What is EDR? And EDR vs. MDR vs. EPP – Security Compared
Proactive vs. Reactive Endpoint Security
Really, there are two kinds of security practitioners in the world right now:
- Proactive: Those who don’t like to ever spill the milk (aka those that want to make sure nothing malicious ever runs on an endpoint, or threat prevention); and
- Reactive: Those that know the milk will spill, so they’d better get ready to clean it up (aka detect when something malicious does execute and have a plan to remediate it).
Most Breaches Originate at Endpoints
The endpoint has become the most important asset to monitor, protect, and respond to in the event of a cybersecurity incident.
We are seeing an enormous rise in cyberattacks and breaches already with the massive increase in remote work and remote assets in the wake of the COVID-19 pandemic. As organizations deploy brand-new endpoints en masse to their employees to keep business moving, security may fall as an afterthought.
There are consequences to rapidly deploying workers, including their hardware. With a shortage of available business laptops for some organizations, now John and Jane may be using personal devices to connect to corporate networks, data, and applications in ways that are simply insecure.
So what’s the solution, you might ask as a line of defense? Endpoint protection, detection, and response.
EPP vs. EDR vs. MDR: What’s the Difference?
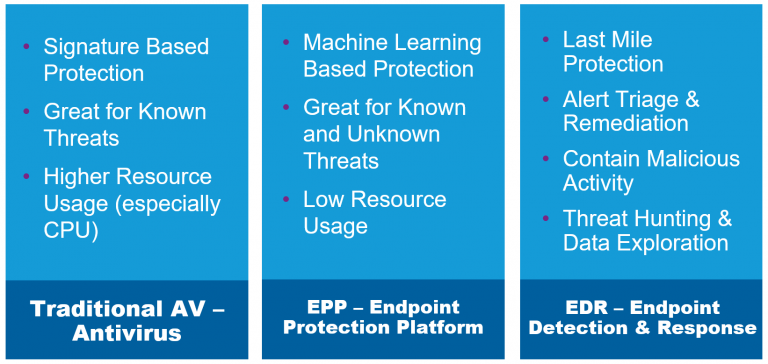
EPP, EDR, and MDR are three of the most common endpoint security solutions on the market today. These tools enable your workforce and empower your security teams to truly mitigate risk, reduce dwell time, and resolve every alert!
However, the context of these cybersecurity implementations matters a lot to the efficacy and efficiency of the best-of-breed tools today.
Let’s dive in and compare EPP vs EDR vs MDR.
Endpoint Protection Platform (EPP)
Endpoint Protection Platform (EPP) simply refers to next-generation antivirus (AV). I loathe the now-ubiquitous term of “next-gen” as much as the next person, but the latest generation of EPP goes far beyond blocking malicious files with signatures as legacy AV has always done.
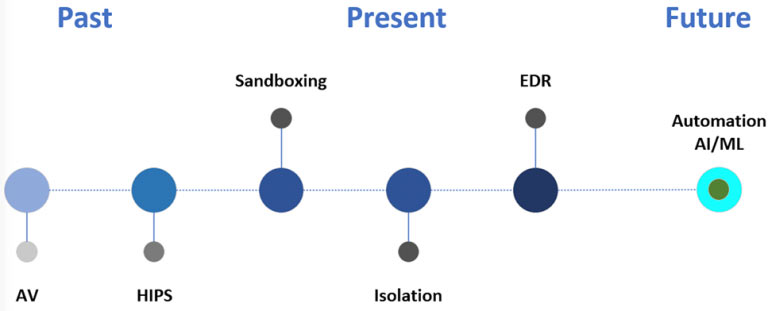
In the contextual diagram shown below, you can see where we have been and where we are going with endpoint security.
EPP, however, goes much further and utilizes certain models to predict when a file, or perhaps fileless code, will attempt to execute something malicious without ever having seen it before (such as a zero-day vulnerability). This is powerful tech!
Benefits of EPP
EPP’s capabilities shine compared to standalone antivirus solutions. Here is the shortlist of capabilities the top tools are packing today:
- Malicious static file detection
- Dynamic fileless analysis & prevention
- Behavioral analysis and machine learning model detection
- Investigation tools for alerts
No EPP is 100% accurate at blocking malicious actions, though. Even with a 99% block rate, the need for endpoint detection & response becomes more apparent. Which leads to the next point: EDR.
Endpoint Detection & Response (EDR)
What is EDR? Endpoint Detection & Response extends the utility of EPP by using models to detect when something malicious has already executed on an endpoint. EDR then provides notifications, visibility, and remediation as malicious actions are identified posthaste.
EDR architecture compensates for EPP’s inability to fully prevent malicious behaviors or actions. EDR services help with threat detection by identifying those threats that can’t be stopped by EPPs.
Benefits of EDR
There are additional features available to a security team when utilizing EDR solutions, such as:
- Threat hunting;
- Ransomware rollback;
- Improved visibility; and
- Dwell time reduction
Not to mention EDR solutions provide a single source of truth for all endpoint actions and analyses for perceived and detected malicious activity. EDR improves your ability to effectively mitigate any malicious activity that bypasses all other security mechanisms on the endpoint.
MDR
The final piece in the puzzle is arguably the most important. Managed Detection and Response (MDR) is a strategic opportunity to co-manage your security posture and incident response. MDR extends your team’s capabilities by expediting reaction time to malicious events in your environment.
A managed endpoint security solution encourages your organization’s security team members to focus on the highest-value work in their roles. This is accomplished by using the best co-managed resources to suppress alert fatigue and effectively orchestrate responses to identified malicious behaviors.
Benefits of MDR
A lofty goal, to be sure, which is why you should consider some requirements when looking at an MDR service’s provisions:
- Stops breaches
- Reduces dwell time
- 100% transparency of events, actions, and access
- Resolves every alert – that means Every. Single. One.
- Mobile application to resolve alerts (e.g. containment and isolation actions)
- Highly trained SOC (Security Operations Center) analysts
CRITICALSTART Offers Advanced MDR Solutions
CRITICALSTART provides architectural guidance in endpoint security and MDR (managed detection and response) services to customers.
For guidance, roadmaps, architecture discussions, or MDR questions please send us a message or call 877-684-2077 to speak to one of our cybersecurity experts!
Mitchem Boles | CISSP, Senior Security Architect at CRITICALSTART
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
