[2020 Updates] Gartner Endpoint Security Hype Cycle Insights

Gartner recently released their 2020 Hype Cycle for Endpoint Security, and the focus is crucial to the security defense, successful implementation, and daily operation of businesses everywhere, especially now.
Cybersecurity practitioners realize the spotlight is squarely on the endpoint, as it should be, for enterprise security leaders asked to pull a rabbit out of their hat.
The rabbit, in this case, is the business requirement for any user to access a litany of applications, over any network, from any connected device, while ensuring a stellar user experience.
Sound familiar to my fellow cyber defenders?
What Is Gartner’s Hype Cycle?
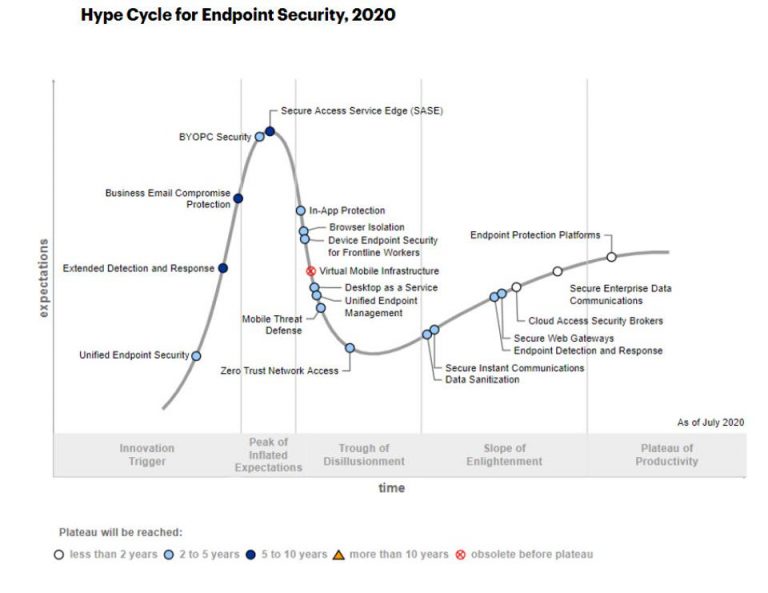
Gartner’s Hype Cycle, seen in the figure below, shows the various stages that security leaders walkthrough in the midst of enterprise tool implementation, in this case specifically around endpoint security.
Five Phases of the Hype Cycle
Hype cycles highlight five main phases that new technology goes through as it matures. These phases are:
- Innovation trigger
- Peak of inflated expectations
- Trough of disillusionment
- Slope of enlightenment
- Plateau of productivity
What’s New in 2020
Gartner’s five additions to its hype cycle are critical to understanding where the highest value of protection can secure the value of enterprises worldwide. Those additions are:
- Unified Endpoint Security (UES);
- Extended Detection & Response (XDR);
- Bring Your Own PC (BYOPC);
- Business Email Compromise Protection (BEC);
- and Secure Access Service Edge (SASE).
The swift surge in remote work highlights the necessity to prioritize and implement more unified and streamlined tools, combining correlative data from multiple sources with the following recommendations.
Unified Endpoint Security (UES)
Unified endpoint security includes EPP and EDR for ALL endpoints (including assets, mobile, and cloud) with aggregated mature protection along with advanced response capabilities in the platforms to consolidate security effectiveness.
A byproduct may be that this consolidates vendor selection as well from the business, GRC (governance, risk management, and compliance), and financial perspective.
Extended Detection & Response (XDR)
XDR is specified as vendor-specific threat detection and incident response tools unifying multiple security products into a system of sorts.
CRITICALSTART‘s view is that Managed Detection & Response (MDR) platforms that offer aggregation of multiple tools, including SIEM, can offer the same definition but result in the resolution of EVERY alert across those toolsets to secure environments efficiently.
Business Email Compromise Protection (BEC)
Business email compromise involves an attacker fraudulently accessing a business email account to act as a representative of the company.
Malicious actors effectively attack users with well-informed, specific victim knowledge to impersonate other businesses, direct funds or data maliciously, or acquire a victim’s legitimate credentials.
These are often hard to detect because of the lack of malicious attachments or links. Instead, these attacks rely on social engineering to produce valid fund transfers to the attackers or gain access to legitimate credentials.
Enterprises must deal with this top priority attack vector with email protection systems and add-ons that effectively limit the risk of BEC.
Bring Your Own PC (BYOPC) Security
BYOPC security returns to the list this year because of the noted 100% increase in personal devices used to access corporate applications, data, and/or assets.
This is an enormous, immediate area of concern. But CRITICALSTART sees tools like cloud access security brokers (CASBs), EDR, Zero-Trust (including identity infrastructure), and secure email gateways (SEGs) to counter this unfortunate gap.
The primary recommendation is providing secured, corporate-owned devices to accordingly operate with your enterprise security tools and necessary policies.
Secure Access Service Edge (SASE)
SASE is a term minted by Gartner that includes multiple service capabilities, i.e. SD-WAN, CASB, SWG, NGFW, etc.
This is cloud-delivered security as a service that supports remote worker access along with branch offices (both of which are notoriously hard to secure with a full suite of protections).
Writing for Forbes, Louis Columbus notes that “by 2024, at least 40% of enterprises will have strategies for adopting Secure Access Service Edge (SASE) up from less than 1% at year-end 2018.”
Usually, SASE would be included as part of a digital transformation where cloud services are adopted and formally implemented to use the “new edge” flexibility and security across sprawled assets and people.
We have fantastic implementation assistance and partners to help you integrate and/or deploy SASE.
Enterprise Direction, Focus, and Priorities
In a previous article, I wrote about the importance of protecting the now-surged, remote workforce.
SMB and enterprise security administrators and leaders alike would agree with the necessity for cloud adoption at the forefront and their employees’ desire to access data and files anywhere.
At the same time, the proliferation of malicious attacks such as phishing, ransomware, and fileless malware has been well-documented.
This increased attack surface correlates to enormous impacts on organizations in seemingly every sector (i.e. healthcare), not to mention government entities, and even countries as a whole across the world (think New Zealand).
Which brings me back to the point: Endpoints are the single common thread for malicious attack detonation (even if received by victims in many ways).
To that end, Gartner’s additions to the 2020 endpoint security hype cycle are apt and clearly needed.
How We Can Help
CRITICALSTART‘s complementary focus is providing a unified approach to architecture, tools, and processes enterprises need to reduce risk and secure the business.
We provide these services through the Field CISO team with decades of experience amongst each member and proven security program implementation experience for some of the largest organizations in the U.S.
CRITICALSTART also offers a unique, best-in-class managed detection & response (MDR) service that uses EDR and/or SIEM data, among other data points, dialed up to 11, to truly resolve every alert so that the enterprise doesn’t accept risk.
RESOURCE CATEGORIES
- Buyer's Guides(1)
- Consumer Education(39)
- Consumer Stories(2)
- Cybersecurity Consulting(4)
- Data Breaches(15)
- Data Privacy(43)
- Incident Response(2)
- Interview(51)
- MDR Services(59)
- MobileSOC(6)
- News(5)
- Press Release(101)
- Research Report(9)
- Security Assessments(2)
- Thought Leadership(19)
- Threat Hunting(3)
- Video(1)
- Vulnerability Disclosure(1)
