IDC Survey Points to Value of MDR in Helping Companies Resolve Security Alerts
Companies of all sizes are failing to investigate an alarming number of security alerts – as many as one-third – and are spending about as long investigating false positives as they do actionable alerts.
Those are just two of the findings of a recent IDC survey looking at challenges organizations face due to the heightened quantity and quality of cybersecurity threats. The survey results paint a picture of organizations drowning in alerts and battling high turnover in their security operations centers (SOCs). That is, except for one key cohort: companies that use a managed detection and response (MDR) service are far more likely to address alerts from investigation through response.
Alert investigation is lacking
IDC surveyed more than 300 U.S.-based IT executives at companies with 500 or more employees. It found companies with 500-1,499 employees ignore or don’t investigate 27% of all alerts. The figure is nearly one-third (30%) for companies with 1,500-4,999 employees and 23% for those with 5,000 or more employees.
The idea that even the largest companies routinely ignore more than one-in-five alerts should be unacceptable in an era where threats such as ransomware are running rampant. But perhaps it’s because it takes companies so long to investigate alerts. The largest companies take 30 minutes to fully investigate an actionable alert and a bit longer (32 minutes) to investigate a false positive alert, IDC found. Smaller companies spend somewhat less time (see Figure 1) but still, given companies can easily get thousands of alerts per day, it’s in inordinate amount of time.
Figure 1
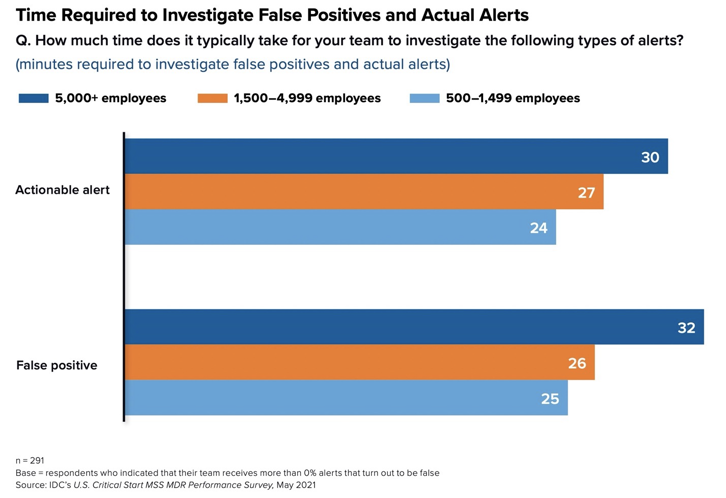
MDR customers investigate far more alerts
However, the IDC survey found companies that use an MDR service fare far better.
“MDR providers are more likely to take the entire detection, containment, and response function all the way through to completion,” writes Craig Robinson, Program Director, Security Services for IDC, in a white paper based in part on the survey findings (see Figure 2). “Given its 24 x 7 x 365 monitoring and response capabilities, the MDR provider is often in the best position to take certain response actions, and such responsibility should be authorized accordingly.”
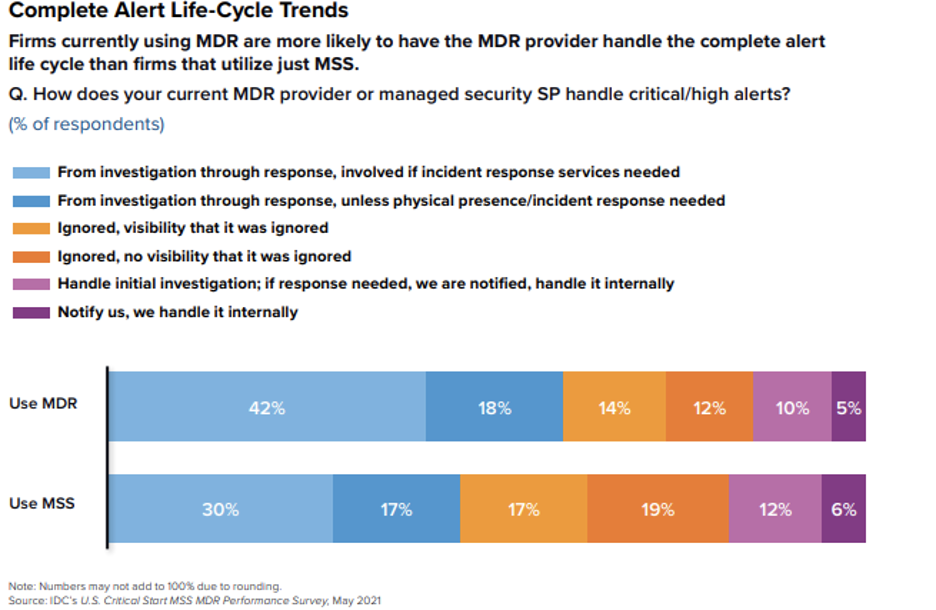
Robinson points out that, as part of the customer onboarding process, an MDR provider will discuss with the customer what sorts of threats the company faces and the responses it deems appropriate for the MDR provider to take. Many customers take advantage of their MDR’s incident response (IR) service to remediate serious threats.
“Incident response demonstrates that an organization’s security posture is migrating from a reactive to a proactive stance,” Robinson writes. Companies such as Critical Start also offer IR retainers that provide clients resources on standby for use at a moment’s notice without needing to draft a new contract or onboard a new provider.
Use of IR retainers also enables CIOs or chief information security officers (CISOs) to have fruitful discussions with their board of directors over the steps the company is taking to mitigate risk. “Specifically, boards want to know that their investments will pay dividends in reducing
the costs of potential ransomware incidents and address concerns about lost productivity,” he writes. “Going through exercises, assessments, and simulations as part of utilizing an incident response retainer are proactive activities in that they help organizations prepare for future incidents.”
Security costs boards care about
Indeed, in terms of costs that boards are most concerned about, the IDC survey found they are twice as likely to be concerned about lost productivity from security incidents (58%) and cyber insurance (56%) as they are about spending on security consulting (24%), internal staffing (22%), and training (17%). Fewer than one-third of boards (32%) are concerned about spending on MDR and MSS offerings – a finding that shows CIOs and CISOs may well have room to push for more funding for MDR services.
That’s especially true since using an MDR provider alleviates stress on your internal SOC and security team, which will help reduce turnover – another issue Robinson says boards will be happy to hear about.
Of course, not all MDR companies are the same. You’d be hard-pressed to find one other than Critical Start that reviews every alert – with a service level agreement (SLA) to back it up. We’ve also got the IR services to help customers proactively prepare for real-world breaches.
Check out the IDC white paper to learn more about what a quality MDR service entails. And feel free to contact us with any questions or sign up for a free demo.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
