Outer Space Meets Cyberspace: What Space Travel Can Teach Us About Cybersecurity
February 20, 1962: An Atlas LV-3B launch vehicle lifts off from Launch Complex 14 at Cape Canaveral, Florida. It’s lifting astronaut John Glenn into orbit aboard the Mercury program spacecraft known as Friendship 7.
At the time, this was a technological marvel and a wonder of engineering complexity. But it was this complexity that Glenn had to try and manage during his three orbits around the earth.
The Evolution of Astronauts and IT Security Providers
Limited information. Manual processes. Extremely detailed checklists. It all may sound familiar to those working in digital security. The complicated environment of space travel can offer insight into the world of information security, and managed security services in particular.
Both have evolved extensively over the years to transform volumes of data into insight and actionable information – information that can be delivered just in time to the hands that need it most.
Spacecraft and SIEM Platforms: Security Through Monitoring Tools

This image shows us just what John Glenn was facing as he sat on the pad at Cape Canaveral: Primary events controls, flight control displays, environmental controls and displays, cabin pressure controls, voltage displays and controls, communications controls, and even control systems controls.
But as complicated as all this was, it did serve a primary function: to serve as a starting point that would ultimately get us to the moon.
From a security perspective, there is a similar scope to early versions of log aggregation and Security Incident and Event Management (SIEM) platforms. It’s where the journey really begins for cybersecurity monitoring.
Before Automation, Threats Were Buried in a Sea of Alerts
In the Friendship 7 capsule, there was basic instrumentation with little automation. The astronaut had to review long and detailed checklists, flipping a multitude of switch combinations to really make use of the information coming from the instrumentation.
In the early days of log aggregation, there were multiple tools to contend with, providing conceivably hundreds of different alerts that had to be processed and understood to uncover a potential threat. Runbooks didn’t exist and every Security Operations Center (SOC) had their own methodology for investigating alerts.
When a crisis occurred during the Apollo 13 mission, it took over 80 hours to diagnose the problem, mitigate the impact, and get the crew safely home. In the early days of cybersecurity monitoring, the time to detect a breach was 206 days.
Simplified User Interfaces Improve Information Processing Capabilities

During the space shuttle era, we witnessed the development of the Multifunction Electronic Display System (MEDS).
Typically known as a “glass cockpit,” the new cockpit display system improved the crew-orbiter interaction with easy-to-read graphics of key flight indicators, such as attitude, altitude, and speed.
It simplified the information astronauts needed to know during liftoff and to navigate and land the vehicle.
Each shuttle orbiter could be configured differently for every mission, according to what the astronauts wanted to be contained on each display.
Prioritizing Alerts with Automation
With the space shuttle, situational awareness was increased over the Mercury and Apollo capsules, enabling the astronauts to focus more on the mission at hand.
Similarly, it can be said that Managed Security Service Providers’ (MSSP) correlation rules and visual analytics were able to make some sense automatically out of multiple data sources. This is really a pivotal point where the technology evolved.
But a customer working with an MSSP received information and had to go through playbooks and checklists using their own security team to make sense of what they were receiving. Response capabilities from the MSSP were limited and network-based.
It was better, but there was still more work to be done: as recently as 2019, the suggested amount of time to detect an intrusion was 100 days.
Filtering Massive Amounts of Data

Fast forward to the current day. The SpaceX Dragon capsule recently carried human passengers for the first time, and all of the information they needed to make critical flight decisions was compressed down from thousands of components to three flat-screen displays and basically 2 rows of switches (and many of those are only meant to be used as a last resort).
Multiple layers of data that astronauts would need to process and interpret to make corrections to a flight path are now handled by AI, so they can focus on monitoring the overall performance of the spacecraft.
Managed Detection and Response: Cybersecurity Evolved
Now think about Managed Detection and Response (MDR), which is the latest evolution of security monitoring and response.
An MDR service provider will help make the minor adjustments that can mitigate a larger security issue. Based on the data coming in, they’re investigating issues and helping to take action on a client’s behalf. This can provide clarity for that client to focus on more strategic decisions.
The MDR Monitoring and Response Process
Here’s what such a process looks like:
- All security-relevant alerts, regardless of priority, are sent to an investigation platform.
- The investigation platform resolves all known good behavior and escalates unknown or malicious alerts to the SOC for review.
- An MDR SOC analyst creates an alert consisting of the following: a) what was observed; b) risk associated with the finding; and c) recommended next steps. Additional details may include information about the IoC(s) discovered in addition to IP and behavioral information collected by the security tools.
- The MDR SOC analyst may take response action on the client’s behalf, such as host isolation.
- The alert is escalated to the client through a web-based UI or mobile application, so they have a clear view of what’s happening.
- The client can then review logs of the machine targeted, pivot into various tool consoles looking for additional indicators of compromise (IoCs).
- The alert investigation platform can also be used to review raw alert data from EPP/EDR tools and other security data feeds.
And yet, for all the steps that just happened, the client can use a simple, intuitive user interface to gain all the necessary data needed to make actionable decisions.
Introducing CRITICALSTART’s Improved MDR User Interface
Take a look at the new UI from CRITICALSTART to see just how essential security monitoring information can be provided in the modern age:
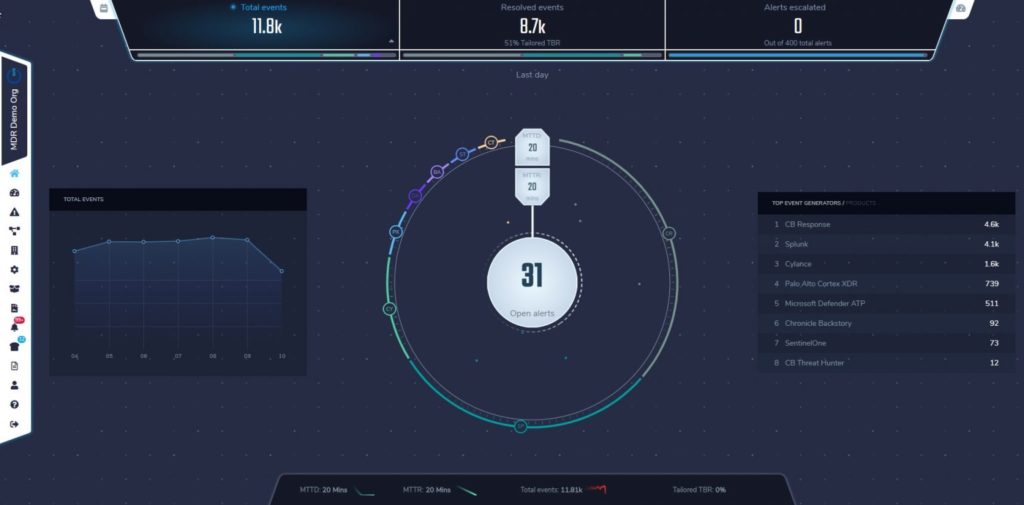
We’ve found that the dwell time to detect a breach working through our approach is 22 minutes on average. And with our UI, our clients are able to focus on threats with transparency and clarity—and without distraction.
Both space exploration and cyber threat monitoring have come a long way in a relatively short amount of time, increasing visibility and greatly enhancing the ability for decision-makers to react in a high-pressure situation.
We’re looking forward to what the future holds next. In the meantime, contact CRITICALSTART today to learn how our advanced MDR platform can eliminate alert fatigue and free your security team to focus on the alerts that truly matter.
By Jim Rohde | Director of Pre-Sales Engineering, CRITICALSTART
June 19, 2020

VP of Pre-Sales Engineering
As the VP of Pre-Sales Engineering, Jim is responsible for leading a team of security experts supporting technical conversations for Critical Start’s products and services. Previously, Jim held leadership roles at large Managed Security Service providers including Secureworks & Trustwave where he received numerous awards for exceeding customer and company objectives. Jim’s expertise in a multitude of security domains over his career has made him a sought after trusted advisor for organizations of all sizes.
You may also be interested in…
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)