Efficient Incident Response: Extracting and Analyzing Veeam .vbk Files for Forensic Analysis
Introduction
Incident response requires a forensic analysis of available evidence from hosts and other devices.
Occasionally, or often if your organization uses Veeam, your source for host evidence will be a Veeam backup in the form of a .vbk file. The .vbk file is a proprietary “snapshot” containing all the expected components of a virtual machine snapshot for one or multiple machines.
Unfortunately, the .vbk file does not lend itself to forensic analysis and must be restored prior to processing. The restoration tools are the Veeam proprietary command line tool, Extract.exe, and the GUI application, Veeam.Backup.Extractor.exe, neither of which are available as separate downloads.
This post will detail how to get those tools, and how to extract the .vbk files.
Obtaining Extract.exe and Veeam.Backup.Extractor.exe
The command line Extract.exe, and the GUI application, Veeam.Backup.Extractor.exe, are only available from within the installed Veeam folder structure. Although these are proprietary programs, the only time you would need them is when the presence of Veeam backups dictates their use. Therefore, there is no licensing issue. Once you acquire the programs, keeping them for future use only in other environments that license the Veeam backup solution, and maintaining the programs will prevent future delays.
From the licensed Veeam Backup & Replication installation location, the programs are found in the %PROGRAMFILES%\Veeam\Backup and Replication\Backup\ folder containing three files for the extract utility, as well as an xml file as seen in the graphic below. Copy all four files to a folder within your examination environment.
The purpose for each of these programs is:
- Veeam.Backup.Extractor.exe — utility working in GUI (can be used on Microsoft Windows machines only)
- Extract.exe — utility working in the command-line interface, a version for Microsoft Windows
- extract — a Linux version utility working in the command-line interface
Restoring Backups with Veeam.Backup.Extractor.exe
The Veeam.Backup.Extractor.exe program is a GUI based restoration program for Veeam created .vbk backup files.
Below is a screenshot of the Veeam Backup Extraction Utility’s user interface. Both the path to the .vbk and to the output directory are entered via the browse buttons. As you see in the example below, this .vbk file only contains the backup for a single machine.
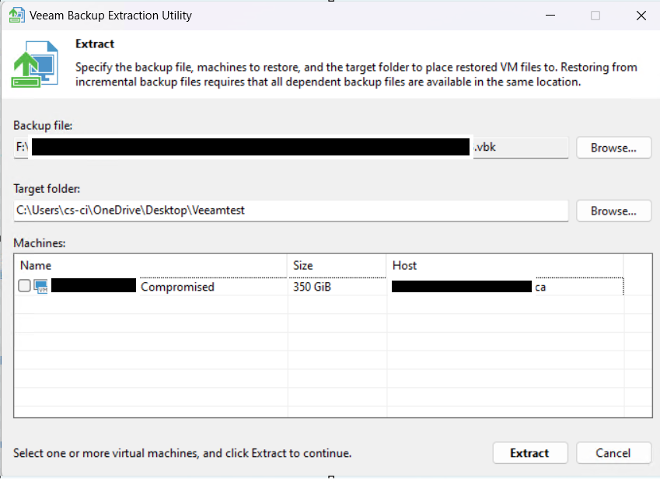
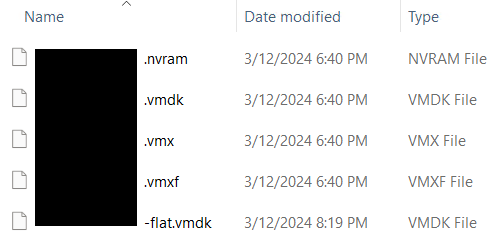
At this point, you simply check the box next to the machine(s) you wish to restore and press Extract. The contents of the .vbk will be restored to your Target folder for further processing as shown in the screenshot below.
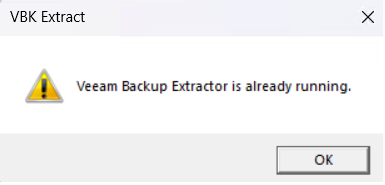
Note that you may only run a single instance of the GUI interface at a time. For multiple .vbk files, it would be more efficient to use the command line operation described below.
Restoring Backups with the Command Line programs
Depending on your operating system, the command line programs will be either extract for Linux, or Extract.exe for Windows. The command line operations will be similar for both. In cases of multiple .vbk files, you may run multiple terminals and extractions simultaneously.
First, open your preferred command line interface terminal. Navigate to the folder containing your restoration program as seen in the screenshots below. Note that in Windows, you may use either a command prompt terminal, or a PowerShell terminal. In this example, you see PowerShell:
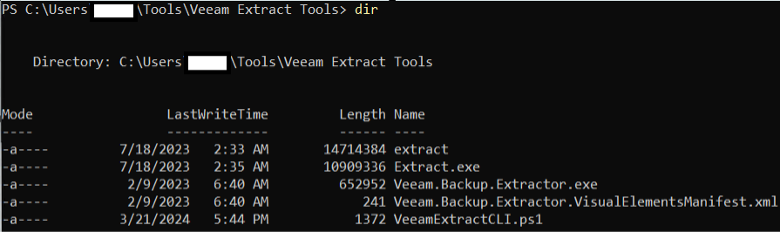
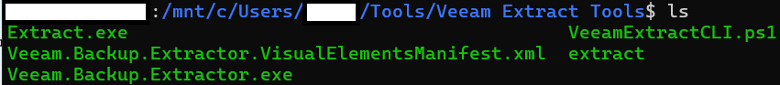
If using a Windows command prompt, entering the program name, Extract.exe, and hitting Enter will suffice. If in PowerShell, you must prepend the command as .\Extract.exe. In Linux, you must prepend the command as ./extract, since the program has not been added to the Path environment variable.
The screenshot below shows the process in a PowerShell terminal, but again, the process will be the same for a command terminal or a Linux terminal (with differences in the path appropriate for the Linux environment).
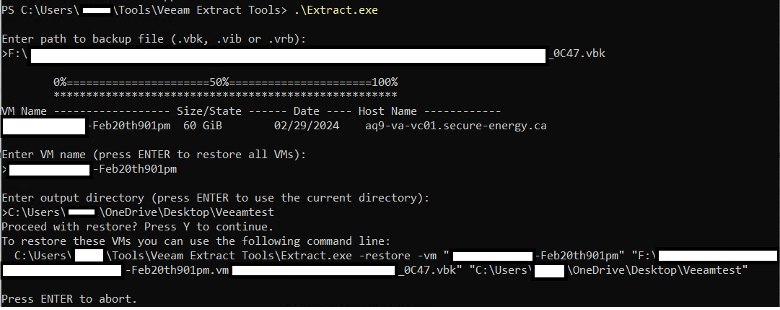
Once the program is executed, it will prompt you for the path to the .vbk backup file. This path must include the .vbk file name and extension.
Pressing Enter will list all of the virtual machine backups that the .vbk contains. If you want to restore a single virtual machine, enter the name at the prompt. Hitting Enter without entering a name will restore all of the machines to the Target/output folder.
Next, you will be prompted to enter the destination folder for the output restored VM’s.
Pressing enter again will initiate the backup restoration process. You may either let the restoration process run, or hitting Enter again will abort the process.
Conclusion
Although the Veeam backup .vbk files cannot be processed directly, the Veeam restoration programs offer an efficient solution. Acquiring the programs from the Veeam installation folder path either in-house or from a client is also straightforward.
Use of the GUI or command line programs is a decision of personal preference or of efficiency in cases involving multiple backups. The command line process can also be scripted, although that is beyond the scope of this discussion.
In conclusion, Veeam backup and restoration provides a dependable and robust data protection solution that you can leverage for incident response. Veeam also provides the tools to restore the proprietary backups to a condition suitable for analysis.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
