Exploring Rhysida Ransomware: A Deeper Understanding of the New Cyber Menace

Background
The digital landscape is in a constant state of flux, and with it, the ever-evolving realm of cyber threats. A recent addition to the cybercrime arena is the Rhysida Ransomware Group, which emerged in May 2023 and swiftly gained notoriety. Presenting themselves as a “cybersecurity team,” Rhysida has taken a unique approach, targeting systems, highlighting security vulnerabilities, and simultaneously threatening victims with the public release of stolen data. This blog post delves into the Rhysida Ransomware Group, elucidating their attack methods, tools, target sectors, and strategies for organizations to fortify their defenses against such threats.
Rhysida, a Ransomware-as-a-Service (RaaS) group, surfaced in late May 2023. Despite its newcomer status, the group has rapidly established itself as a formidable ransomware operation. Its debut attack targeted the Chilean Army, a high-profile incident that aligns with the trend of ransomware groups increasingly targeting Latin American government entities. On June 15, 2023, Rhysida leaked files stolen from the Chilean Army, substantiating its claims. Notably, the group frames itself as a “cybersecurity team” performing a service by exposing security vulnerabilities to their victims.
How It Works
Rhysida employs various methods for deployment, including the misuse of Cobalt Strike, a legitimate penetration testing tool often exploited by threat actors for its advanced exploitation and post-exploitation capabilities. Additionally, they employ phishing campaigns, indicating their potential to target a wide array of sectors and industries, as these methods lack specificity to any particular organization type. Rhysida delivers ransom notes in the form of PDF documents to affected folders on compromised drives, hinting at the types of systems or networks they target, capable of handling PDF documents but not command-line operating systems.
Notably, Rhysida adopts a double-extortion strategy, threatening victims with the public release of exfiltrated data, aligning them with contemporary multi-extortion groups. Their ransomware utilizes a 64-bit Portable Executable (PE) Windows cryptographic application, compiled using MINGW/GCC. As observed, Rhysida employs a 4096-bit RSA key with the ChaCha20 algorithm for encryption. The ransom note content is embedded in the binary in clear text.
Malware Analysis
The Cyber Research Unit (CRU) at Critical Start conducted an in-depth analysis on a recent sample of Rhysida ransomware malware. This comprehensive examination provided valuable insights not only into the ransomware itself but also into the individuals or group behind its operations. The threat actors were observed using Remote Desktop Protocol (RDP) and Windows Remote Management (WinRM) for movement across victim networks. To facilitate their movement, they took steps to collect credentials and other domain details by copying the NTDS.dit file with ntdsutil.exe. The Sysinternals PsExec was used to both distribute the ransomware across the network, but to also remotely execute it.
The attackers leaned on SystemBC and Cobalt Strike to maintain connectivity with their command and control infrastructure. When it came to data exfiltration, they seemed to favor the Invicta Stealer, a publicly available program coded in C++. In one instance mentioned in the HHS report, a sample triggered PowerShell to target an HTML Application (HTA) hosted on a Discord server. This action prompted the execution of mshta.exe on Windows, masquerading as the Invicta Stealer.
What set these attackers apart was their unusually sophisticated evasion techniques for a ransomware operation. These tactics included erasing traces of recently executed programs, directory file paths, scrubbing the PowerShell command history, and even purging RDP user history from the registry. Such meticulous cleanup efforts typically align more with espionage endeavors, making it an intriguing departure from the typical ransomware objective of data theft and encryption, along with the usual claim of responsibility.
Before unleashing the Rhysida ransomware, the attackers adhered to a series of preparatory steps in line with their objectives. This encompassed large-scale password changes, shadow copy deletions, and the alteration of the RDP port from the standard 3389. Other pre-attack measures involved disabling Windows Defender, establishing exceptions, and halting business application services to release file locks, rendering them susceptible to encryption by the ransomware. Ultimately, the deployment of Rhysida ransomware marked the culmination of their nefarious activities.
Targeting
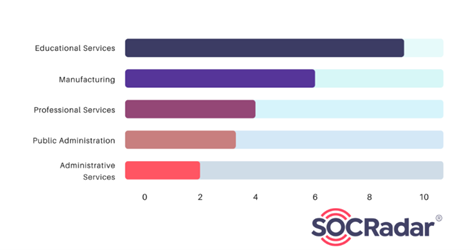
Concerning target sectors, Rhysida predominantly focuses on the Education and Manufacturing fields. Recent headlines featured the group’s announcement of hacking Prospect Medical Holdings and the theft of sensitive data. A subsequent cyberattack in early August disrupted computer systems at multiple hospitals operated by Prospect Medical Holdings across various states, forcing some emergency rooms to close. The group threatened to leak a stolen database, containing sensitive data, unless a 50 Bitcoin ransom (equivalent to $1.3 million) was paid. Additionally, Rhysida claimed to have breached three other US hospitals in late August, affecting multiple medical facilities operated by Singing River Health System.
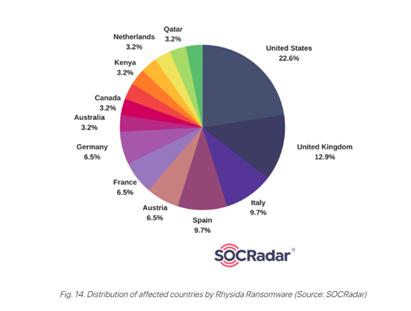
Targeted Countries
Regarding target countries, Rhysida primarily operates in North America, Europe, and Australia. Analysis of affected organizations’ locations reveals a focus on the United States, Italy, Spain, and the United Kingdom.
Collaboration with Other Cyber Actors
Recent security research suggests a potential association between Rhysida and Vice Society, as they share notable similarities in their Techniques, Tactics, and Tools (TTPs). It’s worth noting that Vice Society’s activity has recently ceased, and the group is presumed to have disbanded. This has raised suspicions that these two groups might have merged, possibly explaining the identical TTPs they employed. Furthermore, both cybercriminal entities have a history of targeting the education and healthcare sectors.
Conclusion
The Rhysida Ransomware Group has swiftly emerged as a substantial threat in the cybersecurity landscape. Leveraging robust encryption techniques and double extortion tactics, Rhysida poses a serious risk to organizations worldwide. Their demonstrated focus on military and government institutions, as seen in the Chilean Army attack, underscores the potential gravity of their operations. To counter these threats, organizations must comprehend Rhysida’s tactics, techniques, and procedures (TTPs) and proactively protect their systems and data. Recommendations include patching known vulnerabilities, implementing robust security measures, and conducting staff training to recognize and thwart phishing attempts. Additional safeguards involve virtual patching, phishing awareness training, endpoint security solutions, immutable backups, network segmentation, firewalls, intrusion detection systems, incident response planning, and applying the principle of least privilege to limit access rights.
__________________________________________________________________________
CRITICALSTART® offers a pioneering solution to modern organizational challenges in aligning cyber protection with risk appetite through its Cyber Operations Risk & Response™ platform, award-winning Managed Detection and Response (MDR) services, and a dedicated human-led risk and security team. By providing continuous monitoring, mitigation, maturity assessments, and comprehensive threat intelligence research, they enable businesses to proactively protect critical assets with measurable ROI. Critical Start’s comprehensive approach allows organizations to achieve the highest level of cyber risk reduction for every dollar invested, aligning with their desired levels of risk tolerance.
References
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
