Cloud – Evolution of Malicious Traffic Concealment

Critical Start Cyber Research Unit (CRU) predicts the concealment of malicious traffic within cloud storage platforms, while not a new concept, is poised for further innovation. Critical Start anticipates that threat actors will escalate their use of popular cloud platforms to obscure their malevolent actions. This approach not only bolsters their data theft efficiency but also serves to undermine established security mechanisms and defenses.
Cloud – The Evolution of Malicious Traffic Concealment
The widespread adoption of cloud computing, with up to 94% of enterprises utilizing cloud services, has prompted a shift in organizational security paradigms. Instead of focusing solely on securing the perimeter of local databases, the contemporary cloud-first approach emphasizes the protection of data itself. This shift has propelled adversaries to adopt a highly sophisticated strategy—the covert concealment of malicious traffic within cloud environments. This evolutionary shift represents a profound transformation in the tactics, techniques, and procedures employed by threat actors. As organizations pivot towards the cloud for increased flexibility and scalability, cyber adversaries deftly exploit the inherent complexities, presenting a formidable challenge to traditional security paradigms.
Traditional cybersecurity measures, effective in more static environments, grapple with the novel challenges presented by the expansive and dynamic nature of cloud ecosystems. Malicious actors leverage the intricacies of cloud computing to obfuscate their activities, compelling cybersecurity professionals to reassess and recalibrate defense strategies. Recent reports revealing a staggering 1,400% surge in fileless attacks exploiting cloud vulnerabilities underscore the urgency of adapting to the evolving threat landscape. Insights derived from the analysis of 700,000 real-world attacks, particularly focusing on software supply chains, risk postures, and runtime protection, shed light on the intricacies of contemporary cyber threats.
A noteworthy trend is the significant investment by threat actors in concealing their campaigns, with over 50% of attacks prioritizing defense evasion. These evasion techniques encompass various strategies such as masquerading, obfuscated files, and the utilization of memory resident malware. The illustrative case of the “HeadCrab” campaign serves as a compelling example of adversaries’ proficiency in evading agentless technology. This campaign, detected in early 2023, showcases the limitations of relying solely on agentless defenses, accentuating the indispensable role of agent-based runtime security in countering such evasive maneuvers.
Key Trends
In the realm of cybersecurity, malicious actors are continually finding innovative ways to exploit legitimate web services, making it increasingly challenging for defenders to detect and prevent cyber threats. Recent analysis revealed that at least a quarter of more than 400 malware families studied over the past two years have leveraged legitimate internet services in some way. This strategic abuse allows cybercriminals to blend in with normal traffic, complicating defense efforts.
- Abused Services: Cloud storage platforms are the most abused legitimate services, followed by messaging apps, email services, and social media. Among these, Pastebin, Google Drive, and Dropbox lead the list.
- Messaging Apps: Telegram is identified as the most commonly abused service, followed by Discord. Both services are challenging to block due to their widespread use in both victim environments and the cybercriminal underground.
- Infostealers: Infostealers, designed to discreetly gather login credentials and personal information, stand out in their abuse of legitimate services. Approximately 37% of observed infostealer malware families abused such services, emphasizing their significance in the evolving cybercrime ecosystem.
Anticipating the Expanding Trend in Legitimate Internet Services (LIS) Abuse
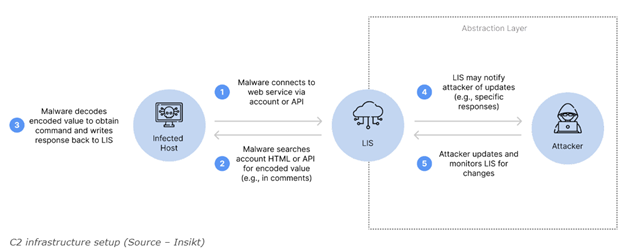
LIS abuse refers to the malicious use of trusted and widely used internet services to conceal or carry out illicit activities by threat actors. Instead of relying on obscure or suspicious channels, hackers exploit well-known and legitimate platforms to hide their malicious traffic, making it more challenging for security systems to detect and block their activities.
The concept of LIS abuse involves leveraging popular internet services, such as cloud storage platforms, messaging applications, or other widely used services, to facilitate various cyber threats. Some common examples include using cloud storage platforms like Google Drive or OneDrive to store and transfer malicious files or utilizing messaging apps like Telegram or Discord to coordinate and communicate during cyber-attacks.
Initial Access Trends
- Phishing Attacks: One prevalent method involves phishing campaigns where attackers trick individuals into providing their credentials or downloading malicious files. For example, an email may contain a link that directs users to a seemingly legitimate login page for a LIS such as Google Drive. Upon entering their credentials, users unwittingly provide access to the attackers.
- Malicious Email Attachments: Attackers may send emails with seemingly harmless attachments that, when opened, execute malicious code or initiate a download from a LIS. This can be a document, spreadsheet, or other file types that are commonly associated with LIS platforms.
- Credential Theft: If attackers manage to compromise credentials through methods like credential stuffing (using previously leaked usernames and passwords) or utilizing keyloggers, they can gain unauthorized access to LIS accounts.
- Exploiting Software Vulnerabilities: Some attacks involve exploiting vulnerabilities in the software or applications associated with LIS. This could be achieved through the use of malware that takes advantage of known vulnerabilities, enabling the attacker to gain control over the system.
- Compromised Third-Party Integrations: Many LIS platforms offer third-party integrations or APIs. If a third-party service connected to a LIS is compromised, attackers may gain access to the LIS by exploiting the compromised integration.
Once initial access is achieved, threat actors can use the LIS environment as a staging ground for various activities, such as concealing malicious traffic, hosting malicious files, or conducting further attacks within the compromised network. It’s essential for organizations to implement robust security measures, including multi-factor authentication, regular security awareness training, and monitoring for suspicious activities, to mitigate the risks associated with malicious activities in LIS.
Concealing Malicious Traffic
- Encryption: Malicious actors often encrypt their communication to make it more challenging for security systems to inspect the content. By using protocols like HTTPS, attackers can mask the nature of the traffic, making it appear as normal, secure web traffic.
- Steganography: This technique involves hiding malicious content within seemingly innocuous files or data. For instance, malware may be concealed within image files, documents, or other files transferred through LIS. This allows attackers to evade detection, as the hidden payload is not immediately apparent.
- Traffic Obfuscation: Threat actors may obfuscate their communication patterns to mimic legitimate traffic behavior. This can include using random or variable time intervals between communications, changing communication protocols dynamically, or employing other evasion techniques to avoid detection.
- Abuse of Trusted Services: Attackers leverage trusted LIS platforms to host and transmit malicious content. For example, they might use file-sharing services to store and distribute malware, or they could abuse messaging apps for command and control communication.
- IoC (Indicators of Compromise) Variation: To bypass traditional detection mechanisms, threat actors may alter the indicators of compromise regularly. This includes changing IP addresses, domains, or other identifiers associated with malicious activities.
- Blend with Normal User Activity: Malicious actors often mimic the behavior of legitimate users within LIS environments to avoid raising suspicions. For example, they might perform activities that typical users engage in, such as accessing shared files or collaborating on documents.
- Dynamic Infrastructure: Utilizing dynamic infrastructure involves rapidly changing the infrastructure used for malicious activities. This can include frequently shifting between different servers, domains, or IP addresses, making it difficult for security systems to keep up.
- Multi-Stage Attacks: Attackers may split their malicious activities into multiple stages, with each stage appearing as benign. This makes it harder for security systems to link the various stages and identify the overall malicious intent.
Real World Examples
Storm-1133 is an active threat group that has been systematically targeting Israeli private-sector entities, specifically within the energy, defense, and telecommunications sectors. This group’s activities primarily focus on organizations deemed hostile to Hamas, including those in Israeli energy and defense, as well as entities loyal to Fatah, a major Palestinian political faction in the West Bank. Notably, this group has also attempted to compromise third-party organizations with known links to Israeli targets of interest. Employing innovative evasion tactics, Storm-1133 utilizes tailored phishing messages through social media, deploys various backdoors, and employs dynamic updates to their command-and-control infrastructure hosted on Google Drive. Additionally, they have created deceptive LinkedIn profiles impersonating Israeli HR managers, project coordinators, and software developers to conduct reconnaissance and deliver malware to employees within Israeli defense, space, and technology organizations during 2023.
The LABRAT campaign was a sophisticated and financially motivated cyber operation known for its emphasis on stealth and defense evasion techniques. Employing undetected compiled binaries in Go and .NET, signature-based tool evasion, cross-platform malware, and kernel-based rootkits, the attackers effectively concealed their presence. The campaign exploited vulnerabilities such as the GitLab CVE-2021-22205 for initial access, utilizing private GitLab repositories, obfuscated cryptographic material, and a sophisticated Linux Loadable Kernel Module (LKM) to hide the mining process and avoid detection. LABRAT’s main objectives involved cryptomining and Russian-affiliated proxyjacking, using TryCloudFlare to obscure the Command and Control (C2) network. The attackers consistently updated their tools, making detection challenging and underscoring the need for defenders to focus on identifying tactics, techniques, and procedures (TTPs) while keeping indicators of compromise (IoCs) updated.
The SCARLETEEL operation showcased a highly sophisticated cyber-attack within a client’s cloud infrastructure. The assailants demonstrated advanced proficiency in exploiting Kubernetes container vulnerabilities and AWS accounts, with objectives extending beyond cryptomining to include the theft of proprietary software and data. Commencing with the compromise of a vulnerable pod in a self-managed Kubernetes cluster within an AWS cloud account, the attackers employed cryptomining as a distraction. Through the exploitation of the Instance Metadata Service (IMDS) v1, they acquired temporary credentials, enabling lateral movement within the AWS environment. The operation featured strategic tactics, including the creation of new users, groups, and access keys, coupled with the disabling of CloudTrail logs to evade detection. Subsequently, the attackers targeted AWS services, achieving significant data exfiltration from Lambda functions and S3 buckets, encompassing proprietary code, software, and logging files. As a defense evasion measure, they disabled CloudTrail logs and extracted IAM credentials from Terraform state files, showcasing a comprehensive and sophisticated cyber-attack methodology.
These campaigns underscore the severe financial and operational consequences of cloud security breaches. The financial motivation behind attacks, exemplified by operations like LABRAT and SCARLETEEL, further emphasizes the critical need for robust security measures in cloud environments. The financial losses, damage to reputation, and legal repercussions resulting from these attacks underscore the imperative for effective risk mitigation strategies.
By abusing legitimate services, threat actors aim to blend in with normal internet traffic, making it difficult for traditional security measures to distinguish between legitimate and malicious activities. This approach allows cybercriminals to operate under the radar, evading detection and complicating the efforts of cybersecurity professionals to identify and mitigate potential threats.
Challenges and Strategies for the Future Defense
The ever-changing landscape of threat tactics challenges the traditional approaches to defense. To effectively safeguard against these evolving threats, organizations must incorporate multifaceted elements into their defense strategies:
Multi-Method Approach: To counter these evolving threats, organizations are advised to adopt a multi-method approach encompassing network, file, and log detection. Understanding the context of service usage is paramount for establishing a lasting and effective security posture. Threat analysts recommend enhancing nuanced detection capabilities to discern subtle indicators of malicious activity, thereby staying ahead of the adversaries.
Proactive Internet Service Assessment: Proactive measures, such as continuous Internet service assessment, are essential components of a robust defense strategy. This involves actively monitoring and assessing Internet services to identify potential anomalies and unauthorized activities. By staying proactive, organizations can better understand the evolving tactics of threat actors and preemptively address potential security risks.
Attack Simulations: The evolution of malicious traffic concealment necessitates a proactive and adaptive approach to security. Security teams are encouraged to deploy attack simulations that replicate real-world scenarios. These simulations help organizations identify vulnerabilities and weaknesses in their security posture, enabling them to fine-tune their defenses and respond effectively to emerging threats.
Future Targets
Within the realm of cloud platforms, notable findings point to Google Drive and OneDrive as the primary targets of abuse by malicious actors. These platforms, widely acclaimed for their user-friendly and collaborative features, have unfortunately become breeding grounds for illicit activities orchestrated by cyber threats. The exploitation of these cloud services allows threat actors to operate discreetly, leveraging the inherent trust associated with such widely used platforms. By camouflaging their malicious activities within the seemingly benign environment of Google Drive and OneDrive, cyber adversaries gain a tactical advantage, effectively concealing their operations amidst the vast sea of legitimate user interactions.
Messaging applications, particularly Telegram and Discord, also find themselves in the crosshairs of frequent exploitation by threat actors. These widely adopted communication channels, celebrated for their ease of use and real-time interaction capabilities, inadvertently become conduits for malicious intent. Cyber adversaries recognize the prevalence of these messaging apps and exploit their popularity to facilitate covert communication, coordination, and data exchange without raising undue suspicion.
Conclusion
The escalating focus of threat actors on the cloud represents a significant trend in cybersecurity. Similar to historical shifts in malware targeting, such as the transition from Windows to Linux, threat actors are adapting strategies to exploit vulnerabilities in the cloud environment. The cloud’s appeal lies in its ubiquity, scalability, and the potential for discreet movement within its distributed infrastructure. This tend could lead threat actors to primarily focus on third-party cloud service providers, posing a unique challenge to organizations due to the interconnected nature of the cloud ecosystem. As the cloud becomes integral to organizational IT infrastructures, concealing malicious traffic within it becomes a critical concern, necessitating innovative solutions.
Cybersecurity professionals must proactively leverage advanced technologies aligned with the dynamic nature of the cloud. Continuous enhancement of capabilities and collaborative efforts within the cybersecurity community are crucial to developing robust defenses against evolving cyber threats in the cloud era. Recommendations emphasize the need for a strategic and multi-faceted defense approach, including understanding service contexts, enhancing detection capabilities, and deploying proactive measures. Organizations should adopt network, file, and log detection methods for a comprehensive security shield, with regular assessments and attack simulations to identify vulnerabilities before exploitation by threat actors.
References:
- https://www.networkworld.com/article/3708635/gartner-top-strategic-technology-trends-for-2024.html#tk.rss_security
- https://gbhackers.com/cyber-criminals-hide-malicious-traffic/
- https://www.darkreading.com/cloud/the-need-for-speed-when-cloud-attacks-take-only-10-minutes
- https://www.helpnetsecurity.com/2023/08/22/kennedy-torkura-mitigant-cloud-security-mechanisms/
- https://www.csoonline.com/article/643356/fileless-attacks-surge-as-cybercriminals-evade-cloud-security-defenses.html
- https://cyberscoop.com/hackers-hiding-cloud-services-malware/
- https://www.cshub.com/attacks/news/iotw-everything-we-know-about-the-medibank-data-leak#:~:text=The%20initial%20cyber%20security%20incident,been%20accessed%E2%80%9D%20during%20the%20breach.
- https://sysdig.com/blog/labrat-cryptojacking-proxyjacking-campaign/
- https://sysdig.com/blog/cloud-breach-terraform-data-theft/
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
