Paper
White PaperEnhancing Cyber Risk Management: Unveiling the Five Critical Components
Rapidly evolving cyber threats demand that organizations implement effective cyber risk management p...
 Webinar
Webinar[On-Demand Webinar] Navigating Cybersecurity with Risk Assessments
Enterprise security teams must continually assess shifting threats and implement mitigation controls...
 News
NewsWindows Users Targeted with Zero-Day Attacks via Internet Explorer
July 23, 2024 | An APT group named Void Banshee is exploiting Internet Explorer vulnerabilities to d...
 News
NewsWomen in IT Security Lack Opportunities, Not Talent
July 23, 2024 | Women in IT security are as skilled as men but face significant career barriers, acc...
 News
NewsFallout From Faulty Friday CrowdStrike Update Persists
July 22, 2024 | The CrowdStrike glitch on July 19 has sparked industry-wide concerns. A faulty Falco...
 News
NewsResearchers Discover New Phishing Kit on the Dark Web
July 22, 2024 | SlashNext researchers uncovered the FishXProxy Phishing Kit on the dark web. This ki...
 News
NewsCrowdStrike vs. Microsoft: Who’s at Fault for the IT Outage?
July 19, 2024 | A global IT outage caused by a CrowdStrike update has led to debate over responsibil...
 News
NewsTips for Handling Cybersecurity Outages
July 19, 2024 | The CrowdStrike outage highlights key strategies for managing disruptions. Act swift...
 News
NewsFallout of Global Microsoft Crash Continues as Firms Assess Damage
July 19, 2024 | The Microsoft outage, triggered by a CrowdStrike update, disrupted critical systems ...
 News
NewsCrowdStrike Crash Raises Questions About Tech Dependency
July 19, 2024 | A flawed update from CrowdStrike caused widespread outages, highlighting the dangers...
 News
NewsIT Teams Scramble to Recover from CrowdStrike Incident as Officials Warn of Risks of Consolidation
July 19, 2024 | IT teams worldwide are rushing to fix systems after a faulty CrowdStrike update caus...
 News
NewsBuggy CrowdStrike EDR Update Crashes Windows Systems Worldwide
July 19, 2024 | A defective update to CrowdStrike Falcon Sensor caused mass IT outages globally, dis...
 Datasheet
DatasheetMOBILESOC®: Quickly mitigate risk and respond to threats from anywhere
Critical Start’s Android and iOS mobile app enables security teams to increase productivity, strea...
 News
NewsVoid Banshee Group Using Patched Zero-Day to Execute Infostealer
July 16, 2024 | APT group Void Banshee is exploiting a recently patched zero-day (CVE-2024-38112) to...
 News
NewsAs CISOs Grapple with the C-suite, Job Satisfaction Takes a Hit
July 15, 2024 | Research shows CISO job satisfaction is tied to their access to company management. ...
 News
NewsFishXProxy Phishing Kit Empowers Cybercriminals
July 11, 2024 | A new phishing toolkit, FishXProxy, is lowering the barrier for creating sophisticat...
 News
NewsFederal Cybersecurity Hiring: What More Needs to Be Done?
July 10, 2024 | The Biden administration launched the National Cyber Workforce and Education Strateg...
 News
NewsBlastRADIUS Vulnerability Exposes RADIUS Security Flaws
July 10, 2024 | Cybersecurity researchers discovered a critical vulnerability in RADIUS, a network a...
 News
NewsCISO Job Satisfaction Drops Due to Lack of C-Suite Access
July 17, 2024 | Research reveals CISO job satisfaction is tied to their access to company management...
 News
NewsEldorado Ransomware Targets Windows and Linux Networks
July 9, 2024 | Eldorado, a Ransomware-as-a-Service (RaaS), is hitting both Windows and Linux systems...
 News
NewsWhat to Tell the Board About Malware Analysis
July 9, 2024 | Malware analysis is crucial for cybersecurity, helping security teams understand mali...
 News
NewsEldorado Ransomware Targets VMware ESXi
July 9, 2024 | A new ransomware-as-a-service platform, Eldorado, targets Windows and VMware ESXi env...
 Quick Card
Quick CardVulnerability Prioritization for Leadership and Compliance
This is a solution quick card for Critical Start Vulnerability Prioritization, which helps businesse...
 Datasheet
DatasheetCritical Start Vulnerability Prioritization
This datasheet from Critical Start discusses their Vulnerability Prioritization solution, which enri...
 Quick Card
Quick CardEffective Ransomware Exposure Mitigation
This is a solution quick card for Critical Start Vulnerability Prioritization, which helps businesse...
 Quick Card
Quick CardVulnerability Prioritization for Vulnerability Management Engineers and Security Analysts
This is a solution quick card for Critical Start Vulnerability Prioritization, which helps engineers...
 News
NewsEldorado Ransomware: Emerging Threat Overview
July 8, 2024 | Explore Eldorado, a new ransomware-as-a-service (RaaS) group targeting VMware ESX ser...
 News
NewsSecurity Leaders Discuss Three Nation-State Campaigns
Menlo Security’s report details three sophisticated nation-state campaigns targeting financial...
 News
NewsReport: Organizations Prioritize Savings Over Client Privacy
July 5, 2024 | Bugcrowd’s latest report reveals that 1 in 3 security leaders believe many orga...
 News
NewsCritical Start: Managed Cyber Risk Reduction
July 5, 2024 | Critical Start introduces Quick Start Risk Assessments and expanded framework coverag...
 News
NewsSecurity Leaders Discuss Life360 Data Breach
July 2, 2024 | Life360 reported a data breach affecting its subsidiary, Tile, exposing client inform...
 News
News3 New State-Backed Gangs Target Govt Sectors with HEAT Attack Methods
July 2, 2024 | Menlo Security’s latest report uncovers three new state-backed cyber gangs using Hi...
 News
News14 Million OpenSSH Servers Exposed via Regression Flaw
July 1, 2024 | A critical remote code execution flaw (CVE-2024-6387) in OpenSSH on glibc-based Linux...
 News
NewsPhantom Secrets: The Hidden Threat in Code Repositories
July 1, 2024 | Aqua Security reveals that API tokens, credentials, and passkeys remain exposed in co...
 News
NewsMicrosoft Reveals AI Security Flaw That Threatens eCommerce and Financial Services
July 1, 2024 | Microsoft has discovered “Skeleton Key,” a security flaw in AI models tha...
 News
NewsCybersecurity Burnout: Costing Enterprises More Than Money
June 28, 2024 | Cybersecurity stress is rampant, with burnout costing U.S. businesses $626 million a...
 News
NewsPreventing Cyberattacks: The Role of Risk Profiling [Q&A]
June 28, 2024 | Randy Watkins, CTO at Critical Start, discusses the critical importance of cyber ris...
 News
NewsPolyfill Becomes a Supply-Chain Risk to 100,000 Websites
June 28, 2024 | A recent acquisition of the Polyfill domain by a Chinese company has turned it into ...
 News
NewsCyberattack Rate Surges as Novel Malware Growth Accelerates
June 28, 2024 | BlackBerry Limited’s latest Global Threat Intelligence Report reveals a sharp incr...

2024 Gartner® MDR Market Guide | Managed Detection and Response Services
What is the 2024 Gartner Market Guide for Managed Detection and Response Services? The 2024 Gartner ...
 Webinar
Webinar[On-Demand Webinar] Exposing Traditional MDR: The Hidden Flaws Putting Your Security at Risk
Are your current Managed Detection and Response (MDR) services truly protecting your organization? T...
 News
NewsCISOs Reveal Firms Prioritize Savings Over Long-Term Security
June 27, 2024 | Bugcrowd’s 2024 Inside the Mind of a CISO report highlights that 33% of security l...
 News
NewsThree Nation-State Campaigns Targeting Healthcare, Banking Discovered
June 27, 2024 | Researchers have uncovered three nation-state campaigns using advanced highly evasiv...
 News
NewsSecurity Budgets Grow, but Inefficiencies Persist
June 27, 2024 | Organizations are increasing their cybersecurity budgets but remain uncertain about ...
 News
NewsOnce Benign Polyfill.io Code Now Exposes 100k+ Websites to Attack
June 26, 2024 | Over 100,000 websites using Polyfill JS are now vulnerable to malicious redirects to...
 News
NewsNew RAT Digs into Android Phones to Steal Data and Encrypt Files – DICE Insights
June 24, 2024 | Outdated Android devices are under attack from “Rafel RAT,” a novel malw...
 News
NewsAndroid Users Warned of Rising Malware Threat From Rafel RAT
June 24, 2024 | Security researchers warn of Rafel RAT, a malware targeting Android devices. Check P...
 News
NewsThe Gately Report: Barracuda Networks CRO Wants New Business – DICE Insights
June 24, 2024 | Barracuda Networks’ new CRO, Geoffrey Waters, aims to drive new business and stren...
 News
NewsGetting Your Cybersecurity Career Started: Advice for Recent Tech Grads – DICE Insights
June 21, 2024 | Recent tech graduates face unique challenges and opportunities as they enter the cyb...
 eBook
eBookThreat Intelligence Report: New FakeBat Variant
Discover the intricacies of cyber threats with our latest Critical Start Cyber Threat Intelligence R...
 News
NewsSecurity Teams Leverage GenAI for Threat Detection and Response – TechStrong.AI
June 20, 2024 | Security teams are adopting generative AI (GenAI) to enhance threat detection and re...
 News
NewsHigh-Severity UEFI Vulnerability Affects Hundreds of Intel CPUs – Secure World Magazine
June 20, 2024 | A high-severity vulnerability in Phoenix Technologies’ SecureCore UEFI firmwar...
 News
NewsCybersecurity Worker Burnout Costing Businesses Big – Security Boulevard
June 19, 2024 | Medium to large enterprises face significant financial losses due to cybersecurity w...
 News
NewsWhy Teams Need a Strategy for Responding to AI-Driven Threats – SC Magazine
June 18, 2024 | As AI-driven cyber threats evolve, security teams must adopt advanced strategies to ...
 News
NewsWhy Teams Need a Strategy for Responding to AI-Driven Threats – SC Magazine
June 18, 2024 | As AI-driven cyber threats evolve, security teams must adopt advanced strategies to ...
 News
NewsA Comprehensive Roundup for Internet Safety Month – Hear from Industry Experts – VM Blog
June 18, 2024 | In honor of Internet Safety Month, VM Blog gathers insights from top industry expert...
 News
NewsLocation Tracker Firm Tile Hit by Data Breach, Hackers Access Internal Tools – Hack Read
June 14, 2024 | Millions of Tile users’ personal information may have been exposed in a data b...
 eBook
eBookSeeing is Securing: Leveraging CRITICALSTART® Asset Visibility to Protect Your Organization’s Critical Assets
Designed for cybersecurity professionals, including CISOs, IT managers, and security operations team...
 News
NewsChinese State-Sponsored Hackers Charged, Sanctions Levied by US – Dark Reading
March 25, 2024 | The US Department of Justice charged seven Chinese nationals linked to the APT31 th...
 News
NewsGovernment’s AI Plans Come into Focus with DHS, OMB Roadmaps – FedTech
June 13, 2024 | The Department of Homeland Security (DHS) and the Office of Management and Budget (O...
 News
NewsIT and Cybersecurity Jobs Are Converging: What It Means for Tech Pros – DICE Insights
June 13, 2024 | As technology evolves, IT and cybersecurity roles are merging, requiring tech profes...
 Webinar
Webinar[On-Demand Webinar] Beyond SIEM: Elevating Threat Protection with Seamless User Experience
In the realm of cybersecurity, staying ahead of threat actors can feel like a perpetual challenge, g...
 News
NewsNvidia Patches High-Severity Flaws in GPU Drivers – Dark Reading
June 12, 2024 | Nvidia has issued patches for high-severity vulnerabilities in its GPU drivers and v...
 News
NewsBlack Basta Ransomware Suspected of Exploiting Windows Zero-Day Flaw – Secure World Magazine
June 12, 2024 | Black Basta ransomware is believed to have exploited a Windows zero-day vulnerabilit...
 News
NewsHotel Check-in Kiosks Expose Guest Data, Room Keys – Dark Reading
June 7, 2024 | A vulnerability in Ariane Systems’ kiosk platform (CVE-2024-37364) allows attac...
 News
NewsHotel Check-in Kiosks Expose Guest Data, Room Keys – Dark Reading
June 7, 2024 | A vulnerability in Ariane Systems’ hotel check-in kiosks, impacting over 3,000 ...
 News
NewsThe Gately Report: SolarWinds Says Generative AI Not a ‘Scary Monster’ – Channel Futures
June 3, 2024 | SolarWinds’ SVP Krishna Sai emphasizes that generative AI is beneficial, not in...
 News
NewsPopular WordPress Plugins Leave Millions Open to Backdoor Attacks – Hack Read
June 3, 2024 | Fastly researchers discovered vulnerabilities in popular WordPress plugins, including...
 News
News39% of MSPs Adapting to New Technologies Is Their Biggest Challenge – Security Magazine
June 3, 2024 | A recent report reveals that 39% of Managed Service Providers (MSPs) find adapting to...
 eBook
eBookNavigate the Path to NIST CSF 2.0: Your Guide to Cyber Risk Reduction
The National Institute of Standards and Technology (NIST) has released version 2.0 of its Cybersecur...
 Webinar
Webinar[On-Demand Webinar] Mastering Cyber Risk Management: Five Critical Components for Success
Critical Start’s recent webinar, Mastering Cyber Risk Management: Five Critical Components for...
 News
NewsEPA Issues Urgent Alert for Water Utilities to Enhance Cyber Defenses – Secure World Magazine
May 22, 2024 | The EPA has issued an urgent alert for U.S. water utilities to strengthen cybersecuri...
 News
NewsNew AI Guides Outline Has Lessons for Tech and Cybersecurity Pros – DICE Insights
May 21, 2024 | New AI guidelines from NIST highlight risks and best practices for developing and dep...
 News
NewsMastering the Cybersecurity Tightrope: Risks and Threats in Modern Organizations – Cybersecurity Insiders
May 20, 2024 | George Jones of Critical Start delves into the importance of distinguishing between c...
 News
News2 D-Link Router Bugs Added to CISA’s Exploited Vulnerabilities Catalog – SC Magazine
May 18, 2024 | CISA has added two end-of-life D-Link routers to its Known Exploited Vulnerabilities ...
 News
NewsCISA’s ‘Vulnrichment’ Aims to Fix the NVD – Reversing Labs
May 15, 2024 | The U.S. Cybersecurity and Infrastructure Security Agency (CISA) launched the “...
 News
NewsStrategic Cyber Defense: Balancing Threat-Centric and Risk-Centric Approaches – CPO Magazine
May 15, 2024 | In cybersecurity, distinguishing between vulnerabilities, threats, and risks is cruci...
 News
NewsDell Data Breach Impacts 49 Million Customers – CPO Magazine
May 15, 2024 | Dell Technologies reported a data breach affecting 49 million customers, exposing per...
 News
NewsBacklogs at National Vulnerability Database prompt action from NIST and CISA – CSO Online
May 15, 2024 | NIST and CISA are addressing critical backlogs at the National Vulnerability Database...
 News
NewsCISA’s ‘Vulnrichment’ Program Enhances the National Vulnerability Database – ReversingLabs
May 15, 2024 | CISA launches the ‘vulnrichment’ program to enrich CVEs with critical met...
 Press Release
Press ReleaseCRITICALSTART® Named a Major Player in 2024 IDC MarketScape: Worldwide Emerging Managed Detection and Response Services
PLANO, TX, May 15, 2024 – Critical Start, a leading provider of Managed Detection and Response (MD...
 News
NewsGoogle Rushes to Patch Second Actively Exploited Chrome Zero-Day in a Week – Secure World Magazine
May 15, 2024 | Google released an emergency update for Chrome (CVE-2024-4761), an out-of-bounds writ...
 News
NewsGoogle Patches 6th Chrome Zero-Day of 2024, Three Days After Last One – SC Magazine
May 14, 2024 | Google released a patch for the sixth Chrome zero-day vulnerability of 2024 (CVE-2024...
 News
NewsDangerous Google Chrome Zero-Day Allows Sandbox Escape – Dark Reading
May 14, 2024 | Google released an emergency update for Chrome, addressing a zero-day vulnerability (...
 Press Release
Press ReleaseCRN 2024 Women of the Channel List Recognizes Five Critical Start Channel Executives
PLANO,TX, May 14, 2024 – Today, Critical Start, a leading provider of Managed Detection and Re...
 News
NewsAHA, H-ISAC Warn Hospitals About Black Basta Following Ascension Cyberattack – Healthcare IT News
May 13, 2024 | Following a major cyberattack on Ascension health system, the AHA and H-ISAC issued a...
 eBook
eBookSecuring Your Future: Take the Complexity Out of Vulnerability Management with Critical Start
Explore the transformative approach of Critical Start’s Vulnerability Management Services, des...
 Press Release
Press ReleaseCRITICALSTART® Expands Risk Assessments Coverage to Include Multiple Frameworks
PLANO, TX, May 8, 2024 – Today, Critical Start, a leading provider of Managed Detection and Re...
 Webinar
WebinarOn-Demand: Vulnerability Management’s Critical Role in Guarding Against Cyber Threats
Did you miss the live presentation of Vulnerability Management’s Critical Role in Guarding Against...
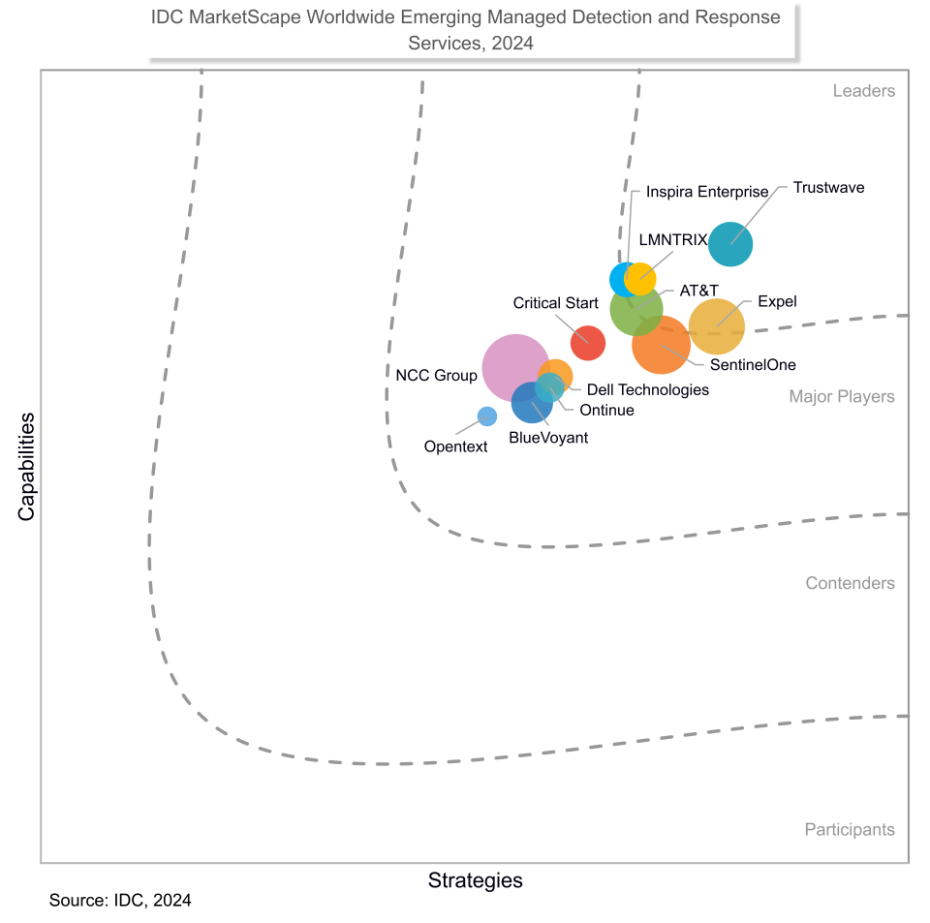 White Paper
White PaperIDC MarketScape: Worldwide Emerging Managed Detection and Response (MDR) Services 2024 Vendor Assessment
Download the free Excerpt on Worldwide Emerging Managed Detection and Response (MDR) Services 2024 V...
 eBook
eBookUnveiling the Myths–and Mastering the Dos and Don’ts–of Asset Visibility
Discover the critical role of asset visibility in bolstering cybersecurity with our eBook, “Th...
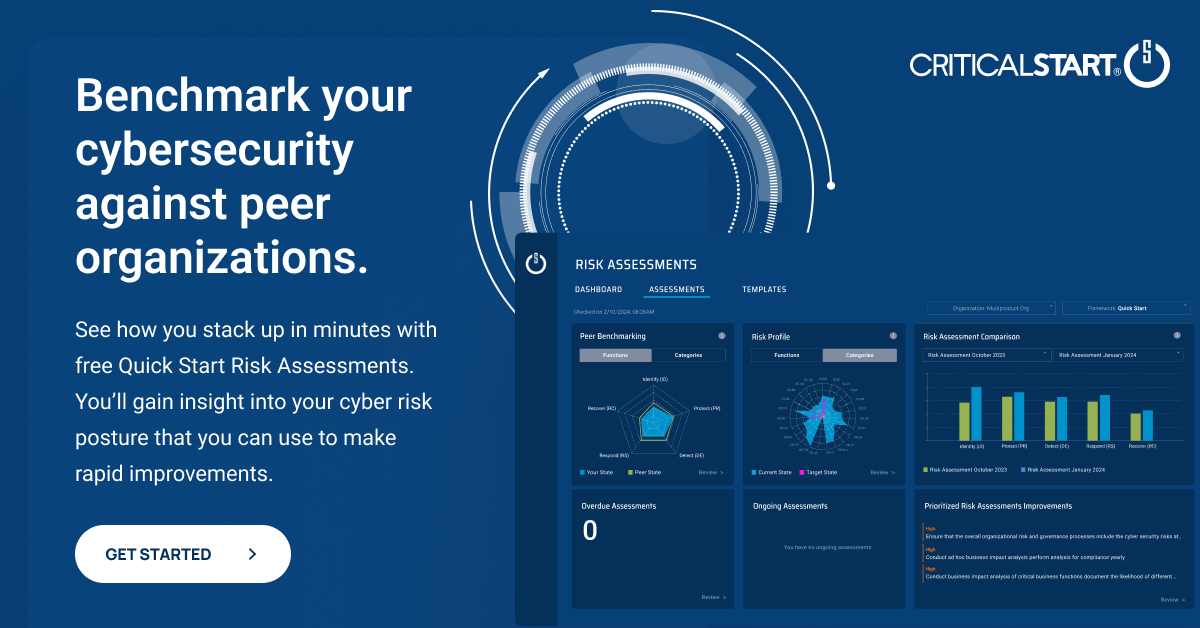 Press Release
Press ReleaseCRITICALSTART® Launches Free Peer Benchmarked Cyber Risk Assessments Tool Empowering Organizations to Evaluate and Enhance Defenses
PLANO, TX, May 7, 2024– Today, Critical Start, a leading provider of Managed Detection and Res...
 Press Release
Press ReleaseCritical Start Receives Three Cyber Defense Magazine 2024 Global InfoSec Award Wins
PLANO, TX, May 6, 2024 – Today at RSA Conference, Critical Start, a leading provider of Manag...
 Datasheet
DatasheetCritical Start Products and Services Overview
Get a 360 view of the products and services offered by Critical start. ...
 Datasheet
DatasheetCyber Risk Register Datasheet
As cyber risk management becomes an increasing focus, organizations are looking for a better way to ...
 eBook
eBookRisk Assessments: The Hidden Key to Continuous Security Improvement
In this exclusive eBook we dive into how Managed Cyber Risk Reduction (MCRR) can significantly boost...
 Press Release
Press ReleaseCritical Start Introduces Cyber Risk Register to Help Organizations Effectively Identify, Track and Reduce Cyber Risk
PLANO, TX, May 1, 2024 – Today, Critical Start, a leading provider of Managed Detection and Re...
 Datasheet
DatasheetSecurity Services for SIEM
Critical Start’s Security Services for SIEM combines Managed SIEM and MDR for SIEM to deliver ...
 Webinar
Webinar[On-Demand Webinar] Vulnerability Management’s Critical Role in Guarding Against Cyber Threats
Did you miss Critical Start’s webinar on Vulnerability Management? Watch the recap as Chris Ca...
 Press Release
Press ReleaseCritical Start Introduces Cybersecurity for Operational Technology (OT) with Upcoming Launch of Tailored MDR Service
PLANO, TX, April 24, 2024 – Today, Critical Start, a leading provider of Managed Detection and...
 Quick Card
Quick CardCritical Start Security Services for SIEM and Sumo Logic® Cloud SIEM
Critical Start offers a comprehensive solution that helps Sumo Logic SIEM customers achieve the full...
 News
NewsCISA Unveils Critical Infrastructure Reporting Rule – Security Boulevard
April 5, 2024 | CISA announced a new rule under the Cyber Incident Reporting for Critical Infrastruc...
 Datasheet
DatasheetCritical Start Managed Cyber Risk Reduction – The Next Evolution of MDR
Discover the key benefits, use cases, solution features, and services of Critical Start’s Managed ...
 News
NewsSecuring Secrets: The State Department’s Cyber Hunt – The CyberWire Daily
April 4, 2024 | The State Department is investigating an alleged cyber breach while the FCC consider...
 News
NewsMalicious Latrodectus Downloader Picks Up Where QBot Left Off – Dark Reading
April 4, 2024 | Researchers have discovered a new malware downloader named “Latrodectus,”...
 News
News‘Latrodectus’ Uses Sandbox Evasion Techniques to Launch Malicious Payloads – SC Magazine
April 4, 2024 | Researchers from Proofpoint have identified a new malware called “Latrodectus,...
 News
NewsSophos Reveals Ransomware Attacks Are Now Targeting Backups – Hackread
April 3, 2024 | A Sophos report reveals ransomware attackers are increasingly targeting backups, mak...
 News
NewsCVE and NVD – A Weak and Fractured Source of Vulnerability Truth – Security Week
April 3, 2024 | The CVE List and National Vulnerability Database (NVD) are criticized for not being ...
 News
NewsWhy the FCC’s Cybersecurity Labeling Program Benefits IoT Systems – SC Magazine
April 3, 2024 | The FCC’s new voluntary cybersecurity labeling program for IoT devices aims to...
 News
NewsRansomware, Junk Bank Accounts: Cyber Threats Proliferate in Vietnam – Dark Reading
April 2, 2024 | Vietnam’s rapid economic growth has led to a surge in cybercrime, including ra...
 News
NewsMicrosoft Copilot for Security: The MSSP Opportunity – MSSP Alert
April 2, 2024 | Microsoft’s release of Copilot for Security integrates AI into its security of...
 News
NewsData Security Fears: Congress Bans Staff Use of Microsoft’s AI Copilot – Hackread
April 1, 2024 | Due to data security concerns, the US House of Representatives has banned staff from...
 News
NewsUS House Forbids Staff Members from Using AI Chatbot Microsoft Copilot – SC Magazine
April 1, 2024 | The US House of Representatives has banned staff members from using Microsoft’...
 News
NewsLet’s Celebrate World Backup Day 2024 – Hear From Industry Experts – VMBlog
April 1, 2024 | As World Backup Day 2024 approaches, industry experts share insights on the importan...
 Webinar
WebinarOn-Demand: Navigating the New Era of Cybersecurity with NIST CSF 2.0
Did you miss the live presentation of Navigating the New Era of Cybersecurity with NIST CSF 2.0 on M...
 News
NewsCritical Infrastructure May Be the Subject of Disruptive Cyberattacks – Security Magazine
March 27, 2024 | A recent White House letter warns that critical infrastructure, especially water an...
 News
NewsStrelaStealer Malware Hits More Than 100 EU and US Organizations – SC Media
March 25, 2024 | A new wave of StrelaStealer malware campaigns has impacted over 100 organizations i...
 News
NewsChinese State-Sponsored Hackers Charged, Sanctions Levied by US – Dark Reading #3
March 25, 2024 | The US Department of Justice charged seven Chinese nationals linked to the APT31 th...
 Quick Card
Quick CardPCI DSS 4.0 Requirement 11.3 – Vulnerability Scanning
In this Use Case, you will learn how the Critical Start Vulnerability Management Service (VMS) with ...
 Datasheet
DatasheetVulnerability Management Service
Take the burden out of vulnerability management while continuously reducing cyber risk Critical Star...
 News
NewsRevolutionize cybersecurity with proactive vulnerability intelligence – SC Media
March 18, 2024 | In her article for SC Media, Callie Guenther, Senior Manager of Cyber Threat Resear...
 Press Release
Press ReleaseCritical Start Achieves Bronze Victory in 20th Annual 2024 Globee® Cybersecurity Awards
Plano, TX, March 14, 2024 – Critical Start, a leading provider of Managed Detection and Response...
 Webinar
WebinarOn-Demand: When MDRs See No Evil with Critical Start and Lenovo
During this recording, you’ll learn how Lenovo MDR powered by Critical Start provides greater ...
 Quick Card
Quick CardEnhanced Security with Vulnerability Assessment & Pen Testing
Explore how Critical Start’s Vulnerability Assessment & Penetration Testing Services stren...
 Press Release
Press ReleaseCritical Start Finishes Fiscal Year with Strong Business Growth and New Approach to Cyber Risk Reduction
Plano, TX, March 12, 2024 – Today, Critical Start, a leading provider of Managed Detection and Res...
 Webinar
Webinar[On-Demand Webinar] Decoding the Shadows: Proactive Cybersecurity Through Managed Threat Intelligence
Watch the recording of our latest webinar as Callie Guenther guides you through: Watch recording now...
 Datasheet
DatasheetCritical Start Managed XDR Threat Detection for User, Cloud and Application Log Sources
Learn how Managed XDR empowers organizations of all sizes to stay ahead of threats beyond the endpoi...
 Video
VideoCritical Start MDR: Welcome To Your New World
Video Transcript: It’s time for a world where no security threat goes undetected. A world whe...
 Use Cases
Use CasesCritical Start NIST 800-171 Rev. 2 Risk Assessment
Leverage the NIST SP 800-171 Rev. 2 assessment to assess compliance levels of security measures safe...
 Use Cases
Use CasesCritical Start CIS Critical Security Controls v8 Risk Assessment
The CIS Critical Security Controls v8 assessment offers a cybersecurity baseline to protect companie...
 News
NewsBenefits And Cautions Of Aligning With Cybersecurity Frameworks – Forbes Council Post
February 13, 2024 | In his Forbes Council Post, Randy Watkins, CTO of Critical Start, emphasizes the...
 Press Release
Press ReleaseDwayne Myers of Critical Start Recognized as a 2024 Channel Chief
Today, Critical Start, a leading provider of Managed Detection and Response (MDR) cybersecurity solu...
 Datasheet
DatasheetCyber Operations Risk & Response™ platform
See how the Critical Start Cyber Operations Risk & Response™️ (CORR) platform integrates wit...
 Quick Card
Quick CardMDR services from Critical Start powered by SentinelOne Singularity™
Using the power of SentinelOne, Critical Start enables customers to centralize, ingest, and correlat...
 Datasheet
DatasheetCritical Start Risk Assessments
Knowing your organization’s cyber risk and proving the value of your security tools is imperat...
 Webinar
Webinar[On-Demand Webinar] Navigating the Cybersecurity Slopes: Unveiling the CRU’s Innovative Approach
Watch the recording now! In the realm of detection engineering and threat intelligence, our CRU (Cyb...
 White Paper
White PaperProtect Your Organization’s Future With A Proactive Cyber Risk Management Strategy
Forrester Opportunity Snapshot: A Custom Study Commissioned by Critical Start Read the Forrester-com...
 Datasheet
DatasheetCyber Risk Dashboard
Providing a holistic perspective for continuously assessing, monitoring, and mitigating your cyber r...
 Webinar
WebinarHunting for Cyber Threats
Watch the recording now: Explore the ever-changing threat landscape and delve into the art of securi...
 Webinar
Webinar[On-Demand Webinar] Security and Sneakers
Watch the recording now: Lace up and get ready for a virtual event, with Critical Start’s Sr. Secu...
 Webinar
WebinarWhen MDRs See No Evil: How to Protect Your Organization from Undetected Threats
Watch Jim Rohde on-demand! Threats can evade detection when endpoint visibility gaps prevent your se...
 Webinar
Webinar[On-Demand Webinar] Strategic Cyber Risk Management: A Proactive Approach for Sustainable Security
Today’s security and risk leaders can no longer afford to be solely reactive with their cyber risk...
 Press Release
Press ReleaseCritical Start Recognized for Two Best Places to Work Awards
PLANO, TX, January 23, 2024 – Today, Critical Start, a leading provider of Managed Detection and R...
 Solutions Brief
Solutions BriefAchieve Full Microsoft Sentinel Operating Potential
How Managed Detection & Response (MDR) Services and Microsoft Security Consulting Services will ...
 Press Release
Press ReleaseNew Study Reveals 81% of Enterprises Have an Inadequate Approach to Cyber Risk Management
PLANO, TX, January 17, 2024 – Today, Critical Start, a leading provider of Managed Detection and R...
 Research Report
Research ReportProtect Your Organization’s Future with a Proactive Cyber Risk Management Strategy
Security and risk teams face the challenge of ensuring their current cyber risk management efforts a...
 White Paper
White PaperShifting Paradigms: Redefining Cyber Risk Assessments for Tangible Outcomes
As the cyber threat landscape evolves rapidly, how can you ensure your risk assessments provide acti...
 Press Release
Press ReleaseCritical Start Redefines Cyber Risk Assessments with Peer Benchmarking and Prioritization Engine to Help Organizations Improve Their Security Posture
PLANO, TX, Jan. 11, 2024 – Today, Critical Start, a leading provider of Managed Detection and Resp...
 Press Release
Press ReleaseCritical Start Launches Asset Visibility to Ensure Managed Detection and Response Has Full Signal Coverage for a More Effective Approach to Reducing Cyber Risk
PLANO, TX, January 9, 2024 – Today, Critical Start, a leading provider of Managed Detection an...
 Solutions Brief
Solutions BriefProtection Beyond the Endpoint: SIEM + XDR
Learn how Critical Start’s MDR and Microsoft Security Consulting Services strengthen your SIEM...
 Quick Card
Quick CardManaged Detection and Response (MDR) services from Critical Start powered by CrowdStrike Falcon
Critical Start integrates with CrowdStrike Falcon to offer a full Managed Detection and Response (MD...
 Customer Stories
Customer StoriesPackaging Manufacturer Saves Time with MDR and Microsoft Security Solutions
A packaging manufacturer needed more visibility into data, faster response times, and their own Secu...
 News
NewsExploitation Accounts For 29% of Education Sector Attacks
October 11, 2023 | The education sector is increasingly targeted by cyber threats, with 29% of attac...
 News
NewsHacker Advocates Turning Tracking Tables on Law Enforcement
October 10, 2023 | A robotics hacker, Alan Meekins (Nullagent), created RFParty, a service enabling ...
 News
News‘Predator Files’ Report Prompts Call for Worldwide Ban on Spyware
October 9, 2023 | Amnesty International reported a series of Predator spyware attacks targeting civi...
 News
NewsAWS Warns of ‘ShellTorch’ Issue Affecting Code Related to AI Models
October 3, 2023 | Amazon Web Services (AWS) has issued a warning regarding a vulnerability affecting...
 News
NewsEU Urged to Reconsider Cyber Resilience Act’s Bug Reporting within 24 Hours
October 3, 2023 | A group of 56 cybersecurity leaders, including professionals from ESET, Rapid7, th...
 News
NewsCisco Warns of Attempted Exploitation of Zero-Day in VPN Software
October 2, 2023 | Cisco has identified and released patches for a vulnerability (CVE-2023-20109) aff...
 News
NewsMOVEit Developer Patches Critical File Transfer Bugs
September 29, 2023 | Progress Software has issued patches for critical vulnerabilities in its WS_FTP...
 News
NewsUS and Japan Warns That Chinese-Linked Hacking Group is Targeting Routers
September 27, 2023 | The U.S. and Japanese governments have issued a joint advisory warning about Bl...
 News
NewsVulnerability in Popular ‘libwebp’ Code More Widespread Than Expected
September 27, 2023 | A previously disclosed vulnerability, first tracked as CVE-2023-4863 and later ...
 News
NewsApple Issues Emergency Patches on Three New Exploited Zero-Days
September 22, 2023 | Apple has patched three zero-day vulnerabilities actively exploited in the wild...
 News
NewsOkta Agent Involved in MGM Resorts Breach, Attackers Claim
September 15, 2023 | The threat group ALPHV, responsible for the recent cyberattacks on MGM Resorts ...
 News
NewsTactics of MGM-Caesars Attackers Were Known for Several Months
September 14, 2023 | The recent ransomware attacks on MGM International and Caesars Entertainment by...
 News
NewsMGM Resorts Cyberattack Hobbles Las Vegas Strip Operations
September 12, 2023 | MGM Resorts is dealing with a cyberattack that has left its hotel operations, e...
 News
NewsCyber-criminals “Jailbreak” AI Chatbots For Malicious Ends
September 12, 2023 | A new trend called “jailbreaking” has emerged in the world of AI ch...
 News
News‘Evil Telegram’ Spyware Campaign Infects 60K+ Mobile Users
September 8, 2023 | Cybercriminals are exploiting the acceptance of Telegram “mods” in t...
 News
NewsCyber-criminals Exploit GPUs in Graphic Design Software
September 8, 2023 | Cisco Talos researchers uncovered a cryptocurrency-mining scheme targeting graph...
 Webinar
WebinarThe State of Cybersecurity: 2023 Trends and 2024 Predictions
The looming threats in 2024 encompass various dimensions, from the sophistication of Cybercriminals,...
 Webinar
WebinarGet Cozy with Lenovo ThinkShield MXDR Powered by Critical Start
Sit back and take a break from the holiday craze and watch the recording of our fireside chat with C...
 Webinar
WebinarThreat Protection Delivered Roadshow with Microsoft and Critical Start
Critical Start’s Chief Technology Officer, Randy Watkins and Microsoft’s Technical Speci...
 White Paper
White PaperYou Can’t Protect What You Can’t See
Concerned your MDR service isn’t detecting all the threats your organization is exposed to? You...
 Press Release
Press ReleaseCritical Start and Microsoft Kick-off Threat Protection Delivered Roadshow
PLANO, TX, November 28, 2023 – Today, Critical Start, a leading provider of Managed Detection ...
 Webinar
Webinar[On-Demand Webinar] Hunting for Threats: Lock & Load Your Organization with Managed Detection & Response
Explore the ever-changing threat landscape and delve into the art of securing your organization agai...
 Press Release
Press ReleaseCritical Start is a Proud Participant in the Microsoft Security Copilot Partner Private Preview
PLANO, TX, November 15, 2023 – Today, Critical Start, a leading provider of Managed Detection ...
 Datasheet
DatasheetManaged Detection and Response Services from Critical Start for Cortex XDR Service
Reduce risk exposure with robust endpoint security protection and advanced cyber threat prevention b...
 Webinar
WebinarSecurity and Sneakers
Lace up and get ready for the on-demand recording of Security and Sneakers, with Critical Start̵...
 Solutions Brief
Solutions BriefProtect against user account attacks
How Managed Detection & Response (MDR) Services and Microsoft Security Consulting Services can h...
 Solutions Brief
Solutions BriefRationalize the Value of Cybersecurity
Not seeing the key security metrics you need to justify cybersecurity spend? Learn how MDR services ...
 Quick Card
Quick CardCritical Start Managed Detection and Response (MDR) Services for Palo Alto Networks® Cortex® Platforms
Critical Start MDR helps Palo Alto Networks Cortex clients reduce risk, mitigate breaches, and stop ...
 Quick Card
Quick CardIncident Response Monitoring
Learn more about our 24x7x365 Incident Response (IR) Monitoring services that use global and customi...
 Press Release
Press ReleaseCritical Start Named Winner of the Coveted Top InfoSec Innovators Awards for 2023
Critical Start recognized as the Most Innovative Managed Detection and Response provider in Cyber De...
 Quick Card
Quick CardTop 10 Capabilities Checklist
Learn the top questions to ask and capabilities to evaluate when selecting an MDR provider...
 eBook
eBookH2 2023 Cyber Threat Intelligence Threat Report
Cyber threats are constantly evolving and the threat landscape is everchanging. How do you know whic...
 Press Release
Press ReleaseNew Cyber Threat Intelligence Report from Critical Start Highlights Prominent Threats and Emerging Cybersecurity Trends with Implications Spanning Multiple Industries
PLANO, TX, October 11, 2023 – Today, Critical Start, a leading provider of Managed Detection a...
 eBook
eBookMaximize the Value of Your Microsoft Security Investment and Unlock Your Security Potential
What You’ll Learn In this guide, learn how you can unlock your organization’s security p...
 Solutions Brief
Solutions BriefMaximize the Value of Microsoft Security
Maximize the value of Microsoft Security with MDR Services and Microsoft Security Consulting. Read t...
 Webinar
WebinarEat Risk for Breakfast: Pancakes and Proactive Security
Watch Critical Start’s CSO, Jordan Mauriello, as he delves into the intricacies of monitoring risk...
 White Paper
White PaperCritical Start Learning Objective: Kerberoasting
Kerberoasting is an attack that targets enterprise Windows environments. Threat actors that have acc...
 Datasheet
DatasheetCritical Start Managed Detection and Response (MDR) Services for Microsoft Security
Critical Start provides deep integration with the Microsoft Security suite to detect every event, re...
 News
NewsNorth Korean Hackers Target Security Researchers — Again
September 7, 2023 | For the second time in the last few years, North Korean state-sponsored attacker...
 News
NewsAttackers Leverage Windows Advanced Installer to Drop Cryptocurrency Malware
September 7, 2023 | Advanced Installer, a legitimate windows tool, is being hijacked by threat actor...
 Webinar
Webinar[On-Demand Webinar] The Power of Risk Assessment: Increasing Cyber Risk Posture with Peer Benchmarking
As a security leader, you understand the importance of effective cyber risk management. The challeng...
 News
NewsWhy Instagram Threads is a Hotbed of Risks for Businesses
September 4, 2023 Instagram’s new Threads is already proving to be a target for fraud and abus...
 News
NewsThe Vulnerability Crisis: Safeguarding PII in Web Apps
August 29, 2023 Web apps that contain Personally Identifiable Information (PII) are prime targets fo...
 Webinar
WebinarThe Next Evolution of MDR: Cyber Risk Reduction, Confidence, and Coffee
Watch Critical Start’s CTO, Randy Watkins, as he discusses the evolution of the cybersecurity ...
 News
NewsCritical Start Report: Most Organizations Struggle to Understand Their Cyber Risk
August 28, 2023 Learn the key findings in Critical Start’s new Cyber Risk Landscape Peer Repor...
 News
NewsNew malware from North Korea’s Lazarus used against healthcare industry
August 25, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, discusse...
 News
NewsXLoader MacOS Malware Variant Returns With OfficeNote Facade
August 23, 2023 Critical Start’s Callie Guenther, Sr. Manager Cyber Threat Research, discussed...
 News
NewsSecurity leaders report misalignment of investments and risk reduction
August 23, 2023 Critical Start’s Cyber Risk Landscape Peer Report was featured in Security Mag...
 Press Release
Press ReleaseCritical Start Research Uncovers 66% of Businesses Lack Understanding of Their Cyber Risks
New Cyber Risk Landscape Peer Report explores unique security challenges confronting businesses toda...
 Research Report
Research ReportCritical Start Cyber Risk Landscape Peer Report
Security leaders are under increasing pressure to show the amount of risk their organization is acce...
 Webinar
Webinar[On-Demand Webinar] Beyond the Endpoint: Strengthening Cybersecurity with Critical Start Managed XDR
In the swiftly changing world of cybersecurity, proactively staying ahead of threats is paramount. T...
 Press Release
Press ReleaseCritical Start Announces Risk Assessments for Enhanced Cybersecurity Visibility
PLANO, TX, August 10, 2023— Today, Critical Start, a leading provider of Managed Detection and...
 News
NewsBlack Hat USA: Cybersecurity Concerns Amid Big Techs’ AI, ChatGPT ‘Race’
Channel Futures highlights Critical Start’s MCRR launch and new Vulnerability Prioritization o...
 Press Release
Press ReleaseCritical Start Transforms the Security Landscape with Managed Cyber Risk Reduction
New proactive approach fuses continuous cyber risk monitoring platform with human-led risk and secur...
 Press Release
Press ReleaseCritical Start Announces New Vulnerability Prioritization Offering
PLANO, TX, August 8, 2023 – Today, Critical Start, a leading provider of Managed Detection an...
 News
NewsRansomware attack on Prospect Medical Holdings takes down hospital systems in 4 states
August 7, 2023 Critical Start’s CTO, Randy Watkins, was featured in SC Magazine discussing the...
 News
NewsCloud Providers Becoming Key Players in Ransomware, Halcyon Warns
August 2, 2023 Critical Start’s Ian Todd, detection engineer, discussed the rise of C2Ps with ...
 News
NewsCyber Risk Confidence Index Reveals Skepticism of Mitigation Strategies
Critical Start’s Cyber Risk Confidence Index was featured in Secure World Read full article...
 Press Release
Press ReleaseCritical Start Research Reveals 66% of Cybersecurity Leaders Lack a High Degree of Confidence in the Effectiveness of Their Current Cyber Risk Mitigation Strategies
Newly released Cyber Risk Confidence Index signals desire for greater alignment between cyber protec...
 Research Report
Research Report2023 Cyber Risk Confidence Index
Critical Start recently surveyed 501 U.S.-based IT security leaders at organizations ranging from 2,...
 News
NewsAs ‘hot zero-day summer’ rolls on, experts think this might be the new normal
August 1, 2023 Critical Start’s CISO, George Jones, spoke with SC Magazine on the spike in zer...
 News
NewsStress Test: IT Leaders Strained by Talent Shortage, Tech Spend
July 19, 2023 Critical Start’s CISO, George Jones, discusses IT talent shortage with Informati...
 News
NewsCisco Nexus 9000 Users Must Disable Encryption to Dodge Vuln
July 17, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, discussed ...
 News
NewsWhat Does the Patchless Cisco Vulnerability Mean for IT Teams, CIOs?
July 14, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, provided i...
 News
NewsEight steps organizations can take after news of a state-sponsored cyberattack
July 14, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, wrote a gu...
 News
NewsMastodon Patches 4 Bugs, but Is the Twitter Killer Safe to Use?
July 11, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, discussed ...
 Press Release
Press ReleaseCritical Start Appoints Clifford Chiu and Edna Conway to its Board of Directors
Plano, TX, July 11, 2023 – Critical Start, a leading provider of Managed Detection and Respons...
 News
NewsA Cybersecurity Wish List Ahead of NATO Summit
July 10, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, was featur...
 News
News5 ways to prepare a new cybersecurity team for a crisis
July 10, 2023 Is your cybersecurity team ready for a crisis? Critical Start’s CISO, George Jon...
 News
NewsNew vulnerability in Cisco’s Nexus switch could allow attackers to modify encrypted traffic
July 6, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, discussed C...
 News
NewsNagoya Port Faces Disruption After Ransomware Attack
July 5, 2023 In response to the Nagoya Port ransomware attack, Critical Start’s Sr. Manager, C...
 News
NewsCybersecurity Certifications: Which Matter for Tech Pros
July 5, 2023 Should tech pros prioritize cybersecurity certifications? Critical Start’s CISO, ...
 News
NewsRussian Spies, War Ministers Reliant on Cybercrime in Pariah State
June 28, 2023 What’s the future of Russia cybercrime? Critical Start’s Callie Guenther, ...
 News
NewsSecurity leaders discuss NSA guide to mitigate BlackLotus threat
June 28, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, was featur...
 Webinar
Webinar[On-Demand Webinar] Why Threat Detection isn’t Your Next DIY Project
You know what they say, “If you want it done right, you’ll just have to augment your existing cy...
 Press Release
Press ReleaseCritical Start Expands Global Footprint with New Offices in the United States and India
Plano, TX, June 26, 2023 – Today, Critical Start, a leading provider of Managed Detection and ...
 News
NewsCybersecurity Career Advice for New Tech Grads
June 23, 2023 Critical Start’s CISO, George Jones, shared vital career advice for new tech gra...
 News
NewsNew strain of JavaScript dropper delivers Bumblebee and IcedID malware
June 22, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, offers com...
 News
NewsDeep Instinct uncovers new JavaScript-based malware dropper
June 22, 2023 Silicon Angle discussed the new JavaScript-based malware dropper with Critical Start&#...
 News
NewsLockBit Developing Ransomware for Apple M1 Chips, Embedded Systems
June 22, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, discussed ...
 News
NewsWho Is Responsible for Identity Threat Detection and Response?
June 21, 2023 Identity threat detection and response (ITDR) programs are vitally important for organ...
 News
NewsFulfilling Expected SEC Requirements for Cybersecurity Expertise at Board Level
June 20, 2023 Critical Start’s CTO, Randy Watkins, spoke with Security Week on the importance ...
 News
NewsUS Investors Sniffing Around Blacklisted NSO Group Assets
June 19, 2023 Critical Start’s Callie Guenther, Sr. Manager, Cyber Threat Research, discussed ...
 News
NewsCISOs Expect Stable IT Security Budgets in 2023
June 15, 2023 A recent survey identified 200 CISOs’ and IT Decision Makers’ expectations...
 News
NewsReport highlights key threats disrupting businesses
June 13, 2023 Article in Security Magazine featuring Critical Start’s H1 2023 Cyber Threat Intelli...
 News
NewsCISA’s new Binding Operational Directive. Encouraging ICS security news. Cybercrime notes. Industry advice for the White House.
June 13, 2023 Cyber Wire’s daily briefing, Featuring Critical Start’s H1 2023 Cyber Threat I...
 News
NewsThreat Intel Report: The Top 10 Cybersecurity Threats of H1 2023
June 13, 2023 Article in Enterprise Security Tech featuring Critical Start’s H1 2023 Cyber Thr...
 Press Release
Press ReleaseCritical Start Unveils Mid-Year Cyber Threat Intelligence Report Highlighting Key Threats Disrupting Businesses
Report finds two-step phishing attacks increasing; Beep malware top of mind for organizations; state...
 eBook
eBookH1 2023 Cyber Threat Intelligence Threat Report
Cyber threats are constantly evolving and the threat landscape is everchanging. How do you know whic...
 News
NewsOrganizations Urged to Address Critical Vulnerabilities Found in First Half of 2023
June 9, 2023 Several noteworthy vulnerabilities were discovered in the First Half of 2023. Critical ...
 Customer Stories
Customer StoriesHealthcare IT Team Rests Easy with Increased Managed Detection and Response Coverage
A small healthcare security team did not have 24/7/365 coverage over weekends and holiday breaks. Le...
 Press Release
Press ReleaseNew Critical Start Managed XDR Reduces Cybersecurity Risk Through Improved Visibility, Rapid Delivery, and Enhanced Security
PLANO, TX, June 6, 2023 – Today, Critical Start, a leading provider of Managed Detection and Respo...
 News
NewsShould You Trust Cybersecurity Certifications?
June 6, 2023 More organizations are investing in cybersecurity certifications, but do they enable th...
 Webinar
Webinar[On-Demand Webinar] MDR Providers Decoded: Evaluating the Top 10 Capabilities your Provider Needs
Managed Detection and Response (MDR) services provide organizations with real-time threat detection,...
 News
NewsBlackCat ransomware takes control of protected computers via new kernel driver
May 23, 2023 A new kernel driver was recently discovered in the BlackCat ransomware through several ...
 News
NewsHackers Intercept USPS Workers’ Paychecks in Direct Deposit Scam
May 22, 2023 Hundreds of United States Postal Service (USPS) workers fell victim to a cyber attack w...
 News
NewsKey Strategies for Tackling Third-party Software Vulnerabilities
May 22, 2023 Critical Start’s Chief Technology Officer (CTO), Randy Watkins, spoke with ITPro ...
 News
News10 MDR Security Companies Making Moves In 2023 (So Far)
May 18, 2023 Critical Start was included as one of 10 MDR security vendors making moves so far in 20...
 News
NewsCybersecurity Consultant: Tech Career Path With Room For Growth
May 18, 2023 DICE Insights interviewed Critical Start’s Chief Information Security Officer (CI...
 Press Release
Press ReleaseCRN 2023 Women of the Channel List Recognizes Six Critical Start Channel Leaders
Critical Start’s Female Channel Executives Recognized by CRN’s 2023 Women of the Channel...
 Webinar
Webinar[On-Demand Webinar] Cyber Threat Intelligence 101 Part 2: Building and Maturing Your Program
Getting information on recent vulnerabilities, malware and breaches is a priority – but is a const...
 Press Release
Press ReleaseCritical Start Wins Global InfoSec Award for Next Gen MDR at RSA Conference 2023
Critical Start recognized as leading innovator in Managed Detection and Response for its approach to...
 Press Release
Press ReleaseCritical Start Reveals Top 10 Capabilities to Consider When Selecting an MDR Provider
Top cybersecurity company unveils MDR capabilities that maximize cyber risk reduction Plano, TX, Apr...
 White Paper
White PaperMDR Providers Decoded: A Comprehensive Guide to Evaluating the Top 10 Capabilities Your Provider Needs
Managed Detection and Response is your last line of defense against business disruption and loss, so...
 Press Release
Press ReleaseCritical Start Announces Partnership with Lenovo™ to Enhance Digital Workplace Solutions
Plano, TX, April 24, 2023 — Critical Start, a leading provider of Managed Detection and Response (...
 Press Release
Press ReleaseCritical Start Announces Expansion of its Security Services for SIEM with Sumo Logic®
New partnership provides Critical Start and Sumo Logic customers with valuable insights to help mana...
 Press Release
Press ReleaseCritical Start Closes Fiscal Year with Accelerated Growth Amid Sharp Rise in Demand for its Technology-Based Approach to MDR
Company Names New Chief Marketing Officer and New Chief Product Officer Plano, TX, April 12, 2023 �...
 News
NewsIT Auditor: Good Entry-Level Position for a Cybersecurity Career?
April 11, 2023 Critical Start’s Chief Information Security Officer (CISO), George Jones, was f...
 White Paper
White PaperBuyer’s Guide for MDR Services for Microsoft Sentinel
What You’ll Learn In this guide, you will learn the criteria of how to maximize the performanc...
 Webinar
Webinar[On-Demand Webinar] Cyber Threat Intelligence 101: Supporting Business Goals and Metrics that Matter
Join our Critical Start Cyber Threat Intelligence expert as she lays out what it takes to build and ...
 Press Release
Press ReleaseCritical Start Spotlighted in the 2023 CRN® Partner Program Guide for Second Year in a Row
Company recognized as the first channel only MDR Plano, TX, March 27, 2023 — Critical Start, a lea...
 News
NewsDocument, document, document: How to keep patching going when the patch pro leaves
March 22, 2023 Critical Start’s Chief Technology Officer (CTO), Randy Watkins, discussed with ...
 Solutions Brief
Solutions BriefIncrease Cyber Risk Awareness to Strengthen Your Security Posture
Do you have limited visibility into key security metrics? Metrics are essential in establishing the ...
 White Paper
White PaperBest Practices for Integrating your SOC Team with MDR Services
What You’ll Learn This white paper explores how organizations that have decided to enlist the ...
 News
NewsCEO of Plano’s Critical Start Discusses International Expansion and More
February 13, 2023 Our CEO Rob Davis sat down with the Dallas Business Journal to discuss Critical St...
 Research Report
Research Report2023 Gartner® Market Guide for Managed Detection and Response Services
Critical Start is recognized in the 2023 Gartner Market Guide for Managed Detection and Response Ser...
 Solutions Brief
Solutions BriefOptimize Your Security Tools’ Detection & Operational Effectiveness
Are you concerned about gaps in your threats coverage and managing multiple security tools? Learn ho...
 Solutions Brief
Solutions BriefMeasure Key Operational Metrics to Continuously Improve Your Security Program
Do you have sufficient data to measure the performance of your security program? With increasing pre...
 Press Release
Press ReleaseDwayne Myers of Critical Start Honored as a 2023 CRN Channel Chief
Plano, TX, February 8, 2023 — Channel leader makes prestigious list for second time — Critical S...
 Press Release
Press ReleaseCritical Start Announces Availability of Managed Detection and Response Service for Trend Micro™ Vision One™
Plano, TX, January 25, 2023 – Today, Critical Start, a leading provider of Managed Detection and R...
 eBook
eBook2023 Threat Intelligence Guide
Stay One Step Ahead of Emerging Threats: Your 2023 Threat Intelligence Guide is Here! A cyberattack ...
 Infographics
InfographicsTop Threat Predictions for 2023
Check out our top 5 threat predictions for 2023, and how Critical Start can simplify breach preventi...
 Infographics
InfographicsCybersecurity Lessons Learned in 2022
Check out our 3 main lessons learned from cybersecurity trends in 2022 and how they can be leveraged...
 Webinar
WebinarAchieve the Full Operating Potential of Your SIEM
Learn how you can achieve the full operating potential of your SIEM while maximizing its value, with...
 Press Release
Press ReleaseCritical Start Recognized with Microsoft Verified Managed XDR Solution Status
Plano, TX, December 6, 2022 — Critical Start, a leading provider of Managed Detection and Response...
 News
NewsTop 100 CEOs speak from the heart about what leadership means to them
November 27, 2022 The Dallas Morning News featured Critical Start’s CEO, Rob Davis, among the ...
 Press Release
Press ReleaseCritical Start Ranked 11th in Midsize Companies Category in The Dallas Morning News Top 100 Places To Work for 2022
Plano, TX, November 15, 2022 — Critical Start, a leading provider of Managed Detection and Respons...
 eBook
eBook2022 MITRE ENGENUITY™ ATT&CK® Evaluations for Managed Services
We publish this paper as an educational asset, not a marketing vehicle. We share our findings here i...
 Webinar
Webinar[On-Demand Webinar] Domain Expert Series Episode 2 | Risk: How to Assess and Manage It
In this second webinar episode, we discuss how to conduct a risk assessment and develop a management...
 Infographics
InfographicsThe Importance of Resolving Every Alert
This infographic shows the importance of detecting and remediating the entire kill chain, or risking...
 Press Release
Press ReleaseCritical Start Launches New Managed SIEM Service
PLANO, Texas, Nov. 1, 2022 — New offering goes above and beyond industry requirement...
 Press Release
Press ReleaseCritical Start Ranks Fifth on the Dallas Business Journal’s Middle Market 50 List for 2022
PLANO, Texas, Oct. 26, 2022 — Critical Start, a leading provider of Managed Detection and R...
 Datasheet
DatasheetManaged Detection and Response Services for Palo Alto Networks Cortex XSIAM for Endpoint
Our MDR service integrates with Cortex XSIAM for Endpoint to deliver team expansion with Cortex cert...
 Press Release
Press ReleaseCritical Start Delivers Threat Detection and Response Actions in Tandem with Palo Alto Networks Cortex XSIAM
Plano, TX, October 17, 2022 – Critical Start MDR service offering available for Cortex XSIAM c...
 News
NewsMeet the 2022 Dallas 100, the fastest-growing private companies in North Texas
October 6, 2022 Critical Start was recognized as one of the fast-growing private companies in North ...
 Press Release
Press ReleaseCritical Start Announces Enhanced Threat Detection and Response Capabilities to Support Microsoft Defender for Servers
PLANO, Texas, Oct. 5, 2022 — New service offering is the company’s first threat detecti...
 Webinar
Webinar[On-Demand Webinar] Domain Expert Series Episode 1: Be a Data Security OpportuNIST
In this webinar, join our Director of Cyber Incident Response Team (CIRT) and Blue Team Services alo...
 News
NewsBeware of Phish: American Airlines, Revolut Data Breaches Expose Customer Info
September 20, 2022 Critical Start’s CTO, Randy Watkins, spoke with Dark Reading on the recent ...
 Press Release
Press ReleaseCritical Start Continues Accelerated Growth with Executive Leadership Appointments and Promotions
Plano, TX, September 13, 2022 – Company hires new Chief Revenue Officer, Chief Information Sec...
 Press Release
Press ReleaseCritical Start Named to 2022 CRN® Fast Growth 150 List for Second Year in a Row
Plano, TX, Aug. 30, 2022 – Critical Start Recognized as a Leading IT Solution Provider for Exc...
 Press Release
Press ReleaseCritical Start Named to 2022 Inc. 5000 List of Fastest-Growing Private Companies in America for the Second Time
Plano, TX, Aug. 17, 2022 – The company’s tremendous growth comes as organizations strive to ...
 Webinar
WebinarTurning Threat Intelligence into Custom Detections to Stop Attacks
Learn on how we turn threat intelligence from our threat hunting team into custom detections added t...
 Video
VideoManaged Detection and Response with Trace3 and Critical Start
Critical Start and Trace3 discuss the importance of Managed Detection and Response (MDR) when it com...
 Datasheet
DatasheetManaged Detection and Response & Cyber Incident Response Team (CIRT): An Unbeatable Combination
Managed Detection and Response (MDR) and Cyber Incident Response Team (CIRT) services are two comple...
 Video
VideoRandy Watkins, CTO interview with David Raviv at RSA
Our CTO Randy Watkins sat down with David Raviv from NY Information Security Group at RSA Confe...
 Solutions Brief
Solutions BriefA Financial Services Guide to Cybersecurity
For financial institutions, being compliant should be the result of a strong cybersecurity program &...
 Quick Card
Quick CardCybersecurity Readiness Assessment
Enhance your cyber resilience and evaluate all aspects of your cyber defense operations....
 Quick Card
Quick CardTabletop Exercises
Test your organization’s ability to respond to attacks and build resiliency through moderated scen...
Quick Card
MDR for Splunk Cloud
Our Managed Detection and Response (MDR) Services for Splunk® Cloud simplifies breach prevention an...
 Press Release
Press ReleaseCritical Start Named Winner of the Global InfoSec Awards At RSA Conference 2022
Plano, TX (June 6, 2022) – Critical Start Wins “Hot Company MDR Service Provider” and “P...
 Press Release
Press ReleaseCritical Start Announces Expansion and Enhancement of EDR Coverage with New MDR Service Offering for Trend Micro Vision One
Plano, Texas – June 6, 2022 – The expansion demonstrates Critical Start’s continued co...
 Webinar
WebinarGetting the most out of your Microsoft Security investment with MDR
Hear from Critical Start and Redmond on how managed detection and response services combine with you...
 Press Release
Press ReleaseCritical Start Named in Microsoft Design Collaboration for New Microsoft Security Experts Services
PLANO, Texas, May 12, 2022 — The collaboration has allowed Critical Start to leverage its ex...
 Press Release
Press ReleaseMultiple Critical Start Female Channel Executives Named to CRN’s 2022 Women of the Channel List and Recognized as a Power 70 Solution Provider
PLANO, Texas, May 10, 2022 — Critical Start, a leading provider of Managed Detection and Res...
 Press Release
Press ReleaseCritical Start Secures Over $215 Million Strategic Growth Investment from Vista Equity Partners to Expand Cybersecurity Protection for the Modern Enterprise
PLANO, Texas – April 12, 2022 – Investment enables Managed Detection and Response leader Cri...
 eBook
eBookSPARK Matrix: Managed Detection and Response (MDR) 2021
Critical Start was recognized as an MDR leader in the SPARK Matrix from Quadrant Knowledge Solutions...
Podcast
In the News – Don’t Get Stung
In this week’s episode, Randy covers the Hive Ransomware Group, the reemergence of Scarab APT,...
 Webinar
Webinar[On-Demand Webinar] Bank on Cybersecurity: Protecting Financial Services from Harm
The financial services industry is literally “where the money is”, making it a leading target fo...
 Press Release
Press ReleaseCritical Start Releases Enhanced Capabilities for Microsoft 365 Defender to Detect and Respond to Phishing and Other User Account Attacks
Plano, Texas – March 29, 2022 – These latest enhancements allow customers to leverage Mi...
Podcast
Threat Actors Two Ways
In this episode, Randy Watkins covers the biggest stories on our news feeds today: the Oscars and th...
 Quick Card
Quick CardIncident Response Plan Review
This quick card describes our Cyber Incident Response Team’s IR Plan Review service and the be...
 Customer Stories
Customer StoriesTrusting the Critical Start Team | A Financial Services Firm’s Use Case
“The biggest lesson is transitioning from alert overload to being at a point where we do have ...
 Press Release
Press ReleaseCritical Start Announces Several New Hires and Promotions at the Vice President Level as the Company Accelerates Growth
PLANO, Texas, Feb. 24, 2022 — The MDR services provider has added two new roles and promoted ...
 Webinar
Webinar[On-Demand Webinar] A Cure for Killware: Healthcare’s Newest Cybersecurity Challenge
Killware! That sounds pretty bad. But what does it mean, how does it happen, & how do you preven...
 Webinar
Webinar[On-Demand Webinar] Protecting Against Multi-Vector Cyber Attacks with MDR and Microsoft 365 Defender
Learn how to provide total protection with Microsoft 365 Defender & MDR services. Hear from Micr...
Podcast
Sponsored IDC White Paper with Craig Robinson
Join CRITICALSTART CTO and SON OF A BREACH! podcast host Randy Watkins as he talks with IDC Pro...
 Datasheet
DatasheetChoosing a Managed Detection and Response Partner
Do your security analysts spend too much time manually triaging alerts? Do you often work with third...
 Solutions Brief
Solutions BriefBuyer’s Guide for Cortex XDR
XDR takes endpoint detection and response to the next level, delivering comprehensive visibility int...
 Webinar
WebinarIntroducing the Cyber Research Unit: The new way to increase SOC effectiveness and stay ahead of emerging threats
The only thing that’s constant is change. As a defender, you’re consistently inundated with new ...
 Quick Card
Quick CardCritical Start Managed Detection and Response VS Cyber Incident Response Team
Critical Start Managed Detection and Response (MDR) and Cybersecurity Incident Response Team (CIRT) ...
 White Paper
White PaperIn Cybersecurity Every Alert Matters – an IDC White Paper
A cybersecurity practitioner has one of the hardest jobs to tackle today.
Constant vigilance is req...
Press Release
Critical Start Announces Enhanced Managed Detection and Response Services Offering for Microsoft Security Suite
Plano, TX – October 19, 2021 — The comprehensive integration with the Microsoft security...
CRITICALSTART Named “Overall Threat Detection Solution Provider of the Year” in 2021 CyberSecurity Breakthrough Awards Program
Prestigious International Awards Program Recognizes Outstanding Information Security Products and Co...
Podcast
Palo Alto Networks’ Tim Junio Shares How Acquisition Strategy and a New Perspective on Data are Making a Definitive Impact in Cybersecurity
Building on the success of a next-generation firewall business, Palo Alto Networks is now leading ac...
Podcast
SentinelOne’s Yonni Shelmerdine Explains why the key to Success in XDR lies in its Evolution, not Revolution
With the acquisition of Scalyr, SentinelOne® is carving out a unique position in the security space...
Podcast
#BadgeLife with Jonathan Singer, SIEM and SOAR Practice Lead, GuidePoint Security
Conference badges have evolved from paper and plastic to collectable mini-computers of all shapes an...
Datasheet
Critical Start Cybersecurity Consulting for Microsoft Security Solutions
This catalog details the Cybersecurity Consulting for Microsoft Security solutions offered by Critic...
Inc. Magazine Reveals Annual List of America’s Fastest-Growing Private Companies—the Inc. 5000
CRITICALSTART Ranks No. 3108 on the 2021 Inc. 5000, With Three-Year Revenue Growth of 122 Percent NE...
Podcast
Rated XDR: Microsoft’s Ann Johnson Sees Security Tools Moving into a Cohesive Orbit, with Humans still Holding the Center of Gravity
While Microsoft took a hit to its security reputation with Windows Defender 2016, the Big 5 Technolo...
CRITICALSTART® Places 73rd on the 2021 CRN® Fast Growth 150 List
CRN® Recognizes the Top IT Channel Providers for Exceptional Performance and Growth PLANO, Texas,&n...
EY Announces ROB DAVIS of CRITICALSTART as an Entrepreneur Of The Year® 2021 Southwest Award Winner
For Immediate Release Plano, TX (August 5, 2021) – Ernst & Young LLP (EY US) today announced t...
 Webinar
WebinarMaking The Grade: Using MDR To Protect Schools From Cybersecurity Threats
From big universities to small school districts, educational institutions are facing increases in ra...
Podcast
Rated XDR: Where CrowdStrike’s Ajit Sancheti thinks Extended Detection and Response is Headed, what it means for SIEM and how it can Improve the Current State of Security
CrowdStrike is on a roll. With the recent acquisitions of Humio and Preempt Security, they’ve adde...
Podcast
What’s Going On With Our SON OF A BREACH! Podcast?
We admit it. We haven’t quite gotten the cadence down on our SON OF A BREACH! podcast series. Yes,...
Press Release
EY Announces Rob Davis of Critical Start as an Entrepreneur Of The Year® 2021 Southwest Award Finalist
DALLAS, TX, June 8, 2021 – Celebrating the 35th class of unstoppable entrepreneurs who transform t...
Podcast
Risk Expert Doug Jones on SON OF A BREACH! Podcast: Ransomware Drives Biggest Losses in Insurance
Ransomware attacks and cybercriminal gangs continue to make headlines as they create the highest sev...
 Customer Stories
Customer StoriesManufacturer Stops Breach Cold, Thanks to Critical Start Incident Response Services
“We were very fortunate that our backups were not compromised. But you can restore all day long, a...
 News
NewsManaged Security Services Provider (MSSP) News: June 3, 2021
June 3, 2021 Each business day, MSSP Alert broadcasts a quick lineup of news, analysis and chatter f...
 Customer Stories
Customer StoriesProtecting the Business with Critical Start MDR & Microsoft
Real-World Results: MDR in Action The Security Director for this global leadership advisory and sear...
Press Release
Critical Start Announces New Chief Security Officer Role and New VP, Sales Operations to Manage Rapid Company Growth
Plano, TX (May 25, 2021) — Critical Start, a leading provider of Managed Detection and Response (M...
Press Release
Critical Start Featured on CRN’s 2021 Solution Provider 500 List
Plano, TX (June 1, 2021) — Critical Start, a leading provider of Managed Detection and Response (M...
Customer Stories
Maximize efficiencies with CRITICALSTART MDR
“Saves My Team Time And Alert Fatigue, Allowing Us To Concentrate On More Important ThingsR...
Podcast
SON OF A BREACH! Podcast: Episode 6 – Ransomware: Dive Into Cyber Insurance Coverage
Ransomware attacks and cybercriminal gangs continue to make headlines as they create ...
 News
NewsEthical Disclosures are Being Ignored: An Unchecked Security Crisis
May 31, 2021 | Forty-seven percent of cyber security professionals are investigating only 10-20 thre...
Podcast
SON OF A BREACH! Podcast: CFO Andrew Kaufman Calculates Cost of Risk
The science and art of security come down to two things: quantifying and managing risk. Do...
Press Release
Top Female Executives of Critical Start Featured on CRN’s 2021 Women of the Channel List and Recognized as a Power 60 Solution Provider
Plano, TX (May 11, 2021) — Critical Start, a leading provider of Managed Detection and Response (M...
 Datasheet
DatasheetCritical Start Security Services for Microsoft Sentinel
MDR reinvented. SIEM reinvented. An integrated threat detection and response solution for the modern...
Podcast
Didi Dayton Joins SON OF A BREACH! Podcast to Celebrate Women in Cybersecurity
Episode 4 of our SON OF A BREACH! podcast series celebrates International Women’s Month with secur...
Press Release
Critical Start Recognized as a Microsoft Security 20/20 Partner Awards Finalist for Top MDR (Managed Detection and Response) Team
PLANO, Texas, March 17, 2021 — Critical Start today announced it has been named a finalist for...
Podcast
SON OF A BREACH! Episode 4: Celebrating Women in Cybersecurity with Didi Dayton
While women’s numbers in cybersecurity lag behind men, female leaders in our industry continue t...
Press Release
With a Two-Year Revenue Growth of 79 Percent, Critical Start Ranks No. 157 on Inc. Magazine’s List of the Fastest-Growing Private Companies in Texas
PLANO, Texas, March 16, 2021 — Inc. magazine today revealed that Critical Start is No. 157 on ...
Press Release
Critical Start releases third-annual Security Operations Center (SOC) professional survey
PLANO, Texas, March 9, 2021– New data reveals alert-overload still plagues cybersecurity indu...
 White Paper
White PaperThird-Annual CRITICALSTART Research Report reveals persistent challenges and some silver linings
It’s back! For the third year in a row, we have surveyed SOC professionals from across the industr...
Press Release
Critical Start aims to eliminate “acceptable risk” from cybersecurity’s vocabulary
PLANO, Texas, March 1, 2021 – Critical Start, a leading and trusted provider of Managed Detec...
Podcast
Rock your SOCs: SON OF A BREACH! Podcast
Do you know how to find the right talent and skillsets to build up your Security Operations Center? ...
Press Release
SMU Cox Dallas 100™ Names Critical Start One of the Fastest Growing Privately Held Companies in Dallas Area
PLANO, TX, (February, 25 2020) – Critical Start, a leading cybersecurity provider of Managed Det...
Podcast
No Kidding: SON OF A BREACH! Podcast Welcomes Dr. Anton Chuvakin for Detection Insights
What do a $10 billion funding request for cybersecurity, a massive collection of 3.2 billion passwor...
Press Release
CRN Names Critical Start To Its 2021 MSP 500 List
PLANO, Texas, Feb. 18, 2021 — Critical Start, a leading cybersecurity provider of Managed Dete...
Press Release
Dwayne Myers of Critical Start Recognized as 2021 CRN® Channel Chief
PLANO, Texas, Feb. 9, 2021 — Critical Start, a leading cybersecurity provider of Managed Dete...
 Quick Card
Quick CardCyber Incident Response Team (CIRT) Services
This solution quick card discusses the robust incident readiness, incident response and forensic ser...
 Podcast
PodcastThe Impact of Talent and Resource Shortages in Cybersecurity
It’s no secret – there is a severe talent and resource shortage in cybersecurity, but what is th...
 Podcast
PodcastGovernment’s Role in Cybersecurity
What role does the government play in cybersecurity? Is it a private sector or government responsibi...
 Podcast
PodcastFighting the Unknown: Next-Generation Cyberattacks and Vulnerabilities
In next-gen cyberattacks and vulnerabilities, you’re fighting the unknown. Building a catalog of t...
 Podcast
PodcastCybercrime: The Monetization of Security Threats
How do you stop the burgeoning field of cybercrime? From ransomware to malware as a service, the mon...
 Podcast
PodcastCyber Warfare: How Wars May Be Fought in the Future
How will wars be fought in the future? Are we keeping up with the times in cyber warfare as a nation...
 Video
VideoCritical Start’s MOBILESOC® App
Video Transcript: Security breaches happen at the worst time, and any delay in response increas...
 Podcast
PodcastCRITICALSTART & ePlus | National Cybersecurity Awareness Month Podcast
Full Transcript: LW: Welcome. Thanks for joining everyone, my name is Lee Waskevich, vice presi...
 Video
VideoCISOs: Communicating Risk to Board Members
Cybersecurity doesn’t have to be a roadblock to effectiveness. CRITICALSTART’s SVP of Managed Se...
 Customer Stories
Customer StoriesProfessional Services: Devising a Strategy that Secures and Saves Money
One of the largest utility companies in the southern US was looking for expertise to help them archi...
 Customer Stories
Customer Stories100% Transparency: Blowing the Lid Off the “Black Box”
When one of the world’s leading beverage companies began their search for a Managed Security Servi...
 Quick Card
Quick CardThreat Hunting Training
Organizations often don’t realize they’ve been breached, giving malicious actors the freedom to ...
Press Release
Critical Start Honored in CEO Innovation Awards 2021
PLANO, Texas, Jan. 29, 2021 — Critical Start, a leading cybersecurity provider of Managed Dete...
 Webinar
WebinarThreat Briefing: What to Know and Do About the SolarWinds Attack
The SolarWinds cybersecurity breach known as Sunburst has organizations ranging from government agen...
 Press Release
Press ReleaseCritical Start Named to Inc. Magazine’s Vet100 List
PLANO, Texas, Dec. 15, 2020 — Critical Start a leading cybersecurity provider of Managed Detect...
 News
NewsAlleged Russian SolarWinds Hack ‘Probably an 11’ on Scale of 1 to 10
Featured on Newsweek A cybersecurity expert warned that the alleged Russian hack of SolarWinds softw...
 News
NewsFireEye Breach to Have Big Impact on Cybersecurity Industry
Featured on Channel Futures | December 9, 2020 This week’s FireEye breach is distressing for ...
 News
NewsTips for Keeping Your Personal Information Safe When Shopping Online
Featured on Fox 2 KTVU | December 4th, 2020 Tens of millions of Americans participated in cyber...
 News
NewsScammers Target Consumers on Record Day of Online Shopping
Featured on Fox News 13 Tampa | December 1, 2020 This holiday season is set to shatter online s...
 Press Release
Press ReleaseCritical Start Awarded the Palo Alto Networks America’s Cortex Partner of the Year Award for 2020
PLANO, Texas, Dec. 3, 2020 — Critical Start a leading cybersecurity provider of Managed Detec...
 News
NewsHere’s How You Can Protect Yourself From Scams This Black Friday
Retail stores should be taking heightened security measures during the holiday season to protect the...
 News
NewsRansomware Attack on Plano Tech Firm Highlights Key Issue Companies Need to Understand
By Brian WomackDallas Business Journal | November 15, 2020 Plano’s Tyler Technologies was hit by a...
 Press Release
Press ReleaseCritical Start Named to the 16th Annual Aggie 100, Honored as Fastest Growing Company
PLANO, Texas, Nov. 12, 2020 — Critical Start, a leading cybersecurity provider of Managed De...
 News
News“Adaptability” With Douglas Brown & Tera Davis
An interview with Douglas Brown of Thrive Global and Authority Magazine. As a pa...
 News
NewsUnknown Election Outcome Benefits Cybercriminals
Without a clear winner, there is a big opportunity for disinformation campaigns. Cybercriminals are ...
 Podcast
PodcastPodcast: The Last Watchdog Interview with Randy Watkins
“Security is really the art of handling risk” – Randy Watkins, CTO of CRITICALSTART. It’s cl...
 Press Release
Press ReleaseCritical Start Recognized as 14th Fastest-Growing Tech Company in North Texas by Tech Titans
PLANO, Texas, Nov. 3, 2020 — Critical Start, a leading provider of Managed Detection and Respon...
 News
NewsThe 4 Threats Facing Voters This Election — and How You Can Beat Them
By Faith Karimi, CNN – October 20, 2020 As the US grapples with an election ...
 Press Release
Press ReleaseCritical Start CEO Rob Davis selected as EY Entrepreneur of the Year 2020 Finalist
PLANO, Texas, Oct. 14, 2020 – Congratulations to Critical Start CEO, Rob Davis, who has been...
 Press Release
Press ReleaseCritical Start Named to MSSP Alert’s Top 250 MSSPs List for 2020
PLANO, Texas, Sept. 29, 2020 – Fourth-Annual List Honors Leading MSSP, MDR and SOCaaS Cyberse...
 News
NewsArkansas’ Colleges and Universities Bolster Security Posture by Partnering with CRITICALSTART
FAYETTEVILLE, Ark., Sept. 22, 2020 /PRNewswire/ — CRITICALSTART, a leading cybersecurity...
 News
NewsA Hospital Ransomware Attack May Have Caused a Death in Germany
State authorities in North Rhine-Westphalia are investigating whether a hospital ransomware attack r...
 News
NewsCRITICALSTART Names New CMO, Continues 2020 Growth
PLANO, Texas, Sept. 10, 2020 /PRNewswire/ — On Thursday, Dallas-based cybersec...
 News
NewsMiami-Dade Public Schools Virtual Learning Disrupted by Teen
A 16-year-old student was able to disrupt the Miami-Dade Public Schools e-learning system earlier th...
 News
NewsCritical Vulnerabilities Expose MoFi Routers to Remote Attacks
Routers made by MoFi Network are affected by several vulnerabilities, including critical flaws that ...
 News
NewsWhat to Know About Possible Cyberattacks as Students Return to School
Ransomware attacks are usually more common early in the school year. Cybersecurity experts are conce...
 News
NewsRouter Vendor Has Patched Some Zero-Days, but Leaves Others Wide Open
Written by Sean Lyngaas of CyberScoop In April, security researcher Rich Mirch got a text ...
 News
NewsDDOS Attack Takes New Zealand Stock Exchange Market Off-Line
The New Zealand Stock Exchange (NZX) has been under attack for several days now as a DDOS ...
 News
NewsCybersecurity Threats Grow as Virtual Learning Continues
NASHVILLE, TENN. (WSMV) – As schools are back in session, so are hackers and cyber-criminals looki...
 News
NewsTech Expert: Ways to Protect Your Student From Hackers During Online Learning
How you can protect your computer and how school districts are protecting your information. With so ...
 News
NewsHackers Increasingly Targeting Online Learning
Most schools and universities are back in session virtually. While online learning is the best...
 News
NewsIT Pros Warn of Potential Cyberattack Dangers
RALEIGH, N.C. (WNCN) — School is in session, but instead of heading into the classroom many kids a...
 News
NewsExperts Warn At-Home Learning Could Attract Hackers
So many students are starting classes this week and cyber experts warn that your child’s e-classro...
 News
NewsCRITICALSTART Named a 2020 Inc. 5000 Fastest-Growing Private Company in America
PLANO, TX – August 12, 2020 – CRITICALSTART, a leading provider of Managed Detection a...
 News
NewsCRITICALSTART® Ranks 58th on the 2020 CRN® Fast Growth 150 List
PLANO, Texas, Aug. 4, 2020 /PRNewswire/ — CRITICALSTART, a leading provider of ...
 News
NewsCan Your Car Be Hacked?
With the recent household device hacks in the news, CRITICALSTART’s VP of Professional Services, S...
 News
NewsExperts Warn Lack of Discussion Impeding Cybersecurity Preparedness
Despite the recent hacking of high-profile users’ Twitter accounts, and reports&nbs...
 News
NewsChina Vows Retaliation After U.S. Ordered Its Houston Consulate Closed Within 72 Hours
China vowed to retaliate Wednesday after the United States abruptly ordered the closure of its consu...
 News
NewsWho’s Going to Derail the U.S. Presidential Election? The Culprit May Be Close to Home
WASHINGTON – Fearing nightmare scenarios such as attacks on voter registration databases...
 News
NewsCRITICALSTART joins Microsoft Intelligent Security Association
PLANO, Texas, July 16, 2020 /PRNewswire/ — CRITICALSTART, a leading provider of&nbs...
 News
NewsWhy Security Alert Fatigue Matters and How to Address It
An influx of false positive security alerts can lead infosec pros to overlook real threats. Learn ho...
 News
NewsTaxes Are Due, But Beware of Scams Targeting Last-Minute Filers
LOS ANGELES (CBSLA) — The federal income tax deadline is Wednesday, after being postponed fro...
 News
NewsHackers Target Contact Tracing Applications
NBC News and Boston 25’s Blair Miller interviews Quentin Rhoads-Herrera of CRITICALSTART‘s TEAMA...
 News
NewsThe Need for State Data in Contact Tracing Apps
Leslie Toldo of NBC 25 Mid-Michigan Now News interviews CRITICALSTART‘s CTO, Randy Watkins, on the...
 News
NewsHow the COVID-19 Pandemic Affects Hackers
Cybersecurity expert Rob Davis, CEO of Critical Start, talks to Hal of Fox 11 New in Los Angeles ab...
 News
NewsCOVID-19 Contact Tracing Apps and Your Privacy
As COVID-19 cases rise, some people and government agencies are turning to contact tracing apps to h...
 Podcast
PodcastSecurity and the Human Element: The Need for the Organizational CISO
In cybersecurity, humans will always have a role to play. Security incidents need critical decision-...
 News
NewsCritical Start Recognized as Best Place to Work by the Channel Partner Insight MSP Innovation Awards 2020
PLANO, Texas, June 25, 2020 /PRNewswire/ — CRITICALSTART, a leading provider of&nbs...
 News
NewsCRITICALSTART Named to CRN’s 2020 Solution Provider 500 List
PLANO, Texas, June 2, 2020 /PRNewswire/ — CRITICALSTART, a leading provider of Mana...
 News
NewsAccuracy in AppSec Is Critical to Reducing False Positives
According to a new report from the Neustar International Security Council (NISC), over one...
 Press Release
Press ReleaseCritical Start’s Tera Davis Honored as a Power 40 Solution Provider Among CRN’s 2020 Women of the Channel
Plano, TX, May 19, 2020 — Critical Start, a leading provider of Managed Detection and Response ...
 Podcast
PodcastSecuring Data: The Importance of Understanding Your Most Valuable Assets
With multiple data points that exist in organizations, how do you know what you need to protect? Wha...
News
How Apps Could Change the Workplace After Coronavirus Crisis
Several apps could hold the future to a safe office after reopening. Imagine you are going in to wor...
 News
NewsHow Safe and Private Are Contact Tracing Apps?
Quentin Rhoads-Herrera, director of professional services at CRITICALSTART, joins GDC to talk about ...
 News
NewsAre Contact Tracing Apps Putting Your Private Data At Risk?
That’s what a lot of you have asked us. So, the Q&A team reached out to Quentin Rhoads-Herrera...
 News
NewsTennessee Has Just 25 Percent of Recommended Contact Tracers
Tennessee has just 25 percent of the recommended amount of contact tracers, leaving the state 1,500 ...
 News
NewsTransparency Key to Heading Off Qualms About Contact Tracing, Experts Say
In late April, Gov. Andrew Cuomo announced the state’s partnership with Bloomberg Philanthropies f...
 News
NewsPolitico: An Unusual Hacking Threat
The education system might be overlooking an unexpected threat with the whole world moving online:&n...
 News
News16 Strategies For Attracting Top Tech Talent To Your Company
In a highly competitive economy, it’s often difficult to attract and retain top talent. This is es...
 News
NewsAssessing Your Cyber Risk Impact: Intent vs. Opportunity
Cybersecurity is no longer just a concern for large corporations and government entities. One of the...
 News
News16 Smart Project-Management Strategies Every Tech Leader Can Use
Task and project management is a must-have skill in the technology industry, especially for tech lea...
 News
NewsCybersecurity During a Pandemic: An Interview With CRITICALSTART
Chris Ward speaks with Quentin Rhoads-Herrera of CRITICALSTART to discuss cybersecurity in a ti...
 News
NewsNFL Draft Via Social Media Offers Insights Into Online Security
For the first time in National Football League history, draft day is going remote and online. Social...
 News
NewsVirtual Draft Makes NFL Teams Potential Targets for Hackers
A hacker could provide entertainment value by disrupting the virtual NFL draft that begins Thursday....
 News
NewsExperts Warn of Tax Scams With Delayed Deadline
The tax deadline came and went and now is the time when scammers see confusion and opportunity. “I...
 News
NewsSecurity Versus Convenience
Zoom has become nearly synonymous with office meetings and socializing as people around the world ha...
 News
News5 Things IT Teams Can Learn From Initial Weeks of Telecommuting
In the wake of the ongoing coronavirus pandemic, we have witnessed a surge in telecommuting as ...
 News
NewsA researcher found zero-days in one city’s software. Then he realized the problem could be bigger.
For Quentin Rhoads-Herrera, this was not a typical security test. A big municipal government in the ...
 News
NewsAI’s Great, but It Still Takes Humans to Enforce Cybersecurity
When it comes to protecting computers and information systems from cyber attack, artificial intellig...
 News
NewsConsumer EducationData PrivacyInterview
Interview: 2020 Election Security and the Future of Online Voting
Jordan Mauriello, SVP of Managed Security, shares his thoughts with Steve Gruber of the Steve Gruber...
 News
NewsUsing Password Crackers to Analyze the Virus
In addition to helping doctors provide care, technologists are helping researchers find a vaccine fo...
 News
NewsThe Cost to Defend: Automation is Key in Combatting Cybercrime
As organizations find themselves short on budget and talent, security automation that supplements th...
 News
NewsSuper Tuesday: Election Cybersecurity Survey
A recent survey by computer security firm CRITICALSTART showed 66 percent of Super Tu...
 News
NewsQ&A: How Firms Can Stop Wasting Time Pursuing ‘Cyber Ghosts’
In an increasingly connected and digital world, no company or industry is safe from the growing thre...
 News
NewsInterview: Online Scammers Are Taking Advantage of Typos to Steal Your Personal Information
How many times have you typed in the wrong URL? If you’re like us, it happens a lot — bu...
 News
NewsFirst in MC: Super Tuesday Hack Safety Confidence Low
Two-thirds of voting-age adults in Super Tuesday states believe the election is vulnerable to foreig...
 News
NewsNew Survey: 66% of Super Tuesday Voters Fear Elections Aren’t Secure
New Survey: 66% of Super Tuesday Voters Fear Elections Aren’t Secure With less than one week to go...
 Press Release
Press ReleaseCritical Start Grows Business By More Than 100%, Expands Headquarters
PLANO, Texas, Feb. 25, 2020 – New channel model, minority investment among key milestones �...
 Press Release
Press ReleaseCritical Start Named to CRN’s Managed Service Provider (MSP) 500 list for 2020
PLANO, Texas, Feb. 25, 2020 – Critical Start has been named to CRN’s MSP 500 list for 202...
 News
NewsData Breaches and Their Main Causes
A data breach is an incident in which a victim’s sensitive information is acce...
 News
NewsHOT TOPIC: 2020 Election Cybersecurity
CRITICALSTART CEO, Rob Davis, discusses the security of digital versus paper voting in the 2020...
 News
NewsInterview: 2020 Election Security and Digital Voting
FRANK FM – New Hampshire interview with Rob Davis, CEO of CRITICALSTART Aired February 17, 202...
 News
NewsRansomware Is Back: Tips for Avoiding the Growing Context-Based Ransomware
Cryptojacking is so 2019. Ransomware is reemerging as the top cybercrime of choice, with attacks exp...
 Press Release
Press ReleaseCritical Start Adds Support for Microsoft Azure Sentinel
PLANO, Texas, Feb. 12, 2020 – Addition of new cloud-native SIEM to MDR platform helps enter...
 News
NewsAI Stats News: 35% Of Workers Worldwide Expect Their Job Will Be Automated
The Life of Data, the fuel for AI: Security Recent surveys, studies, forecasts and other quantitativ...
 News
NewsThreat Overload: IT Feels the Security Burnout
How can enterprises and IT professionals combat the increasing IT security threats without feeling b...
 News
NewsIran Conflict Could Shift to Cyberspace, Experts Warn
Hackers linked to Iran are probing American companies for vulnerabilities, cybersecurity researchers...
 News
NewsAvoiding Risk Acceptance With Security Alerts
As the shortage of security professionals grows, most organizations struggle to attract and retain t...
 News
NewsFalse Positives Plague Cybersecurity Professionals
Automation is helpful in reducing the time to investigate alerts. Cybersecurity providers are being ...
 News
NewsCyberattacks Are an ‘Immediate’ Challenge for Businesses Following Iran Strike
Cyberattacks, already seen as the top risk of doing business by executives, are likely to ...
 News
News12 Essential Questions to Ask CTO Candidates
Technology is ever-changing, and it’s important for every business to keep up with new gadgets and...
 Press Release
Press ReleaseCritical Start Announces New Partnership with Fast-Growing Endpoint Protection Security Leader SentinelOne
PLANO, TX – January 14, 2020 – Partnership provides endpoint remediation capabilities to help cu...
 News
NewsTips for Building Camaraderie in a Remote Tech Team
With an exclusively remote tech team, there may be fewer opportunities for team building. However, w...
 News
NewsGetting the Most out of Endpoint Security Solution Evaluations
The endpoint security market has evolved over the last decade from a “one agent to rule them a...
 Press Release
Press ReleaseCritical Start Releases Major Redesign of MobileSOC
PLANO, TX – December 4, 2019 – Industry’s first – and only – MobileSOC app helps driv...
 News
NewsCritical Start’s Randy Watkins Joins Forbes Technology Council
Critical Start CTO, Randy Watkins, was recently tapped for membership in the Forbes Technology Cou...
 Press Release
Press ReleaseCritical Start Named a 2020 Best Tech Startup in Plano by The Tech Tribune
PLANO, Texas, Nov. 26, 2019 – The news just keeps getting better for Critical Start! The Tec...
 Press Release
Press ReleaseCritical Start Named to SMU’s Dallas 100 List for Third Consecutive Year
Plano, TX – November 22, 2019 – List Recognizes Fastest-Growing Privately Held Businesses in...
 Press Release
Press ReleasePlano’s Critical Start Plans to Continue Growth After Recent Successes
PLANO, TX – Nov. 13, 2019 – Cybersecurity software company Critical Start was created in r...
 News
NewsData Breaches: Safeguarding Your Healthcare Organization
Breaches are increasing – a proactive approach to data protection can help you safeguard your orga...
 Press Release
Press ReleaseCritical Start Recognized by Dallas Business Journal as Best Workplace
PLANO, TX – Oct. 31, 2019 – We’ve always known Critical Start is a great place to work, a...
 Press Release
Press ReleaseCritical Start Names Chief Financial Officer
PLANO, TX – October 16, 2019 – Innovative MDR company expands executive team and names Andre...
 Press Release
Press ReleaseCritical Start Named to 2019 MSSP Alert Top 200 Managed Security Services Providers List
PLANO, TX – October 11, 2019 – Third Annual List Honors Leading MSSPs, MDR Service Providers...
 Press Release
Press ReleaseCritical Start Unveils Channel Strategy Driving High-Growth MDR Services
PLANO, Texas, Oct. 9, 2019 – Agreements with leading cybersecurity distributors and resellers...
 News
NewsThe Last Watchdog Talks to CRITICALSTART About Quantifying Risk
“Security is really the art of handling risk” – Randy Watkins, CTO of CRITICALSTART. It’s cl...
 Press Release
Press ReleaseCritical Start Kicks Off Cybersecurity Awareness Month
PLANO, TX – October 1, 2019 – Coinciding with National Cybersecurity Awareness Month 2019, w...
 News
NewsProtecting Your Agency Against Ransomware Attacks
Ransomware attacks are not going away. Security researchers have repeatedly warned the public sector...
 News
NewsThe Importance of Password Managers and MFA in Your Security Stack
The subject of password strength and complexity requirements has been discussed and debated ad ...
 News
NewsWhat’s the Real Role of AI and ML in Cybersecurity?
Artificial intelligence (AI) and machine learning (ML) are being heralded as a way to solve a wide r...
 Press Release
Press ReleaseNew Research from Critical Start Finds 8/10 Security Analysts Report Annual SOC Turnover Is Reaching 10% to More Than 50%
PLANO, TX – August 29, 2019 – Data shows the number of alerts is up, longer times to investi...
 Press Release
Press ReleaseCritical Start Signs U.S. Distribution Agreement with SYNNEX Corporation
PLANO, TX – August 15, 2019 – New distribution agreement expands reach and availability of t...
 News
NewsManaged Services and Risk: Mitigation or Inherent Acceptance?
With the evolution of cybersecurity over the last decade, it’s easy to forget what security is; th...
 News
NewsNetwork Security: Keys to Adopting Zero-Trust, Micro-Segmentation
Adoption of zero-trust and micro-segmentation as core design principles can help improve the securit...
 Press Release
Press ReleaseCritical Start Names Vice President of Channels Alliances
PLANO, TX – August 19, 2019 – Hyper-growth MDR company adds cybersecurity industry expert Dw...
 News
NewsRadical Transparency and Zero Trust: Putting Concept into Practice
Enterprise CIOs, CSOs, and VPs of security need business outcomes and a positive ROI from their MSSP...
 Press Release
Press ReleaseDecoding Critical Start’s Rapidly Expanding MSSP Business
PLANO, Texas, July 8, 2019 – Critical Start and Microsoft recently announced a collaboration ...
 Press Release
Press ReleaseCritical Start Signs U.S. Distribution Agreement With Ingram Micro
PLANO, TX – July 10, 2019 – New distribution alliance expands reach and availability of Mana...
 News
NewsWhat a Plano Cybersecurity Firm’s $40M Capital Raise Tells Us About the Region’s Ecosystem
A Plano cybersecurity firm will open offices in Los Angeles and New York in a national expansion fue...
 News
NewsManaged Detection and Response: Critical Start Raises $40M
Critical Start, a Top 100 MSSP with managed detection and response (MDR) cyberse...
 News
NewsData Breach Threats in the Real World: How MSSPs Can Help Mitigate Them
The U.S. Customs and Border Protection said this week that travelers’ images and persona...
 News
NewsPlano Cybersecurity Company Gets $40M in First Outside Investment, Has Valuation of $150M
Critical Start is looking beyond itself to fuel fresh growth. The Plano cybersecurity company raise...
 Press Release
Press ReleaseCritical Start Raises $40 Million in Minority Investment to Fuel Growth of Its Zero-Trust Platform and Managed Detection and Response Services
PLANO, TX – June 12, 2019 – Funds will be used to accelerate North American expansion and ca...
 News
NewsEquifax Breach, Two Years Later: Lessons for the Financial Services Industry
Nearly two years after the Equifax breach, the fallout is far from over. As detailed in the 96-page ...
 News
NewsAI and Machine Learning Make Data the New Source Code
The role of data in today’s business world cannot be overstated. Competitive intelligence is inext...
 News
NewsNext-Gen Firewalls: Key Considerations to Make the Most of Your Investment
You’ve purchased a next-generation firewall. You understand the why, but how do you...
 News
NewsProtect Your Enterprise Against Social Media Hoaxes
In an era of fake news and constant misinformation, Facebook/Instagram/WhatsApp hoaxes have become a...
 Press Release
Press ReleaseCritical Start Announces Collaboration With Microsoft
PLANO, TX – April 30, 2019 – Combined Technologies Will Reduce Alerts by 99% and Deliver a F...
 Press Release
Press ReleaseCritical Start Recognized for Excellence in Managed IT Services
Plano, TX – March 13, 2019 – MDR Provider Named to CRN® MSP 500 List and Managed Security ...
 Press Release
Press ReleaseCritical Start Announces Partnership with Chronicle to Bring Advanced Security Solutions to Market
RSA CONFERENCE, SAN FRANCISCO, March 4, 2019 – MDR services powered by industry’s only Zero-...
 News
NewsCRITICALSTART Announces Managed Detection and Response Services with Palo Alto Networks Traps Management Service
Industry’s only Zero-Trust Analytics Platform with full transparency and MOBILESOC app now in...
 Webinar
Webinar3 Challenges Facing Cybersecurity Professionals Revealed
Join CRITICALSTART‘s industry-leading cybersecurity professionals Randy Watkins, Chief Technology ...
 News
NewsCritical Start Takes “Radical Transparency” for MDR Customers to New Level with SOCREVIEW
Automated and audited process integrated into the MDR provider’s Zero-Trust Analytics Platform ens...
 News
NewsAnnouncing Beta MDR Program for Windows
CRITICALSTART is the fastest growing MDR service in North America, and we are expanding our ser...
 News
NewsCritical Start Recognized by Palo Alto Networks as a NextWave Diamond Partner
Plano, TX – December 4, 2018 – CRITICALSTART, today announced it has become a Palo Alt...
 News
NewsCRITICALSTART Named to Aggie 100 List by the Texas A&M Mays Business School
List Recognizes the Fastest-Growing Aggie-Owned Businesses in 2018 Plano, TX – November 13, 2018 �...
 News
NewsCRITICALSTART Names Chief Technology Officer
Randy Watkins to Lead Strategic Technology Initiatives for Fast-Growing Leader in MDR Services, Cybe...
 News
NewsCRITICALSTART Named CRN® Triple Crown Award Winner
Fifth Annual Award Program Recognizes Standout Solution Providers Plano, TX – October 10, 2018 –...
 News
NewsCRITICALSTART Achieves Soc 2 Type II Compliance Certification
Certification Validates CRITICALSTART’s Adherence to Higher Industry Security Standards for a Serv...
 News
NewsCRITICALSTART Named to Top 100 Managed Security Services Providers of 2018 by MSSP Alert
Second Annual List Honors Leading MSSPs & Cybersecurity Companies That Safeguard Customers’ Di...
 News
NewsNew Tech: CRITICALSTART Applies ‘Zero-Trust’ Security Model to Managed Security Services
All companies today are exposed to intense cyber-attacks. And yet the vast majority simply do not ha...
 News
NewsCisco Warns Customers of Critical Security Flaws, Advisory Includes Apache Struts
Cisco has issued a security advisory to customers detailing a swathe of critical and highly-rat...
 News
NewsHigh-Severity Flaws in Cisco Secure Internet Gateway Service Patched
Two high-severity vulnerabilities have been disclosed in Cisco’s security platform that ...
 News
NewsCisco Releases 16 Security Alerts Rated Critical and High
Cisco published on Wednesday 30 security advisories on vulnerabilities identified in ...
 News
NewsCisco Warns of Critical Remotely Exploitable Vulnerabilities
Cisco has issued security alerts for 30 vulnerabilities across a range of its product...
 News
NewsCisco Patches Serious Flaws in RV, SD-WAN, Umbrella Products
Cisco informed customers on Wednesday that patches are available for over a dozen critical and ...
 Press Release
Press ReleaseCritical Start Increases Revenue 87%, Moves into New Headquarters to Support Future Growth
PLANO, Texas, Aug. 29, 2018 – Cybersecurity company completed a strategic acquisition to bolst...
Press Release
Critical Start Named to 2018 CRN Fast Growth 150 List
PLANO, Texas, Aug. 6, 2018 – Cybersecurity solution provider named for the second consecutive...
 News
NewsEmerging Vendors 2018: Cybersecurity Companies You Need to Know
In the IT industry, shattering the status quo is the status quo. While big vendors generate their sh...
 News
NewsHow Legacy MSSPs Increase Cybersecurity Risks
Today, the number of cyberattacks is on the rise. According to a 2017 report from Accenture, th...
 Press Release
Press ReleaseCritical Start Announces New Advanced Threat Analytics App for the Palo Alto Networks Application Framework
ANAHEIM, Calif., May 22, 2018 – Critical Start today unveiled its Advanced Threat Analytics app...
 Press Release
Press ReleaseCritical Start to Acquire Advanced Threat Analytics
DALLAS, March 15, 2018 – Unique Managed Security Services Provider (MSSP) / Managed Detect &a...