MXDR Verified – Raising the Bar on XDR

Collaboration drives innovation and improves outcomes
Critical Start has a longstanding collaborative relationship with Microsoft dating back to the early days of the Microsoft Security suite. We were initial members of the Microsoft Security Partner Advisory Council, and are a current Design Build partner, a MISA member, a Microsoft security solutions partner, and an inaugural member of the MXDR Partner program. Today, we announced achieving Microsoft MXDR verified status, another milestone in our commitment to collaborate with industry leaders to drive innovation, raise the standards for Managed Detection and Response providers, and drive reliable outcomes for the businesses that rely on these services.

Raising the bar
Achieving verified status is not just another checkbox certification in cybersecurity, it marks a significant milestone in an industry that is flush with acronyms, confusion, and hyperbole; EDR, NDR, MDR, etc. Managed Extended Detection and Response or MXDR is no exception and is just the latest example. From an industry perspective, Microsoft’s MXDR verified program begins to set a baseline for what makes up an MXDR solution, and what the customer of these services should expect. It combines the capabilities of the SIEM and XDR, delivering threat protection across endpoints, email, user credentials, cloud apps, and more. In addition to data and tool integration, and automation, Microsoft MXDR verified also requires robust deployment and operational capabilities on the part of Managed Detection and Response (MDR) services providers. In other words, saying you are MXDR is one thing, being verified is another.
The Microsoft MXDR verified program is putting an industry stake in the ground and requires MDR providers to put their money where their marketing is, proving they can deliver, including Critical Start. In addition, the verified program supplies criteria for customers to evaluate all MDR providers against. Even if you’re not a Microsoft security shop, using the MXDR verified status as an evaluation criterion is an effective bar to hold MDR providers too. If you are a Microsoft security shop, it is a great framework and roadmap to effective cybersecurity.
What does it mean to be Microsoft MXDR Verified?
Unfortunately, much of what is in the inaugural MXDR verified criteria are capabilities that many think MDR providers already deliver. However, the MXDR verified program is an industry first. It brings together Microsoft SIEM and XDR capabilities in an operational model that includes the following criteria:
- 24x7x365 SOC monitoring across Microsoft Sentinel and 365 Defender – even though this should be table stakes, not all MDR providers are 24x7x365
- Advanced hunting as part of new incident investigation – this goes beyond detection ticket forwarding and really shows an MDR provider’s cybersecurity chops. Can they get to the root causes of infiltration and exploitation or is this going to happen again?
- Leverage Microsoft Defender’s built-in response capabilities for manual/automated response (ex: isolate machine) – This is another advanced operational criterion. Saying you have response capabilities is one thing but to be able to effectively respond without causing more damage is another. In addition to tight integration, this requires the MDR provider to have a deep level of situational awareness of the threat and systems affected before response actions are taken, especially if they’re automated.
- Develop and deliver custom detection rules and queries, and Indicators of Compromise (IOCs) – Being able to develop and deliver custom detection rules and IOCs is the lifeblood of MDR effectiveness. For Critical Start, it’s how we can be the only MDR provider that focuses on analyzing all detections versus a subset of high and medium criticality detections.
- Managed Detection and Response Microsoft integrations – The foundation and base criteria for the MXDR Verified program is to integrate and deliver MXDR services for Microsoft Sentinel, 365 Defender and Defender for Cloud. That is a tall order and solid criteria to evaluate an MDR provider. How robust are their integration capabilities? Are they able to cover the breadth of technologies that make up an XDR solution? And, to what level are they able to integrate, operationalize, and execute on this data?
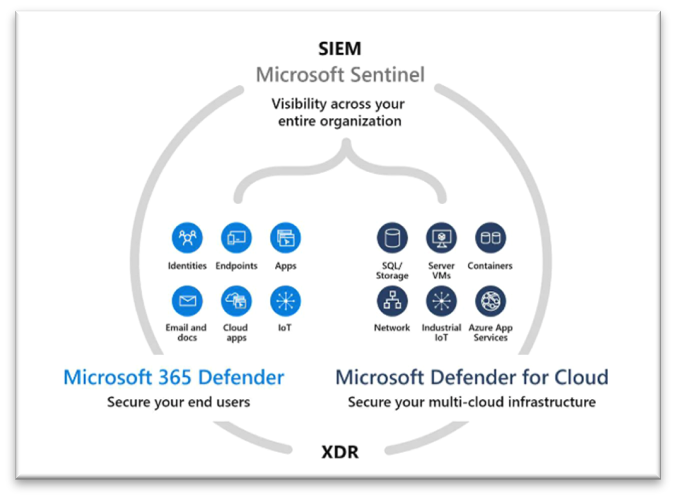
- Managed SIEM for Microsoft Sentinel services – Another table stakes criteria but an important one to many customers of MXDR services, is managing the SIEM that makes up the data layer of an MXDR solution. MXDR providers should be able to handle these complex and tedious tasks as well.
- Microsoft Expertise – A deep bench of Microsoft expertise is a requirement and good evaluation criteria as well.
- Guaranteed 1-hour Service Level Agreement (SLA) for Time to Detect (TTD) and Median Time to Respond (MTTR) – Okay, this isn’t part of the MXDR Verified criteria, but we think it is a great one to add your evaluation list.
What’s next?
While I can’t go into details on the next iteration of MXDR Verified criteria, one thing is for sure, you can bet Critical Start will be collaborating to drive greater operational standards. Some areas we are delivering today and will be advocating for inclusion into future MXDR verified criterion emphasize improved operational outcomes. Here are a few key areas:
- Raising the bar on delivering actionable views of attacks in progress with clear, step-by-step response guidance, so security teams can gain situational awareness they can use.
- Measuring the mean time to response (MTTR) for analysts and teams to drive continuous improvement, productivity, and team efficiency.
- Mapping detection content to the MITRE ATT&CK framework to enable risk-based decision making and improved attack coverage effectiveness.
- Articulating the value of an MXDR service is challenging at best, MXDR providers should be able to deliver the data and reporting to make this yet another table stakes criteria.

CTO
As the Chief Technology Officer and an emerging thought-leader in the security industry, Randy is responsible for designing and executing the company’s strategic technology initiatives, which includes defining the strategy and direction of CRITICALSTART’s Managed Detection and Response (MDR) services delivered by the Zero-Trust Analytics Platform® (ZTAP). Previously, Randy served as the Director of Security Architecture, where he set the strategy for emerging vendor technologies, created the Defendable Network reference architecture, and set product direction for the company’s internally-developed Security Orchestration Automation and Response platform.
You may also be interested in…
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)