Unlock the Full Power of Microsoft Security with MDR
Transform Your Cybersecurity from Chaos to Clarity
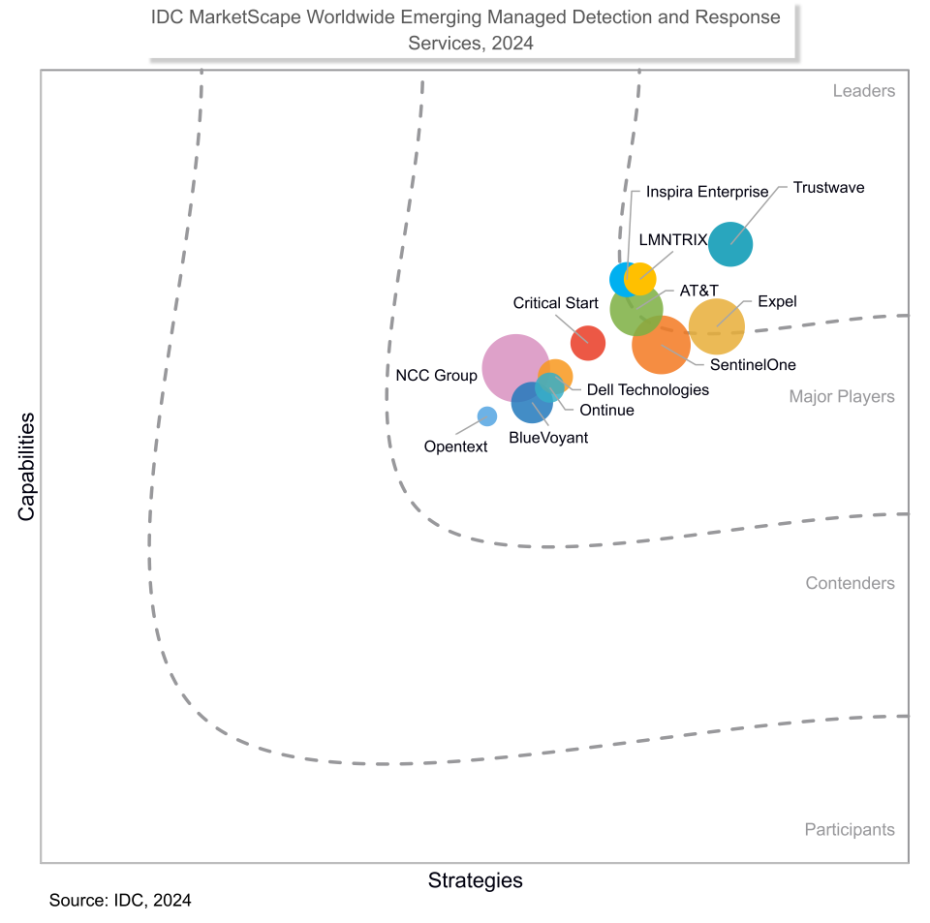
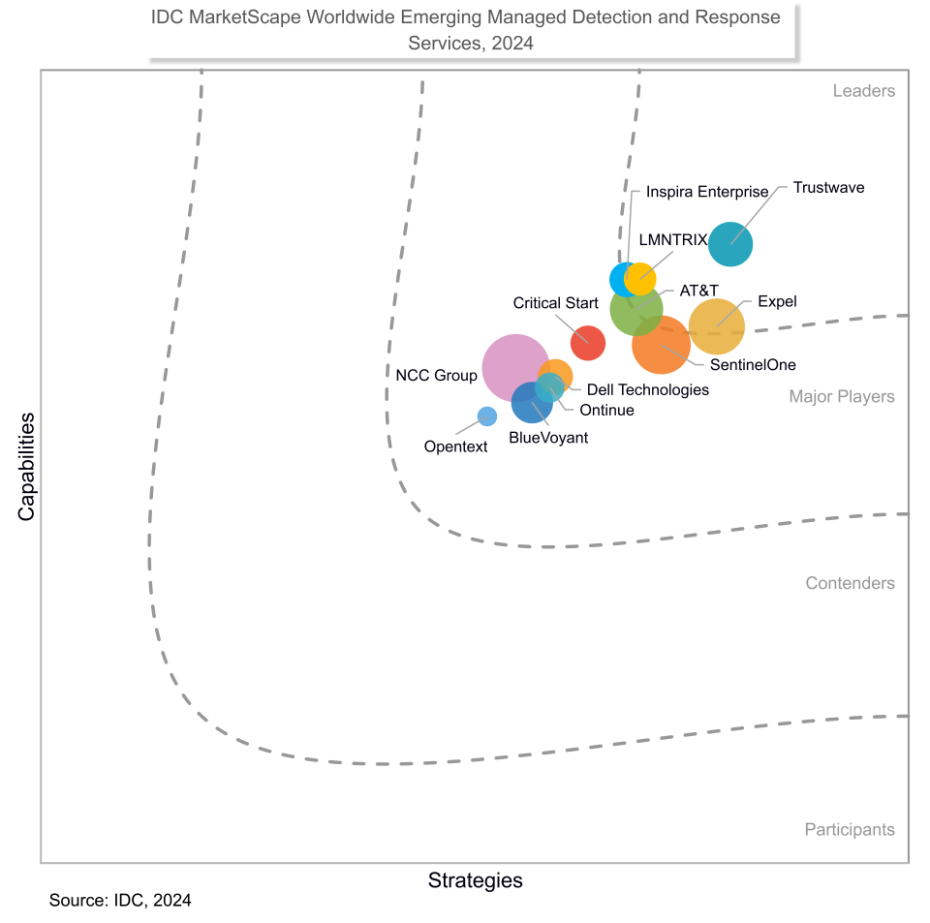
In today’s relentless threat landscape, your team is drowning in alerts, juggling tools, and racing against evolving attacks. Microsoft Security gives you the toolkit — Defender, Sentinel, Entra — but tools alone won’t win the fight. Pair them with Managed Detection and Response (MDR) from Critical Start to stop reacting and start dominating threats.
Why You Need This White Paper:
Alert Overload: Cut through the noise and focus on real threats.
Skill Gaps: Get 24x7x365 expert response when your team can’t.
Tool Sprawl: Unify your security for seamless protection.
Always-On Defense: Sleep easy with round-the-clock monitoring.
Compliance Simplified: Meet regs without breaking a sweat.
Don’t Wait for the Next Breach — Download Now and Take Control!