How to be a Data Security OpportuNIST: Announcing Episode 1 of the Critical Start Domain Expert Series
It’s time to break down the barriers between data and cybersecurity professionals. Episode 1 of the Domain Expert Series will show you how to unify these roles into one shared goal of protecting your data—the 21st century currency of business.
Our special guest speakers include Joe Reis and Matt Housley, co-founders of Ternary Data and co-authors of Fundamentals of Data Engineering. Joe and Matt will be joined by Ross Williams, our Director of CIRT and Blue Team Services, to cover topics such as:
- Data types that threat actors are targeting most often
- How they are successful in compromising your data
- The impacts from vulnerabilities and risks introduced by not having the appropriate security controls in place
The goal is to give you a deeper understanding of how to identify your most valuable digital assets and transform that knowledge into a reliable risk management strategy.
Exploring the NIST framework
Ross will also add context around the NIST framework that provides the foundation for the discussion. The Cybersecurity Framework | CSRC (nist.gov) is based on existing standards, guidelines and practices to help organizations better manage and reduce cybersecurity risk.
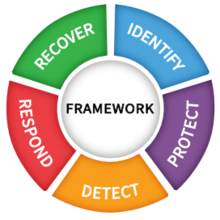
The NIST Framework is organized by five key Functions to provide a comprehensive view of the lifecycle for managing cybersecurity over time. These functions include:
Identify—Develop an organizational understanding to manage cybersecurity risk: systems, assets, data, and capabilities.
Protect—Develop and implement the appropriate safeguards to ensure delivery of services.
Detect—Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
Respond—Develop and implement the appropriate activities to take action regarding a detected cybersecurity event.
Recover—Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired during a cybersecurity event.
With each discussion, the Critical Start Domain Expert Series will bring together leaders in their field—including data engineering, system designers, legal experts, insurance panels and others—to cover in detail different levels of the framework.
Identify the data you need to protect
Episode 1 of our series will focus on level 1 of the NIST Cybersecurity Framework in working to identify that data that needs to be protected and the process to go about it. It will help you consider important questions such as:
- Where is my data?
- How is it stored?
- Who has access to it?
- Is my organization handling, processing, transmitting and/or storing it properly?
- Do I have a formal plan for protecting my data?
We’ll discuss the importance of investing the time and effort to perform tasks such as data cataloguing to benefit not only security, but data engineering and other teams as well. Our experts will share tips on identifying the priority assets that need the most protection to help formulate a solid incident response plan. Your IR team will need to check the right places in the event of a breach and focus on the most likely areas of attack. The right understanding of your data infrastructure, and the right plan to make it better will help you to target IR efforts for maximum effect.
We understand that for many data engineers, the demands of their daily job can pull their focus away from critical security issues. That’s why this discussion will also share insight on how a data engineering team can work most effectively with third-party security providers such as a DevSecOps team or IR team. You can learn how to work together towards a common goal and create a more healthy and secure technology environment, from a data perspective.
If you’re ready to connect with dedicated domain expertise in data engineering and cybersecurity, then sign up now for Episode 1 of the Critical Start Domain Expert Series.
And if you need to consult directly with IR experts on how best to protect the data infrastructure of your own organization, reach out directly to Critical Start to develop a cybersecurity plan tailored to your unique technology environment.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)