Critical Start Cyber Risk Peer Insights – Strategy vs. Execution
Effective cyber risk management is more crucial than ever for organizations across all industries. Cyber risk peer benchmarking provides valuable insights into how organizations are performing in terms of their risk management strategies and execution. In this post—the first of an ongoing series—we’ll look at the findings of our latest peer benchmarks and explore the gap between strategy and execution in reducing cyber risk.
What is Cyber Risk Peer Benchmarking?
Cyber risk peer benchmarking is the process of comparing an organization’s cyber risk management practices against those of similar organizations within the same industry or sector. This comparison helps identify strengths and weaknesses across the tools, strategies, and processes that an organization uses to secure their assets. By understanding how they measure up against their peers, organizations can make data-driven decisions to reduce cyber risk.
Recommended Reading | Critical Start Cyber Risk Landscape Peer Report
The Importance of Peer Benchmarking
Organizations face navigating numerous cyber threats while ensuring their risk management strategies keep pace with industry standards. This is where peer benchmarking emerges as a vital tool, providing valuable insights that business and technical leaders can use to optimize their resources, defend budget requests, and prioritize strategic improvements.
Peer benchmarking is essential for:
- Identifying best practices: By studying the successful strategies employed by top-performing peers, organizations can adopt and adapt these practices to bolster their own cyber risk management.
- Pinpointing weaknesses: Benchmarking highlights areas where an organization may be lagging its peers, enabling targeted improvements to close these gaps.
- Justifying investments: Benchmarking data can be used to support the case for increased investments in cybersecurity initiatives, as it demonstrates the need to keep pace with industry standards.
Strategy vs. Execution: Key Findings
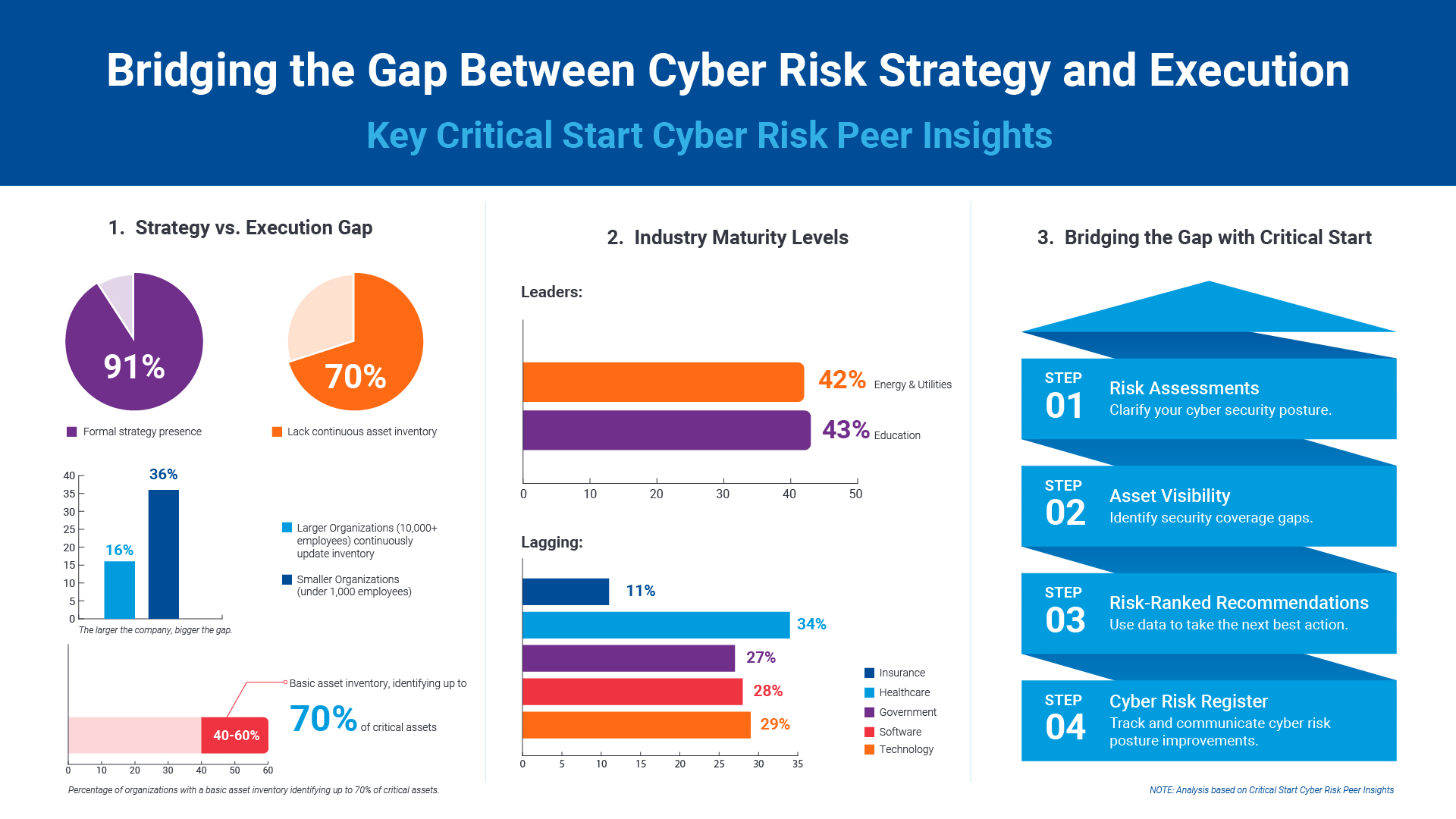
The latest peer insights unveil a striking dichotomy between strategy and execution in cyber risk management. While most organizations acknowledge the criticality of having a robust risk management strategy, the execution of these strategies often falls short. And a surprisingly high percentage of organizations lack continuous asset inventory, leaving them vulnerable to threats targeting unknown and unprotected assets.
This gap between strategy and execution widens as organizations grow larger. Furthermore, even among organizations maintaining basic asset inventories through manual processes or tools, only up to 70% of critical assets are identified.
Strong on Strategy:
- 91% of organizations report having a formal risk management strategy in place for most or all functions, indicating a widespread recognition of the importance of cyber risk management.
Weak on Execution:
- Nearly 70% of organizations lack continuous asset inventory, making it challenging to protect what they have (but don’t know they have).
- Larger organizations tend to have less awareness of their IT assets:
- Only 16% of organizations with over 10,000 people update their asset inventory continuously using formal inventory management tools, compared to 36% of organizations under 1,000 people.
- Between 40% and 60% of organizations maintain a basic asset inventory using manual processes or tools, but only up to 70% of critical assets are identified, leaving significant visibility gaps that attackers can exploit.
Report after report, and study after study, shows that many attacks are successful because network owners did not know their enterprise assets, the software they had running and where their critical data was.
Center for Internet Security (CIS)
Industry-Specific Findings
We found significant disparities in asset inventory management across various industries, with some sectors demonstrating higher maturity levels than others. Some highly regulated industries, such as Energy & Utilities and Education, lead the pack in maintaining continuous and formal inventories. However, other regulated sectors, including Insurance, Healthcare, and Government, exhibit lower maturity levels in this crucial aspect of cyber risk management. Surprisingly, even Software and Technology organizations struggle to maintain comprehensive asset inventories.
- Highly regulated industries like Energy & Utilities (42%) and Education (43%) maintain continuous, formal inventories with over 70% of critical assets identified and tracked.
- Other regulated industries, such as Insurance (11%), Healthcare (34%), and Government (27%), have lower maturity levels in asset inventory management.
- Software (28%) and Technology (29%) organizations also struggle with maintaining comprehensive asset inventories, potentially leading to weak links in the vendor supply chain, as highlighted by the new focus on supply chain governance in the National Institute of Standards and Technology Cybersecurity Framework 2.0 (NIST CSF 2.0).
Bridging the Gap with Critical Start
To effectively reduce cyber risk, organizations must bridge the gap between strategy and execution. Critical Start offers a comprehensive solution to help organizations achieve this by:
- Maintaining a strong strategy with Risk Assessments: Our guided assessments leverage peer benchmarking to help organizations develop and refine their cyber risk management strategies.
- Knowing what you have and what’s at risk with Asset Visibility and Cyber Risk Register: Our tools provide continuous asset discovery and visibility, enabling organizations to identify and prioritize their critical assets.
- Executing on continuous improvement with Risk-Ranked Recommendations: Our platform delivers actionable, risk-ranked recommendations to guide organizations in effectively allocating resources and implementing controls to reduce cyber risk.
Yes, organizations have made strides in developing cyber risk strategies, but execution remains a challenge. By leveraging peer benchmarking insights and partnering with Critical Start, organizations can bridge the gap between strategy and execution, ultimately strengthening their cyber resilience. Start with a Quick Start Risk Assessment and compare your organization’s security against peer benchmark insights presented in this series.
Download a copy of our “Bridging the Gap Between Cyber Risk Strategy and Execution” infographic here.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
